Cybersecurity researchers have revealed that a threat actor known as ViciousTrap has
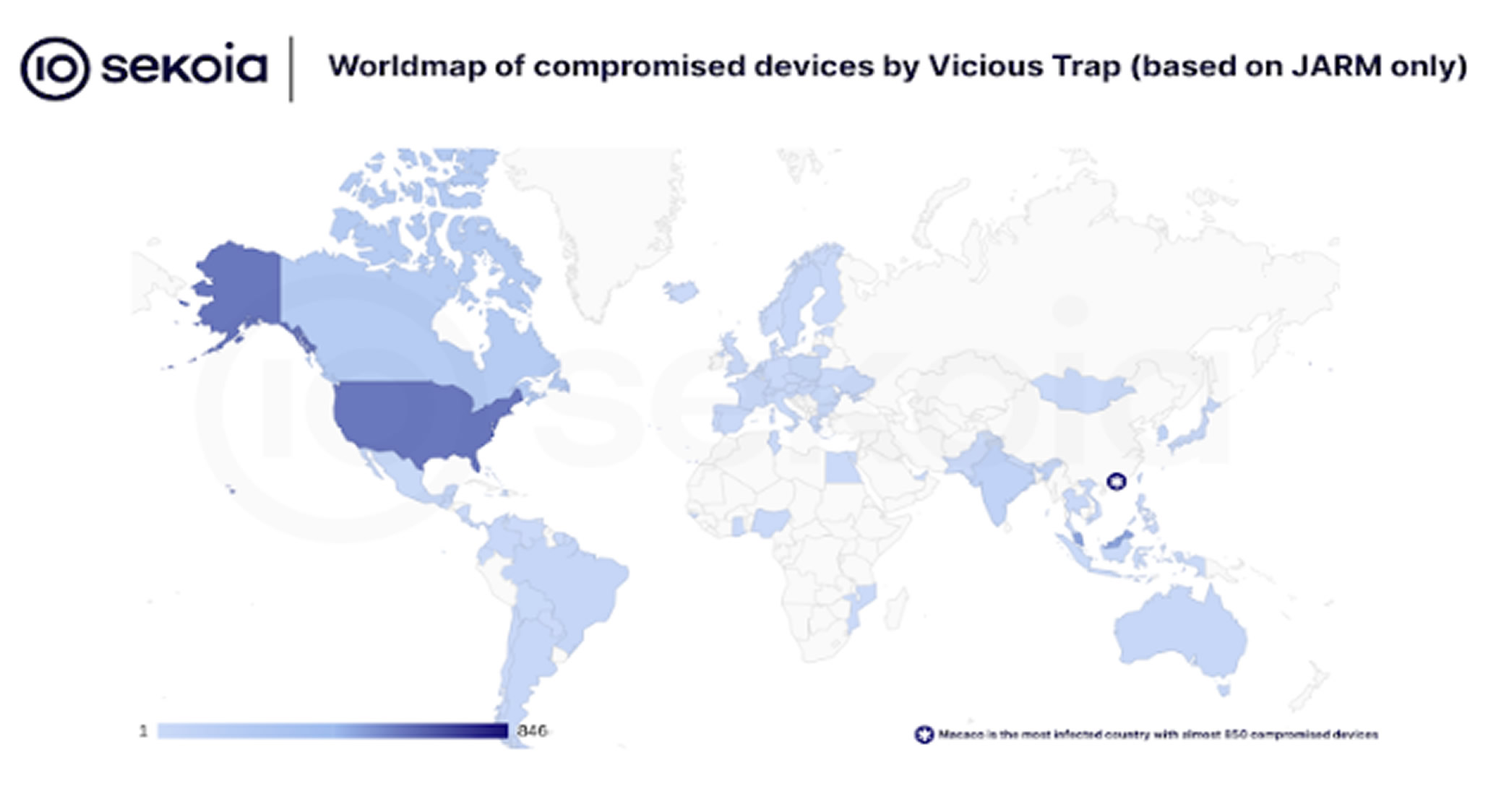
compromised nearly 5,300 unique network edge devices across 84 countries, transforming them into a honeypot-style network.
The attacker has been exploiting a critical vulnerability in Cisco Small Business routers specifically RV016, RV042, RV042G, RV082, RV320, and RV325 models (CVE-2023-20118). This mass exploitation has turned affected devices into fake systems designed to lure and monitor malicious activity. Macau accounts for the largest share, with 850 infected devices.
