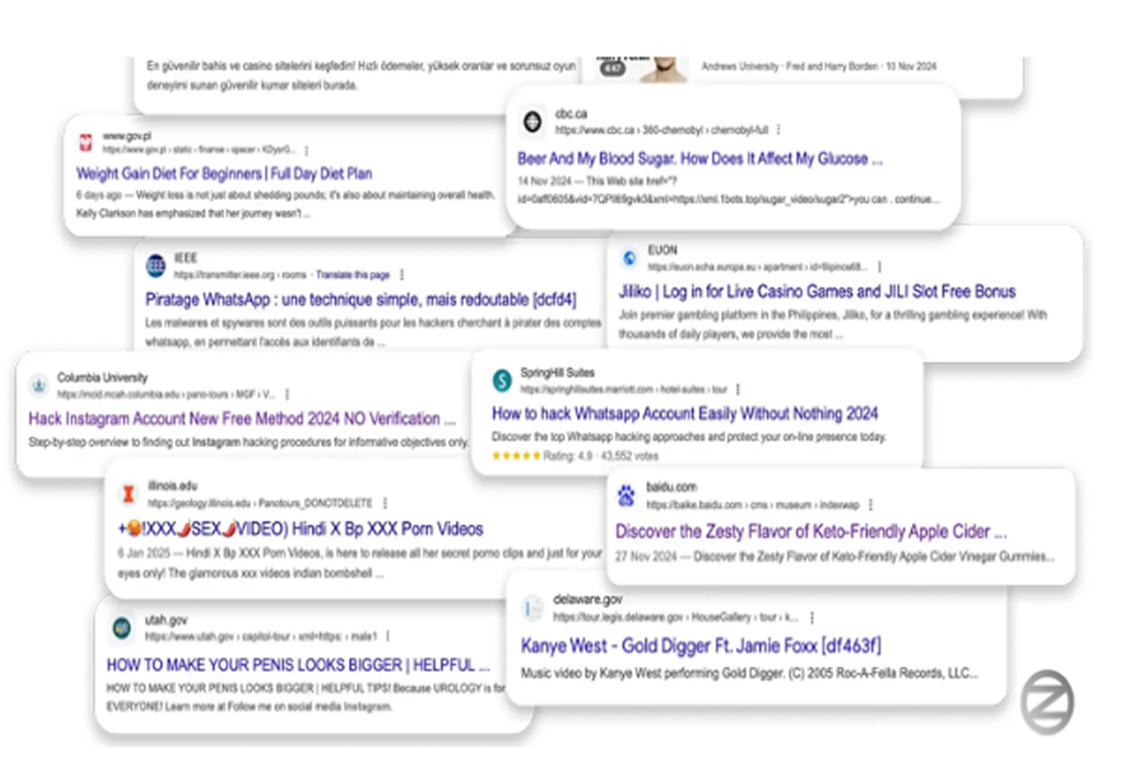
Massive XSS Exploit in Virtual Tour Framework Hijacks 350+ Websites
A cross-site scripting (XSS) vulnerability in a widely used virtual tour framework has been exploited by attackers to inject malicious scripts into hundreds of legitimate websites, manipulating search results and running a large-scale spam ad campaign.
Overview of the 360XSS Campaign
Security researcher Oleg Zaytsev shared details of the attack, dubbed 360XSS, with The Hacker News. The campaign impacted over 350 websites, including:
- Government portals (including U.S. state government sites)
- American universities (e.g., Yale University)
- Major hotel chains
- News outlets
- Car dealerships
- Fortune 500 companies
Attackers used a known XSS vulnerability to inject ads for pornography, diet supplements, online casinos, and fake news sites into high-trust domains, making them appear prominently in search results through a technique known as SEO poisoning.
How the Attack Works
Exploiting the Krpano Framework
- The attack targets Krpano, a popular framework used to embed 360° images and videos for virtual tours and VR experiences.
- Specifically, it abuses a "passQueryParameters" setting that allows HTTP parameters to be passed via URL to an embedded panorama viewer.
Leveraging a Known XSS Vulnerability
- The reflected XSS flaw (CVE-2020-24901, CVSS score: 6.1) was first disclosed in 2020.
- While Krpano version 1.20.10 attempted to fix this issue by restricting parameters to an allowlist, Zaytsev found that manually adding XML parameters back into the allowlist reintroduced the risk.
- Many websites are still running older versions of Krpano, making them vulnerable.
Weaponizing Trusted Domains
- Attackers trick search engines into displaying malicious URLs by injecting ads into trusted domains.
- When users click a compromised search result, the website executes a Base64-encoded script, which fetches and displays spam ads from another website.
“A reflected XSS is a fun vulnerability, but on its own, it requires user interaction. One of the biggest challenges is to make people click your reflected XSS link. Using search engines as a distribution platform for XSS is a very creative and cool way to do it.” — Oleg Zaytsev
Massive Impact and Ongoing Investigation
- The true scale of the operation remains unclear, but it appears to be an industrial-scale abuse of trusted domains.
- Attackers did not use the exploit for credential theft or more dangerous attacks, suggesting a black-hat ad network is behind the campaign.
The Krpano development team has responded by releasing version 1.22.4, which:
Eliminates support for external XML configuration
Restricts external URLs in query parameters
Mitigation and Recommendations
For Website Owners:
- Update to Krpano 1.22.4 immediately
- Disable “passQueryParameters” in configuration settings
- Check for infected pages using Google Search Console
For Users:
- Be cautious of unexpected redirects from search results
- Use browser security tools to block malicious scripts
Final Thoughts
This XSS-driven SEO poisoning campaign demonstrates how attackers can exploit legitimate, high-trust domains at scale for monetization. The 360XSS attack was not just a spam operation. it was an industrial-level abuse of trusted domains, emphasizing the ongoing need for stronger web security across platforms.