Ukrainian and German law enforcement agencies have identified two Ukrainian nationals suspected of collaborating with Black Basta, a ransomware‑as‑a‑service (RaaS) operation linked to Russia.
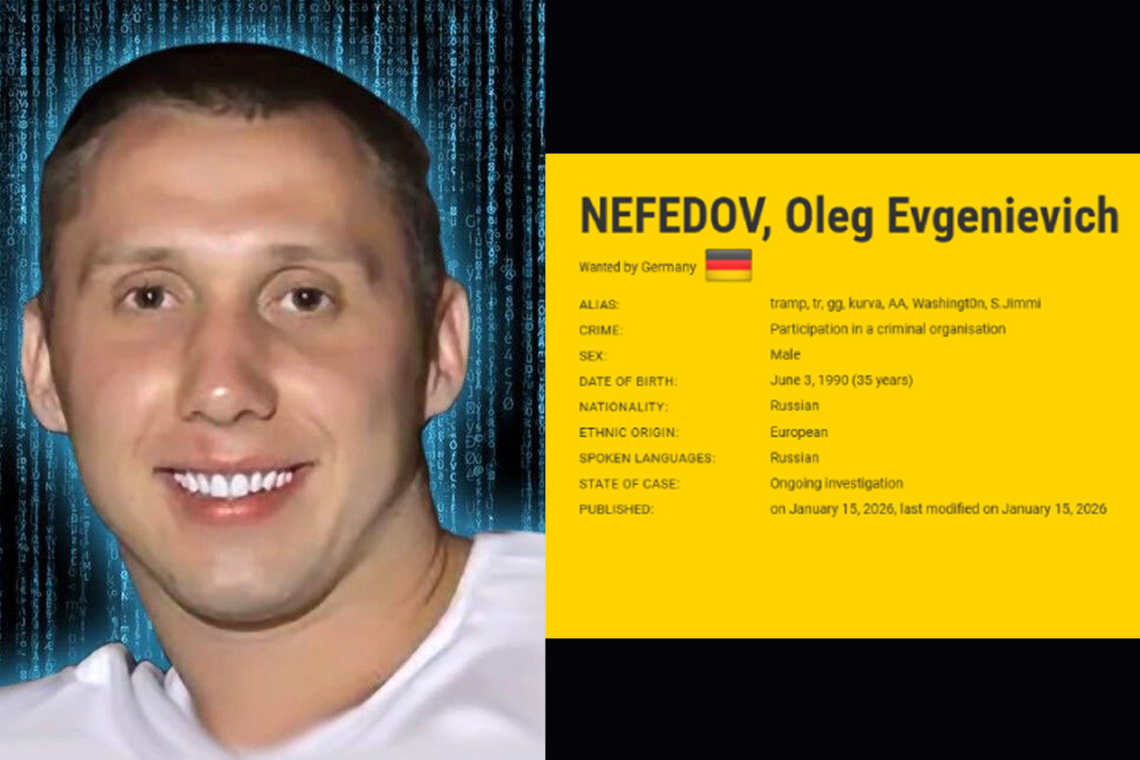
Authorities also stated that the group’s suspected leader, 35‑year‑old Russian citizen Oleg Evgenievich Nefedov (Нефедов Олег Евгеньевич), has now been placed on both the European Union’s Most Wanted list and INTERPOL’s Red Notice list.
“The investigation revealed that the suspects specialized in technically compromising secure systems and helped prepare ransomware‑based cyberattacks,” Ukraine’s Cyber Police announced.
According to officials, the individuals acted as “hash crackers,” experts who extract passwords from information systems using specialized tools. Once credentials were captured, the ransomware group used them to infiltrate corporate networks, deploy ransomware, and demand payment in exchange for decrypting the locked data.
Searches carried out at the suspects’ homes in Ivano‑Frankivsk and Lviv resulted in the seizure of digital storage devices and cryptocurrency assets.
Black Basta became active in April 2022 and has reportedly attacked more than 500 organizations across Europe, North America, and Australia. The group is believed to have generated hundreds of millions of dollars in illicit cryptocurrency payments.
In early 2025, a year’s worth of internal Black Basta chat logs was leaked online, offering rare insight into the gang’s operations, hierarchy, and the security flaws it exploited to gain entry into targeted networks.
These leaked materials also exposed Nefedov as the mastermind behind the group, noting that he used several pseudonyms, including Tramp, Trump, GG, and AA. Some documents further claimed that he had connections to senior Russian political figures and intelligence agencies such as the FSB and GRU.
Investigators believe Nefedov used these connections to shield his activities and avoid prosecution. Research from Trellix found that despite being detained in Yerevan, Armenia, in June 2024, he managed to secure his release. Additional aliases tied to him include kurva, Washingt0n, and S.Jimmi. While authorities think he is somewhere in Russia, his exact location remains unknown.

Evidence also links Nefedov to Conti, a now‑defunct ransomware group formed in 2020 as a successor to Ryuk. In August 2022, the U.S. State Department offered a $10 million reward for information on five Conti members—Target, Tramp, Dandis, Professor, and Reshaev.
Notably, Black Basta emerged as an independent group in 2022 alongside BlackByte and KaraKurt after Conti publicly disbanded. Other Conti members went on to join groups such as BlackCat, Hive, AvosLocker, and HelloKitty, all of which have since shut down.“He acted as the group’s leader and determined which individuals or organizations would be attacked. He recruited members, assigned tasks, took part in ransom discussions, managed the extorted funds, and distributed payments to the group,” Germany’s Federal Criminal Police Office (BKA) stated.
Following the leaks, Black Basta appears to have collapsed. The group has remained inactive since February and removed its data leak site around the same time. However, given that ransomware operators often rebrand or resurface under new identities, experts believe former members may join other groups or create new ones.
In fact, reports from ReliaQuest and Trend Micro suggest that multiple former Black Basta affiliates may have shifted to the CACTUS ransomware group. This theory is based on a sharp increase in victim listings on CACTUS’s data leak site in February 2025, coinciding with Black Basta’s disappearance.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.