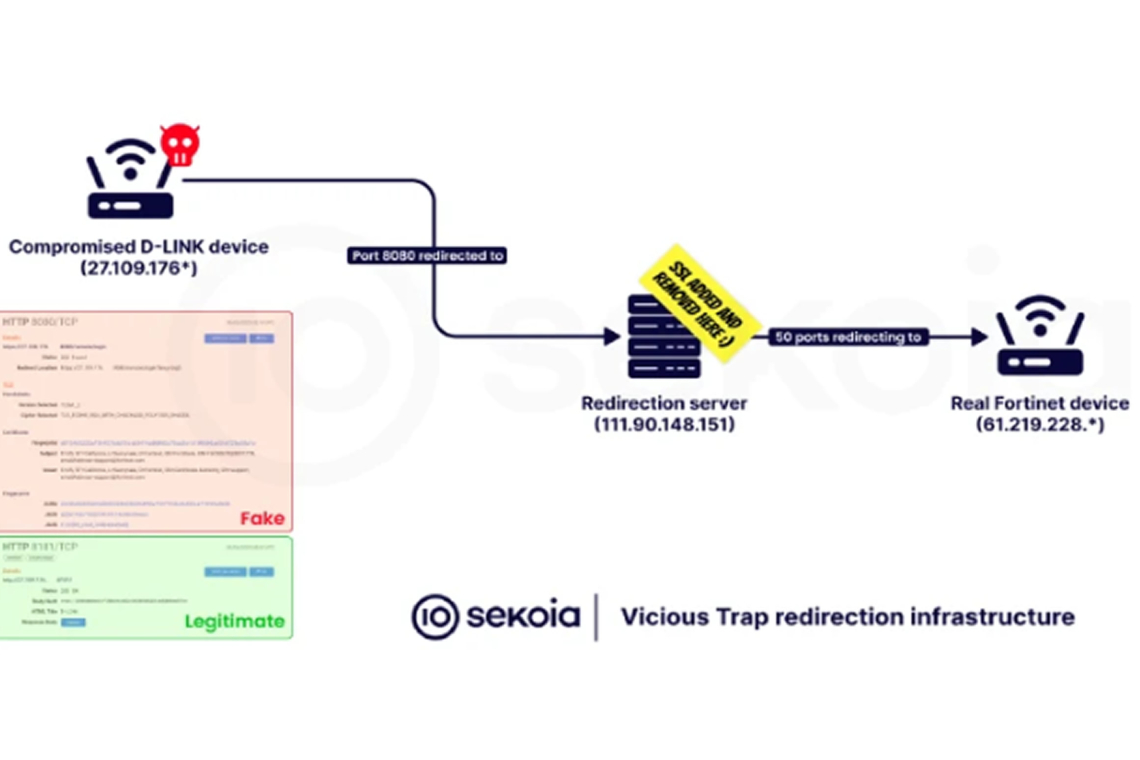
According to an analysis published Thursday by Sekoia, the infection chain starts with a shell script called NetGhost. This script redirects incoming traffic on specific ports of the compromised router to infrastructure controlled by the attacker. This allows the threat actor to intercept and observe network activity. Sekoia had previously linked exploitation of the same Cisco vulnerability to another botnet called PolarEdge.
