The North Korean–aligned group known as Konni has been observed deploying PowerShell malware developed with the help of AI tools, aiming at developers and engineering teams within the blockchain ecosystem. According to a technical analysis published by Check Point Research last week, the latest phishing campaign has expanded Konni’s reach to Japan, Australia, and India, signaling a broader geographic focus beyond its historical targets in South Korea, Russia, Ukraine, and parts of Europe.
Active since at least 2014, Konni is primarily associated with operations against South Korean entities. The group is also tracked as Earth Imp, Opal Sleet, Osmium, TA406, and Vedalia.
In November 2025, researchers at the Genians Security Center (GSC) described how the actors abused Google’s asset tracking service, Find Hub, to remotely factory reset Android devices and wipe victims’ personal data—an indication of an escalating toolset and technique shift.
More recently, Konni has circulated spear‑phishing emails embedding malicious links masked as benign advertising URLs tied to Google and Naver ad platforms. This approach helps the payload slip past security filters and deliver a remote access trojan (RAT) dubbed EndRAT. GSC refers to this activity as Operation Poseidon. The campaign involves impersonations of North Korean human rights groups and South Korean financial institutions, and it relies on poorly secured WordPress sites for both malware hosting and command‑and‑control (C2) operations.
The phishing lures commonly pose as financial notices—for example, transaction confirmations or wire transfer requests—enticing recipients to download ZIP archives hosted on WordPress. Inside, a Windows shortcut (LNK) launches an AutoIt script disguised as a PDF. That script is a known Konni toolset component: EndRAT (a.k.a. EndClient RAT). GSC assessed that the adversary effectively evaded email defenses and user scrutiny by exploiting advertising click‑redirection mechanisms within the Google ads ecosystem. Specifically, the attackers abused the ad.doubleclick[.]net redirection structure to gradually shuttle users to external infrastructure hosting the actual malware.
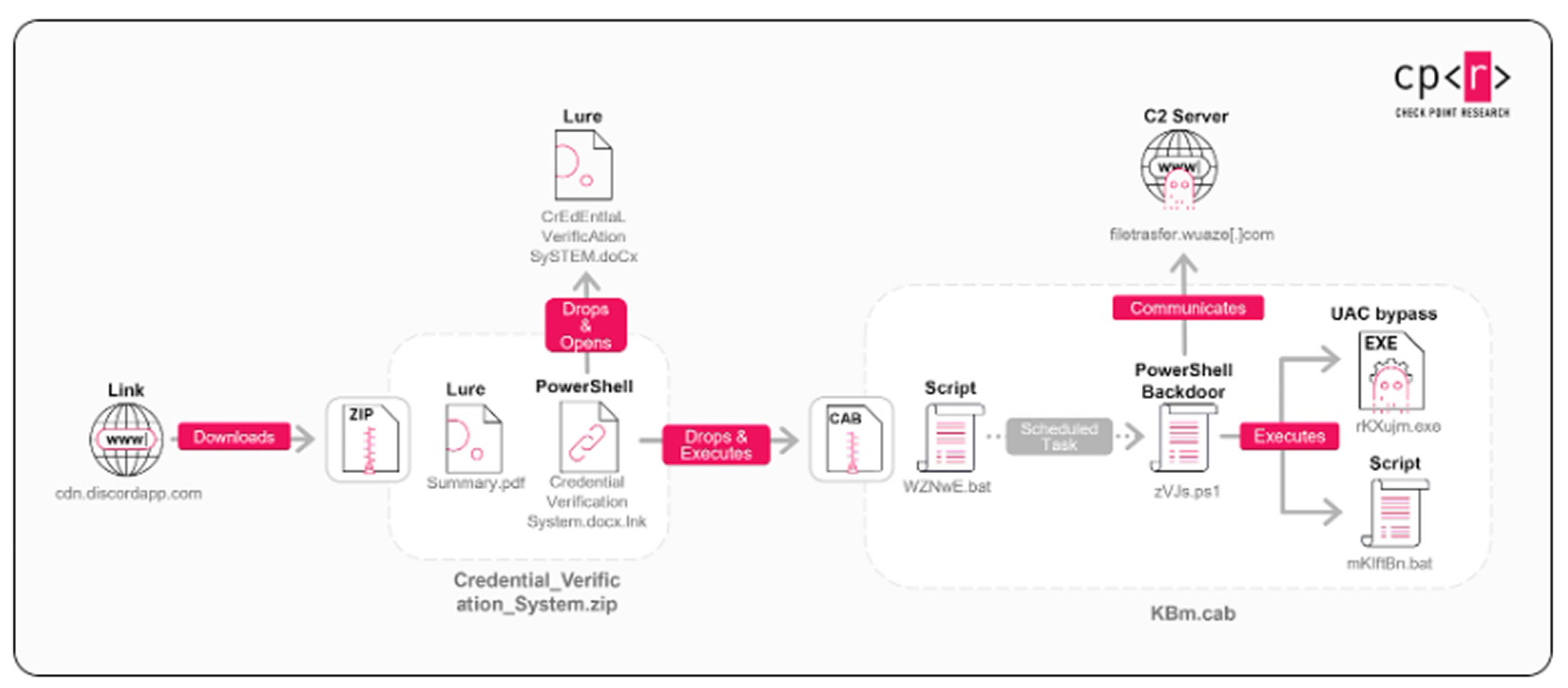
The campaign detailed by Check Point uses ZIP files themed around project requirements, hosted on Discord’s CDN, to kick off a multi‑stage intrusion chain. The precise initial access path remains unclear. The chain progresses as follows:
- The ZIP contains a PDF decoy and an LNK file.
- The shortcut runs an embedded PowerShell loader that extracts two files—a Microsoft Word lure and a CAB archive—and displays the Word document as a distraction.
- The CAB archive contains a PowerShell backdoor, two batch scripts, and an executable intended for User Account Control (UAC) bypass.
