Google has dismantled what it believes to be one of the largest residential proxy ecosystems ever observed, securing court orders to seize domains steering IPIDEA’s backend infrastructure and disconnecting millions of consumer devices that had been unknowingly conscripted as proxy exit nodes.
The operation brought together platform providers, law enforcement, and security companies to eradicate a service that enabled large-scale espionage, cybercrime, and influence operations.
Residential proxy services sell access to IP addresses assigned by ISPs to household customers. By funneling traffic through everyday consumer devices worldwide, threat actors disguise malicious activity behind authentic-looking residential IPs, which makes detection and attribution significantly harder for defenders.
IPIDEA gained notoriety for powering multiple botnets, with its SDKs central to device onboarding and its proxy clients facilitating attacker control. Targets included BadBox 2.0 (previously the subject of Google’s legal action) and more recent botnets like Aisuru and Kimwolf.
The scale of abuse is striking: in just one week in January, Google observed over 550 tracked threat groups using IPs linked to IPIDEA exit nodes to conceal their operations. These actors—based in China, North Korea, Iran, and Russia conducted activities such as accessing victims’ SaaS environments, compromising on‑premises infrastructure, and password spraying.
Google noted that, although proxy providers may claim ignorance or remediate when notified, effective enforcement is hampered by opaque ownership, reseller chains, and a sprawling application ecosystem.
Google’s investigation found that numerous “independent” residential proxy brands were in fact tied to the same operators behind IPIDEA. Thirteen proxy and VPN labels were identified within the IPIDEA orbit, including 360 Proxy, ABC Proxy, Cherry Proxy, Door VPN, IP 2 World, Luna Proxy, and PIA S5 Proxy, among others.
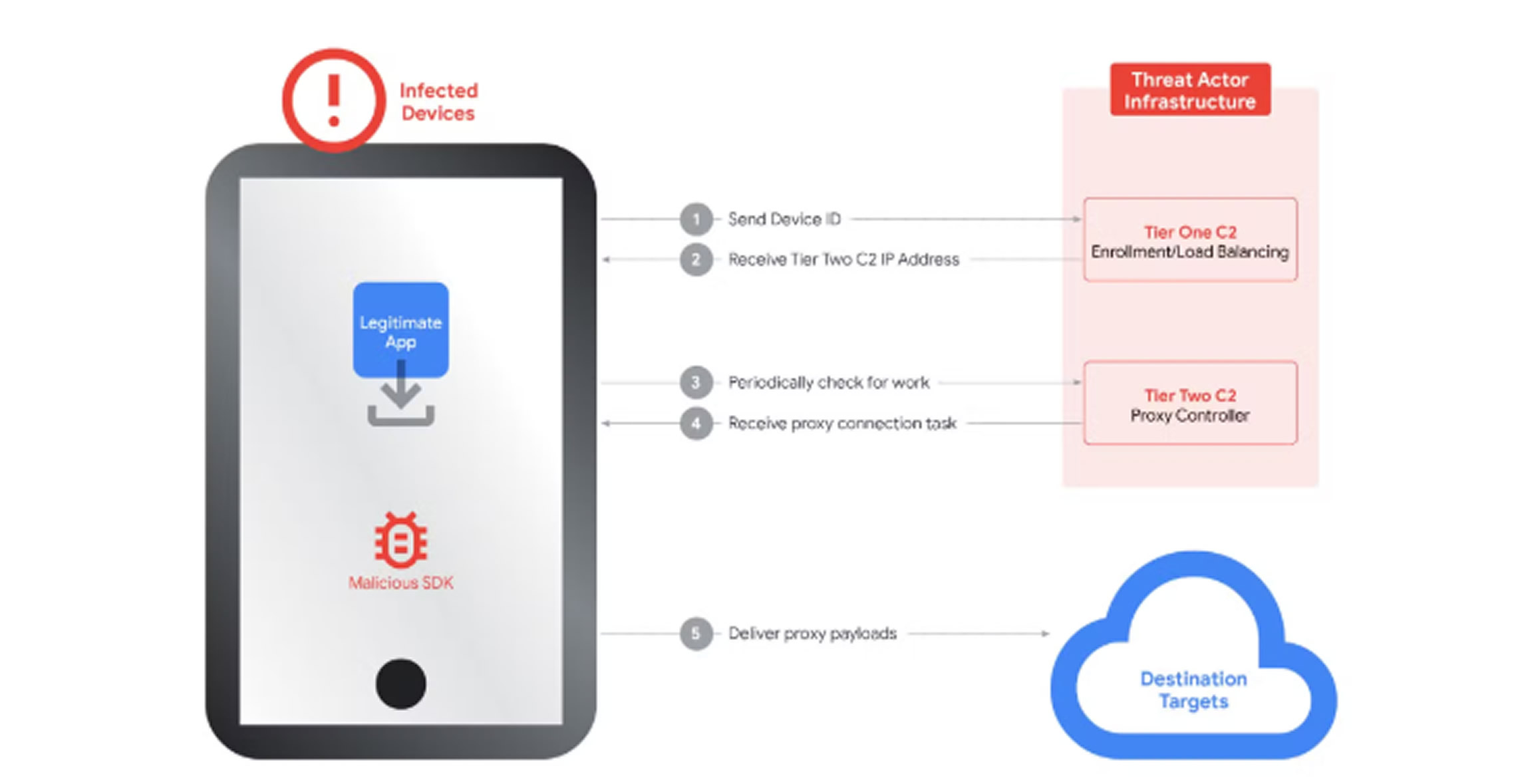
The same actors also controlled multiple SDK domains marketed to app developers as monetization tooling. Supporting Android, Windows, iOS, and WebOS, these SDKs paid developers per install and once embedded converted user devices into exit nodes while the host apps continued to provide their advertised features.
Google analyzed more than 600 Android apps from various distribution sources that contained code linking to IPIDEA command‑and‑control domains. Although these apps appeared benign—utilities, games, and content apps—they employed monetization SDKs that enabled proxy behavior without clear user disclosure.
Technically, the infrastructure ran as a two‑tier system. On startup, compromised devices contact Tier One domains and transmit diagnostics. They then receive a roster of Tier Two servers for tasking. Devices poll Tier Two endpoints periodically, obtain instructions to proxy traffic to specific destinations, and establish dedicated channels for that routing.
