ASUS Fixes Two Critical Flaws in DriverHub That Could Allow Remote Code Execution
ASUS has issued updates to fix two security vulnerabilities in its DriverHub software, which could allow attackers to remotely execute code if successfully exploited.
DriverHub is designed to automatically detect a computer’s motherboard model and suggest necessary driver updates. It communicates with a dedicated server hosted at "driverhub.asus[.]com."
The two vulnerabilities are:
CVE-2025-3462 (CVSS score: 8.4): A flaw related to origin validation that might allow unauthorized sources to interact with DriverHub’s features using specially crafted HTTP requests.
CVE-2025-3463 (CVSS score: 9.4): A vulnerability tied to improper certificate validation, which could let untrusted sources influence system behavior through crafted HTTP requests.
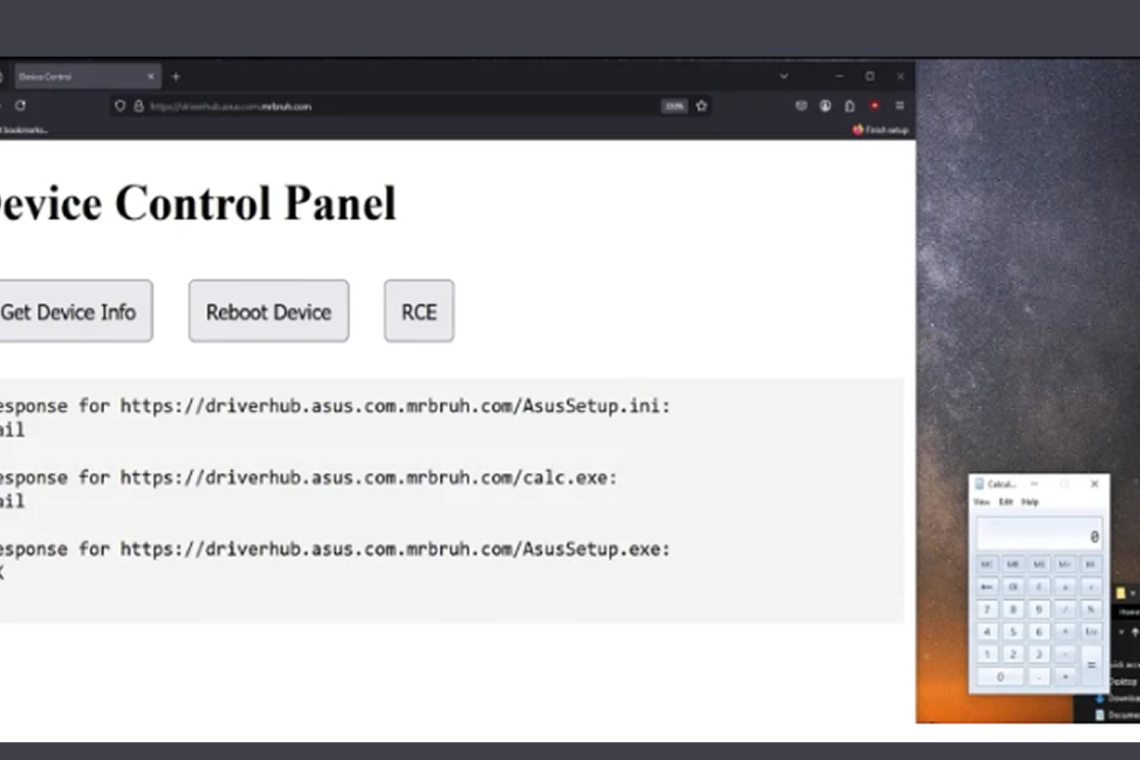
Security researcher MrBruh, who discovered and reported the issues, noted that these flaws could be used for remote code execution through a one-click attack. The method involves directing a user to a malicious sub-domain resembling driverhub.asus[.]com and exploiting DriverHub’s UpdateApp endpoint to run a legitimate "AsusSetup.exe" file with settings that execute a file from the attacker’s server.
According to the researcher, AsusSetup.exe reads from an AsusSetup.ini file that contains metadata about the driver. When the file is run with the -s flag, which is how DriverHub performs silent installations, it executes the command specified in the "SilentInstallRun" field of the ini file. In normal use, this would automate a driver installation, but it could also be configured to run a malicious script.
To exploit this vulnerability, an attacker would only need to set up a domain and host three files: a malicious payload, a modified AsusSetup.ini file with the payload specified in the "SilentInstallRun" field, and the AsusSetup.exe installer.
The vulnerabilities were responsibly disclosed to ASUS on April 8, 2025, and fixes were released on May 9. ASUS has stated that there is no evidence of these flaws being exploited in the wild.
In a bulletin, the company urged users to update immediately: “This update includes important security improvements, and ASUS strongly recommends updating ASUS DriverHub to the latest version. Users can do this by opening DriverHub and clicking the ‘Update Now’ button.”
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.