Researchers from the CISPA Helmholtz Center for Information Security in Germany have disclosed a newly uncovered hardware vulnerability that impacts AMD processors. The flaw—dubbed StackWarp—enables an attacker with privileged access to a host server to execute malicious code inside confidential virtual machines (CVMs), effectively breaking the security assurances provided by AMD Secure Encrypted Virtualization with Secure Nested Paging (SEV‑SNP). The issue affects AMD Zen 1 through Zen 5 CPU generations.
“In SEV‑SNP environments, this vulnerability allows a malicious VM host to alter the stack pointer of a guest virtual machine,” wrote researchers Ruiyi Zhang, Tristan Hornetz, Daniel Weber, Fabian Thomas, and Michael Schwarz. “This manipulation enables an attacker to take over both control flow and data flow, resulting in remote code execution and privilege escalation within a confidential VM.”
AMD has categorized the issue as CVE‑2025‑29943 (CVSS v4 score: 4.6), describing it as a medium‑severity improper access control weakness. According to the company, an attacker with administrator‑level privileges could modify CPU pipeline configuration, corrupting the stack pointer inside an SEV‑SNP‑protected VM.
The vulnerability affects the following AMD product lines:
- EPYC 7003 Series
- EPYC 8004 Series
- EPYC 9004 Series
- EPYC 9005 Series
- EPYC Embedded 7003 Series
- EPYC Embedded 8004 Series
- EPYC Embedded 9004 Series
- EPYC Embedded 9005 Series
SEV is intended to safeguard VM memory from hypervisor access, but CISPA’s findings show that this barrier can be bypassed without accessing plaintext VM memory. Instead, the exploit targets an internal microarchitectural component called the stack engine, which accelerates stack-related operations.
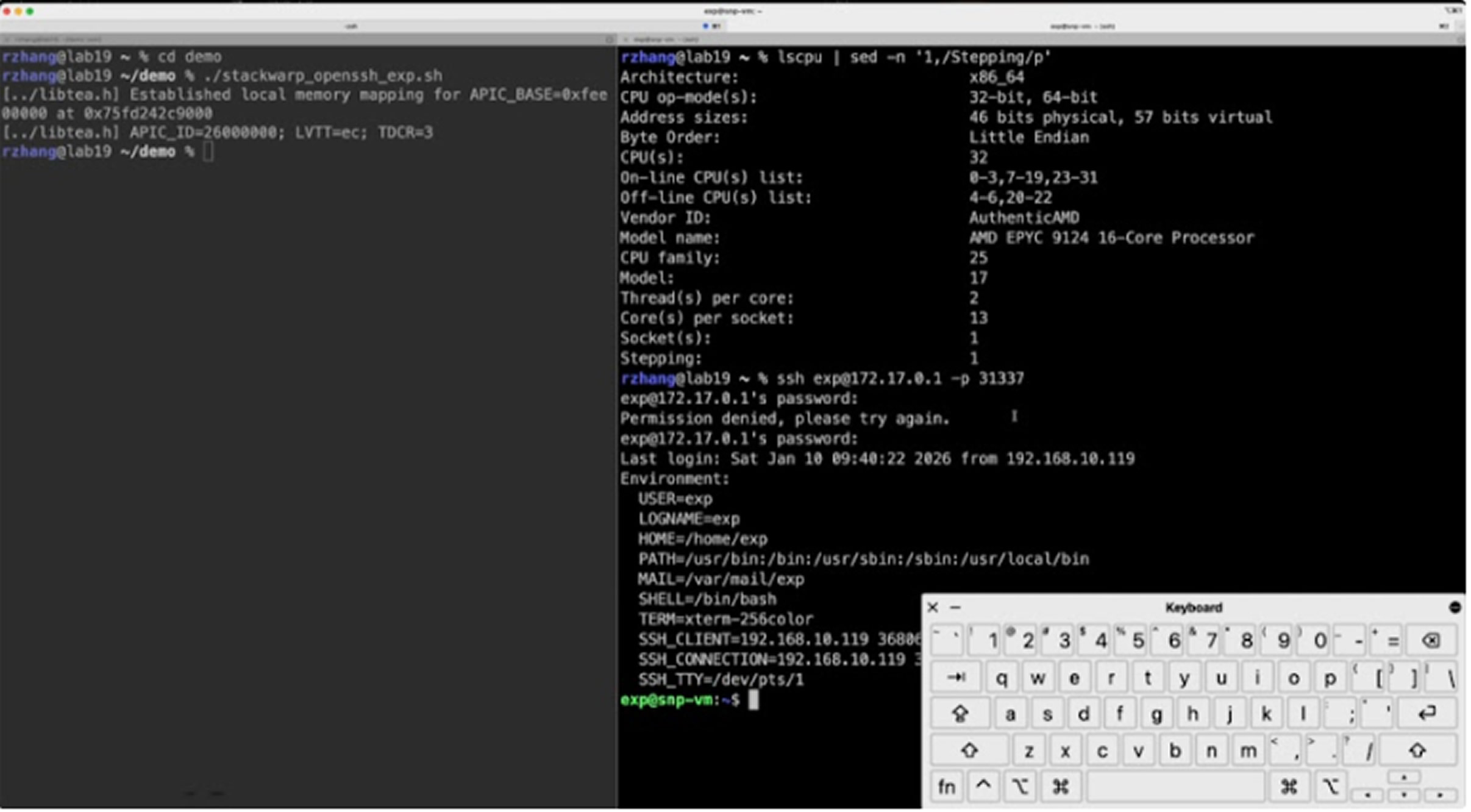
“The exploit relies on a previously undocumented hypervisor‑level control bit,” Zhang explained in a statement shared with The Hacker News. “By running a hyperthread in parallel with the victim VM, an attacker can influence the position of the stack pointer inside the protected VM.”
This capability allows attackers to redirect program execution or manipulate critical data. The StackWarp attack can leak sensitive information from SEV‑protected workloads and compromise virtual machines running in AMD-based cloud environments. Notably, researchers demonstrated the ability to extract an RSA‑2048 private key from a single faulty signature, bypass OpenSSH password authentication and sudo prompts, and achieve kernel‑level code execution inside a VM. AMD shipped microcode patches addressing the issue in July and October 2025, with additional AGESA updates for EPYC Embedded 8004 and 9004 processors planned for April 2026.
The discovery builds on earlier CISPA research into CacheWarp (CVE‑2023‑20592), a software-based fault attack against SEV‑SNP that allowed control‑flow hijacking, VM compromise, and privilege escalation. Both StackWarp and CacheWarp fall under hardware architectural attack vectors.
“For operators of SEV‑SNP systems, several protective steps are recommended,” Zhang said. “First, determine whether hyperthreading is enabled on affected machines. If so, consider temporarily disabling it for CVMs that have strict integrity requirements. Additionally, administrators should apply all available microcode and firmware updates. StackWarp is yet another example of how subtle hardware-level behaviors can undermine higher-level security guarantees.”
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



