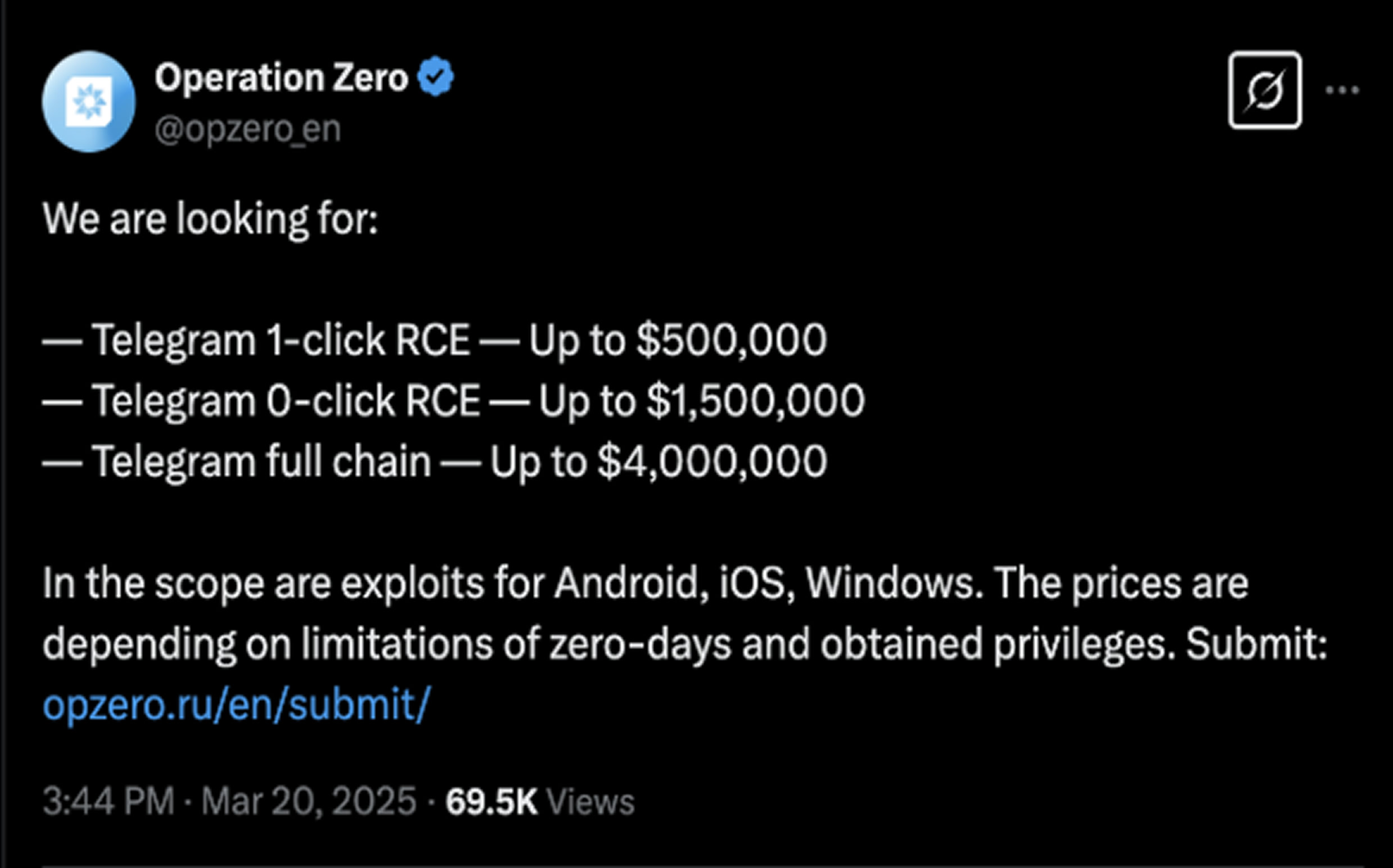
A Russian exploit brokerage firm, Operation Zero, has publicly offered bounties of up to $4 million
for zero-day vulnerabilities in Telegram, highlighting growing state-sponsored efforts to compromise the widely used messaging platform.
The firm, which exclusively provides services to the Russian government and domestic entities, is specifically looking for remote code execution (RCE) exploits targeting Telegram on Android, iOS, and Windows. The reward amounts vary depending on the complexity and effectiveness of the exploit.