- The first batch script prepares the host, establishes persistence via Scheduled Tasks, stages and executes the backdoor, and then self‑deletes to limit forensic artifacts.
- The backdoor performs anti-analysis and sandbox‑evasion checks, profiles the system, and attempts privilege escalation using the FodHelper UAC bypass technique.
- It then removes the previously dropped UAC bypass executable, sets a Microsoft Defender exclusion for C:\ProgramData, and runs a second batch script to replace the scheduled task with one capable of elevated execution.
- Finally, it deploys SimpleHelp—a legitimate RMM tool—for persistent remote access, and communicates with a C2 protected by an encryption gate that blocks non‑browser traffic. The agent periodically sends host metadata and executes PowerShell returned by the server.
Check Point notes indications that the PowerShell backdoor was AI‑assisted, citing its modular design, readable inline documentation, and source comments such as “# ← your permanent project UUID.” Rather than focusing on individual end users, the operation appears designed to gain footholds in development environments, where a single compromise can yield downstream access across numerous projects and services. The incorporation of AI‑assisted tooling likely reflects an effort to speed development, standardize code, and scale operations while continuing to leverage established delivery methods and social engineering.
These findings coincide with a broader set of North Korean–driven campaigns enabling remote control and data theft, including:
- A spear‑phishing wave using JavaScript Encoded (JSE) files masquerading as HWPX documents with government‑themed decoys, ultimately deploying a Visual Studio Code (VS Code) tunnel for remote access.
- A phishing chain distributing LNK files that look like PDFs, which launch a PowerShell script to detect virtualization and analysis environments and then deliver a RAT called MoonPeak.
- Two Andariel operations in 2025: one against an unnamed European legal entity to deliver TigerRAT, and another abusing a South Korean ERP vendor’s update mechanism to push StarshellRAT, JelusRAT, and GopherRAT to downstream targets.
Per WithSecure, the same ERP software has suffered similar supply‑chain compromises twice before—2017 and 2024—to distribute families like HotCroissant and Xctdoor. As for the toolset: JelusRAT (C++) supports plugin retrieval from C2; StarshellRAT (C#) enables command execution, file transfer, and screenshot capture; and GopherRAT (Go) can run binaries/commands, exfiltrate files, and enumerate the filesystem.
“WithSecure” researcher Mohammad Kazem Hassan Nejad notes that the group’s goals vary over time—from financially motivated activity to intelligence collection aligned with regime priorities—demonstrating flexibility and the ability to support shifting strategic objectives.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