By the time of the takedown, Google had identified approximately 7,400 Tier Two servers, a number that fluctuated daily to meet demand. These servers were globally hosted, including within the United States.
On Windows, analysis surfaced 3,075 unique file hashes where dynamic execution produced DNS lookups to at least one Tier One domain. Some binaries masqueraded as legitimate software (e.g., OneDriveSync, Windows Update), although Google found no evidence that IPIDEA operators themselves directly distributed these trojanized builds.
Residential proxies present direct risks to consumers whose devices become exit nodes. Whether users consent or not, they lend IP addresses and hardware as launchpads for attacks, risking provider blocks or account sanctions. Such proxy apps can also weaken home network security. Once a device is turned into an exit node, third‑party traffic outside the user’s control traverses the local network, potentially allowing attackers to pivot to other devices on the same LAN and expose internal services to the public internet. Google’s analysis confirmed that IPIDEA’s proxy client not only relayed traffic but also delivered traffic intended to compromise devices.
Google’s disruption consisted of three coordinated measures:
Legal action to seize domains used to control devices and proxy traffic. Intelligence sharing on IPIDEA SDKs with platform providers, law enforcement, and research partners to spur ecosystem‑wide enforcement. Play Protect enforcement, ensuring Android’s built‑in security warns users, removes apps integrating IPIDEA SDKs, and blocks future installs, safeguarding users on certified Android devices with Google Play services.
Google assesses that these steps severely degraded IPIDEA’s capacity and business, removing millions of devices from availability. Because reseller agreements commonly pool device inventories, the disruption likely propagates downstream across affiliated services. The residential proxy sector has evolved into a deceptive “gray market,” according to Google exploiting consumer bandwidth to mask global espionage and criminal operations. Users should be extremely wary of apps that pay for “unused bandwidth” or promote “internet sharing,” as these are primary feeders for illicit proxy schemes. Google advises consumers to buy connected devices from reputable manufacturers and verify certifications. Users can consult Android TV’s partner lists and confirm Play Protect certification in device settings.
Finally, Google calls for greater accountability and policy changes. Even if some providers claim to onboard devices with explicit consent, assertions of “ethical sourcing” must be transparent and auditable. App developers also bear responsibility for vetting monetization SDKs they integrate.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