Exploit Pricing and Targets
Operation Zero’s tiered pricing model includes:
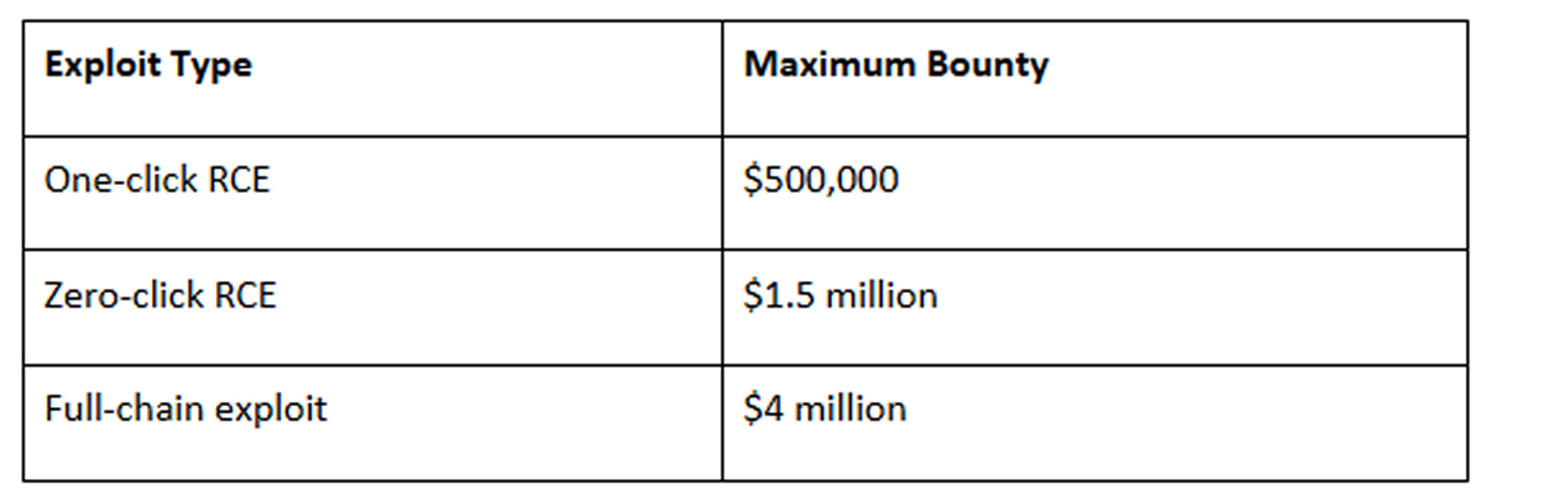
The “full-chain” category refers to multi-stage exploits granting access to a device’s operating system after the initial Telegram compromise.
Industry Insights on Exploit Pricing and Telegram’s Security Challenges
Industry sources suggest these prices may be below market value, as brokers typically resell exploits to governments at 2–3 times their acquisition cost.
Telegram’s encryption and file-handling mechanisms have repeatedly come under scrutiny:
- Android: A July 2024 “EvilVideo” zero-day exploit allowed attackers to disguise malicious APKs as videos, leveraging Telegram’s auto-download feature. Though patched in version 10.14.5, the flaw required user interaction, exposing risks in default settings.
- Windows: A 2024 vulnerability caused by a typo mislabeling “.pyzw” files enabled unauthorized Python script execution. Telegram later mitigated this by appending “.untrusted” to suspicious files.
- Historical Issues: Past vulnerabilities include a 2017 Unicode exploit that facilitated cryptomining malware distribution via disguised files.
Security experts highlight that Telegram’s encryption lags behind Signal and WhatsApp, as its default chats lack end-to-end protection and rely on non-audited protocols. These weaknesses, combined with its 1 billion+ user base—particularly in Russia and Ukraine—make Telegram a prime target for state-sponsored actors.
Operation Zero’s Bounty Reveals Russia’s Cyber Priorities Amid Telegram Ban
Operation Zero’s public bounty provides a rare glimpse into Russia’s exploit procurement strategy, following Ukraine’s 2024 ban on Telegram for government devices due to infiltration concerns from Russian hackers.
Industry experts suggest the bounty signals an urgent need for surveillance or cyberwarfare tools within Russian agencies. While Operation Zero claims exclusivity to Russian clients, underground forums indicate a broader exploit trade. The “” vulnerability, for instance, surfaced on Russian hacking forums in June 2024 before being patched, highlighting the overlap between state-sponsored and criminal exploit markets.
As zero-day brokers like Operation Zero drive a $12 billion global surveillance industry, Telegram remains a key target due to its cross-platform reach. Users are advised to disable auto-downloads, enable encryption manually, and keep apps updated.
Found this article interesting? Follow us on X(Twitter) and Instagram to read more exclusive content we post.


