A new phishing campaign, dubbed the “Clickflix Technique,” is targeting YouTube content creators
A new phishing campaign, dubbed the “Clickflix Technique,” is targeting YouTube content creators by disguising malware as legitimate brand collaboration requests.
This attack exploits creators’ eagerness for sponsorship deals, tricking them into downloading malicious payloads under the guise of partnership documentation.
Cybercriminals initiate contact via email or social media, posing as marketing representatives from well-known brands. They offer lucrative deals that require the creator to review supposed “campaign materials” hosted on compromised domains or cloud storage.
Typically, the attackers focus on creators with subscriber counts ranging from 10,000 to 500,000. They craft highly personalized messages referencing the creator’s content style and past sponsorships to establish credibility.
When victims click on the malicious links, they are directed to professional-looking landing pages mimicking popular file-sharing services. These pages prompt them to download what appears to be a PDF contract or campaign brief but actually contains malware.
CloudSek researchers identified this campaign in early March 2025, revealing that over 2,300 creators across gaming, technology review, and lifestyle niches have been targeted. Around 18% of the victims have been successfully compromised.
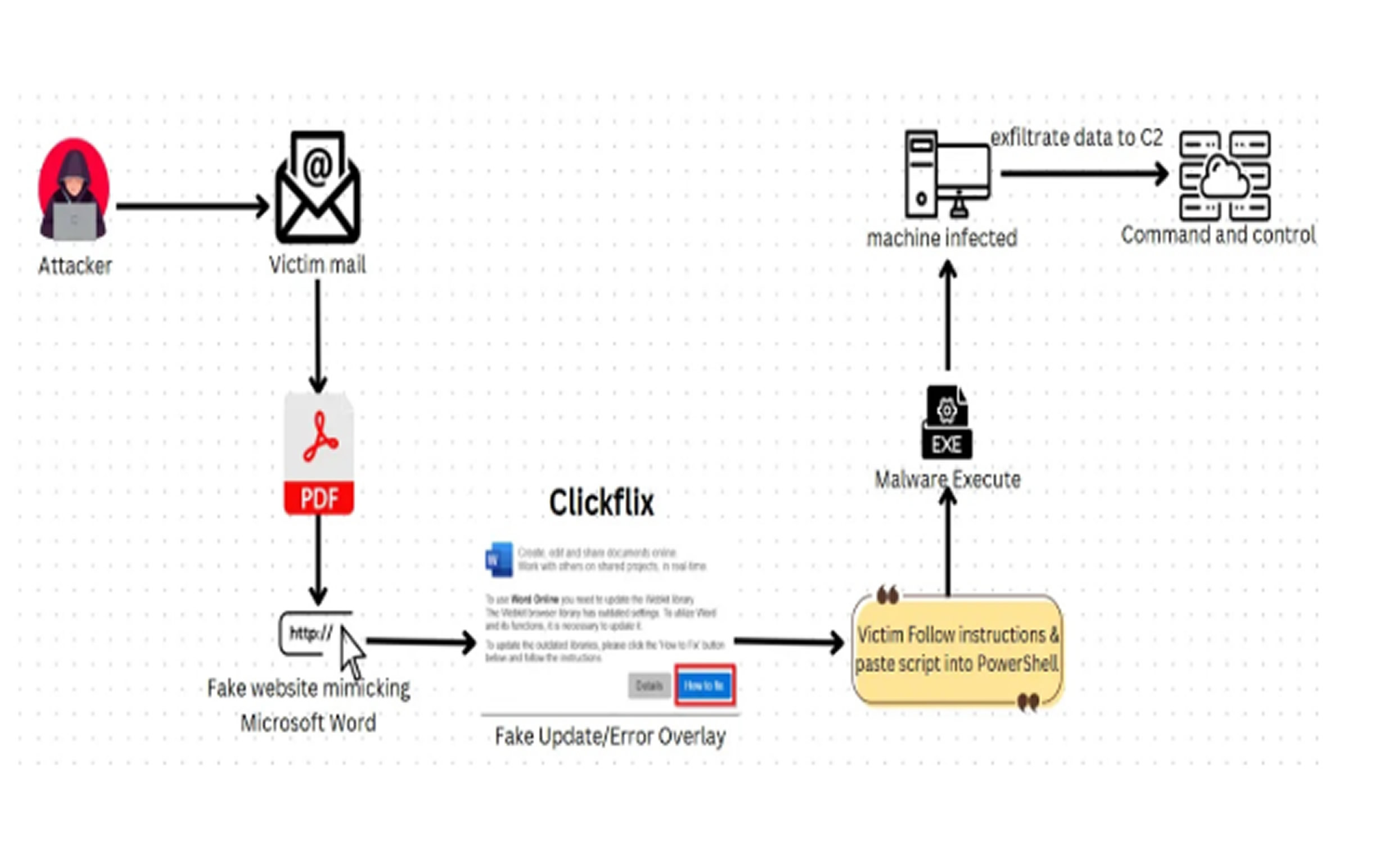
The attack employs a combination of social engineering and technical deception, often using time-sensitive offers to pressure creators into making quick decisions. Victims report receiving messages referencing specific videos they’ve produced, indicating that threat actors conduct thorough reconnaissance before initiating contact.
The malware’s infection mechanism relies on a sophisticated JavaScript downloader embedded within what appears to be a standard HTML preview page. When executed, it launches a multi-stage infection process designed to bypass traditional security solutions.

The obfuscated code ultimately executes a PowerShell command that downloads a stealer designed to extract browser data, with a specific focus on YouTube Studio credentials, Google authentication tokens, and cryptocurrency wallet information.
To maintain persistence, the malware modifies the Windows Registry and creates scheduled tasks with deceptive names like “GoogleUpdateTask,” making it harder to detect during routine system inspections.
This attack highlights the increasing sophistication of cyber threats targeting content creators, who have become valuable targets due to their monetization potential and access to highly engaged audiences.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


