Two serious security flaws CVE-2025-7723 and CVE-2025-7724 have been discovered in TP-Link's VIGI network video recorders, potentially allowing attackers to execute unauthorized system-level commands on targeted devices.
Vulnerability Breakdown
CVE-2025-7723 (Authenticated Access)
Attackers who gain login access to VIGI NVR1104H-4P V1 or NVR2016H-16MP V2 systems can inject OS-level commands, enabling control over surveillance operations.
- CVSS v4.0 score: 8.5
- Impact: Data breaches, altered footage, and network infiltration
CVE-2025-7724 (Unauthenticated Exploitation)
More critical due to its lack of login requirement, this flaw lets adjacent network users execute arbitrary commands remotely.
- CVSS v4.0 score: 8.7
- Impact: Full compromise of device confidentiality, integrity, and availability
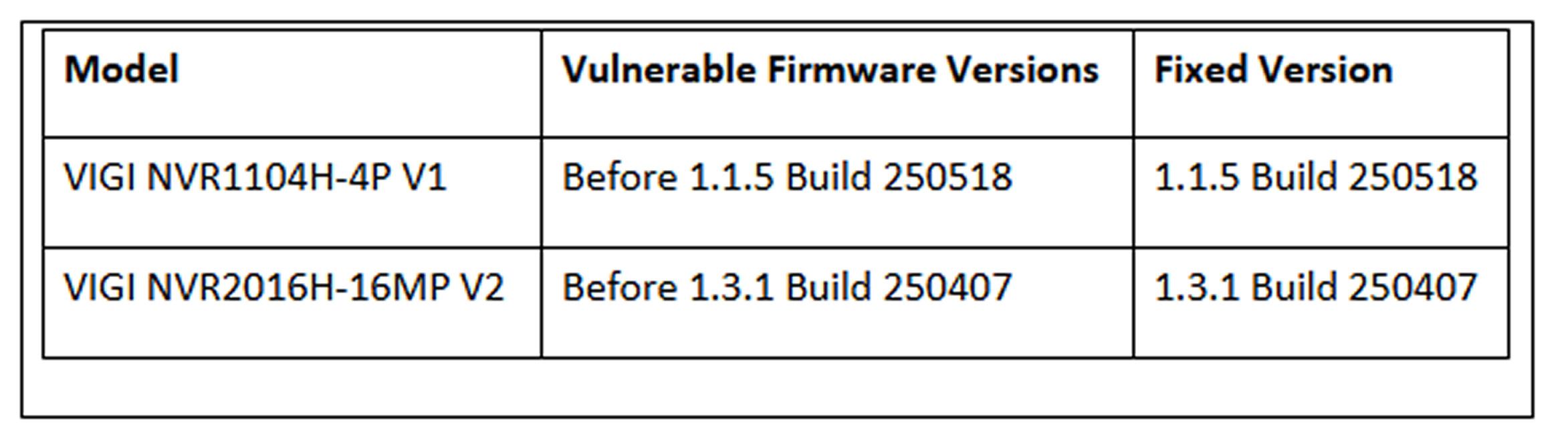
Affected Models and Firmware
Mitigation and Recommendations
TP-Link urges users to:
- Immediately apply the recommended firmware updates
- Verify post-update security configurations
- Strengthen network segmentation to minimize potential exposure
Administrators should download the patches directly from TP-Link’s official support channels and follow best practices for securing surveillance infrastructure
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