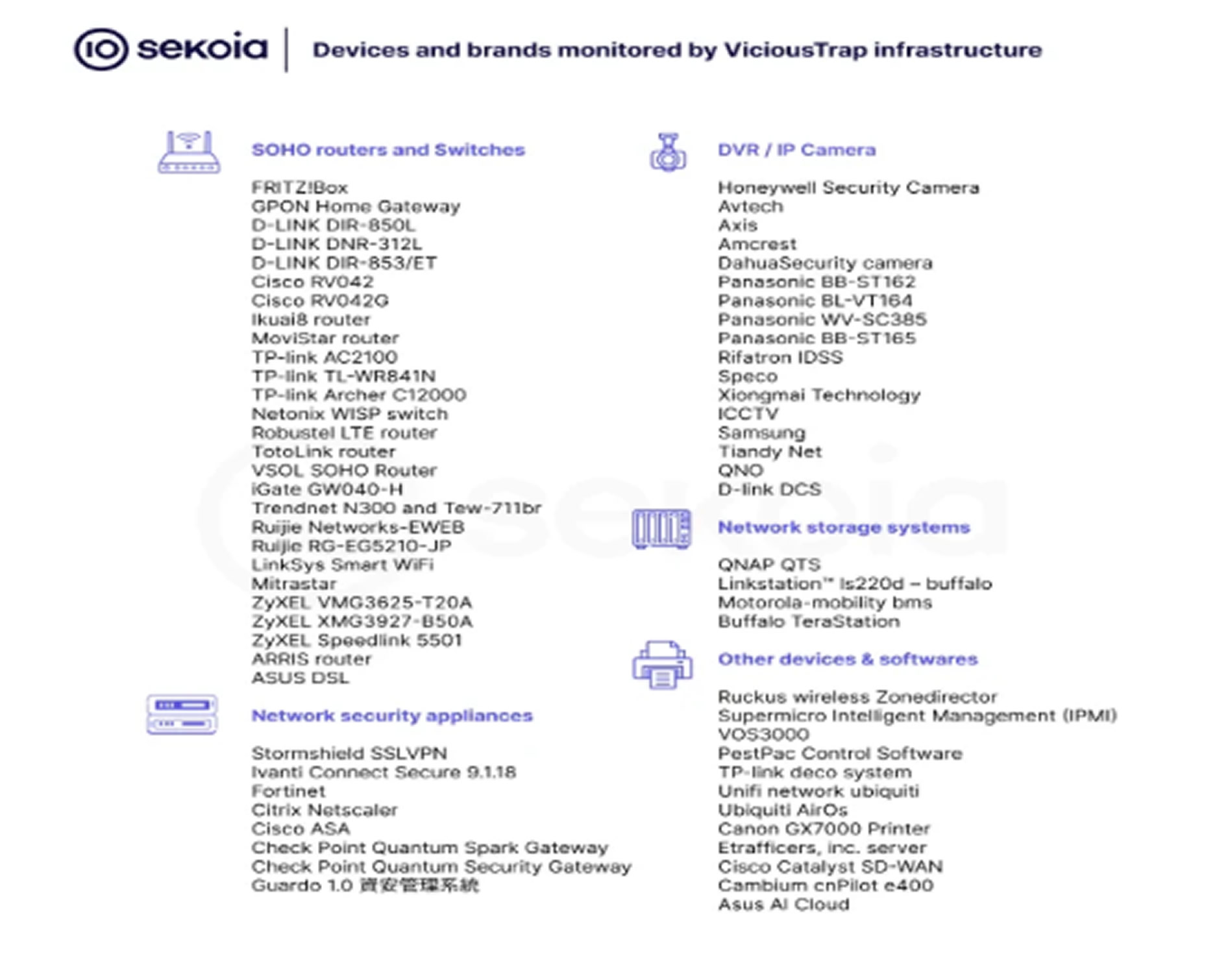
Although there is no direct evidence linking the two operations, researchers believe ViciousTrap is building its honeypot network by breaching a wide range of internet-exposed equipment. This includes SOHO routers, SSL VPNs, DVRs, and BMC controllers from over 50 brands such as Araknis Networks, ASUS, D-Link, Linksys, and QNAP. The goal appears to be the collection of exploitation attempts, including undisclosed or zero-day vulnerabilities, and the potential reuse of access obtained by other attackers.
The attack begins with the use of CVE-2023-20118 to download and execute a bash script via ftpget. This script then contacts an external server to retrieve the wget utility. In the next phase, the same Cisco flaw is exploited again to run a second script using the wget binary. This second-stage script, also named NetGhost, reroutes traffic from the infected device to third-party infrastructure under the attacker’s control. This redirection enables adversary-in-the-middle attacks and includes a function to delete itself from the system to reduce forensic evidence.
Sekoia noted that all exploitation attempts traced back to a single IP address (101.99.91[.]151), with the first activity recorded in March 2025. In April, researchers observed the attackers using a previously undocumented web shell that was once part of the PolarEdge botnet. Researchers Felix Aimé and Jeremy Scion commented that this behavior supports the idea that the attacker is silently observing traffic and possibly collecting sensitive data such as web shell access.
More recently, in May, the campaign expanded to target ASUS routers. However, these newer attacks, originating from a different IP address (101.99.91[.]239), did not result in the creation of honeypots. All IP addresses involved are based in Malaysia and belong to an Autonomous System (AS45839) operated by hosting provider Shinjiru.
Researchers believe the threat actor likely speaks Chinese, based on a minor overlap with infrastructure used by the GobRAT malware and the redirection of traffic to systems in Taiwan and the United States.
Sekoia concluded that the ultimate objective of ViciousTrap is still unknown, but the evidence strongly suggests it is building a large-scale honeypot network.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.