A new vulnerability called "Branch Privilege Injection" has been discovered in all modern Intel CPUs,
allowing attackers to leak sensitive data from memory regions allocated to privileged software, such as the operating system kernel.
These regions typically contain information like passwords, cryptographic keys, memory from other processes, and kernel data structures, making their protection crucial.
ETH Zurich researchers Sandro Rüegge, Johannes Wikner, and Kaveh Razavi explained that although Spectre v2 mitigations were effective for six years, their new exploit, dubbed "Branch Predictor Race Conditions," bypasses these protections. Tracked as CVE-2024-45332, this flaw involves a race condition in the branch predictor subsystem of Intel CPUs.
Branch predictors, such as the Branch Target Buffer (BTB) and Indirect Branch Predictor (IBP), are specialized hardware components that predict the outcome of branch instructions before they're resolved, keeping the CPU pipeline full for optimal performance. While these predictions are speculative and undone if incorrect, they improve performance when correct.
The researchers found that updates to Intel's branch predictors are not synchronized with instruction execution, leading to updates crossing privilege boundaries. When a privilege switch occurs, like from user mode to kernel mode, a small window opens during which the update may be associated with the wrong privilege level. This breaks the isolation between user and kernel, allowing a non-privileged user to leak data from privileged processes.
The ETH Zurich team developed an exploit that trains the CPU to predict a specific branch target, then triggers a system call to move execution into the OS kernel. This results in speculative execution using an attacker-controlled target, accessing secret data loaded into the cache. The attacker then uses a side-channel method to leak the contents.
In their demonstration, the researchers used Ubuntu 24.04 with default mitigations enabled to read the contents of the '/etc/shadow/' file, which contains hashed account passwords. The exploit achieved peak leak rates of 5.6 KB/sec with 99.8% accuracy.
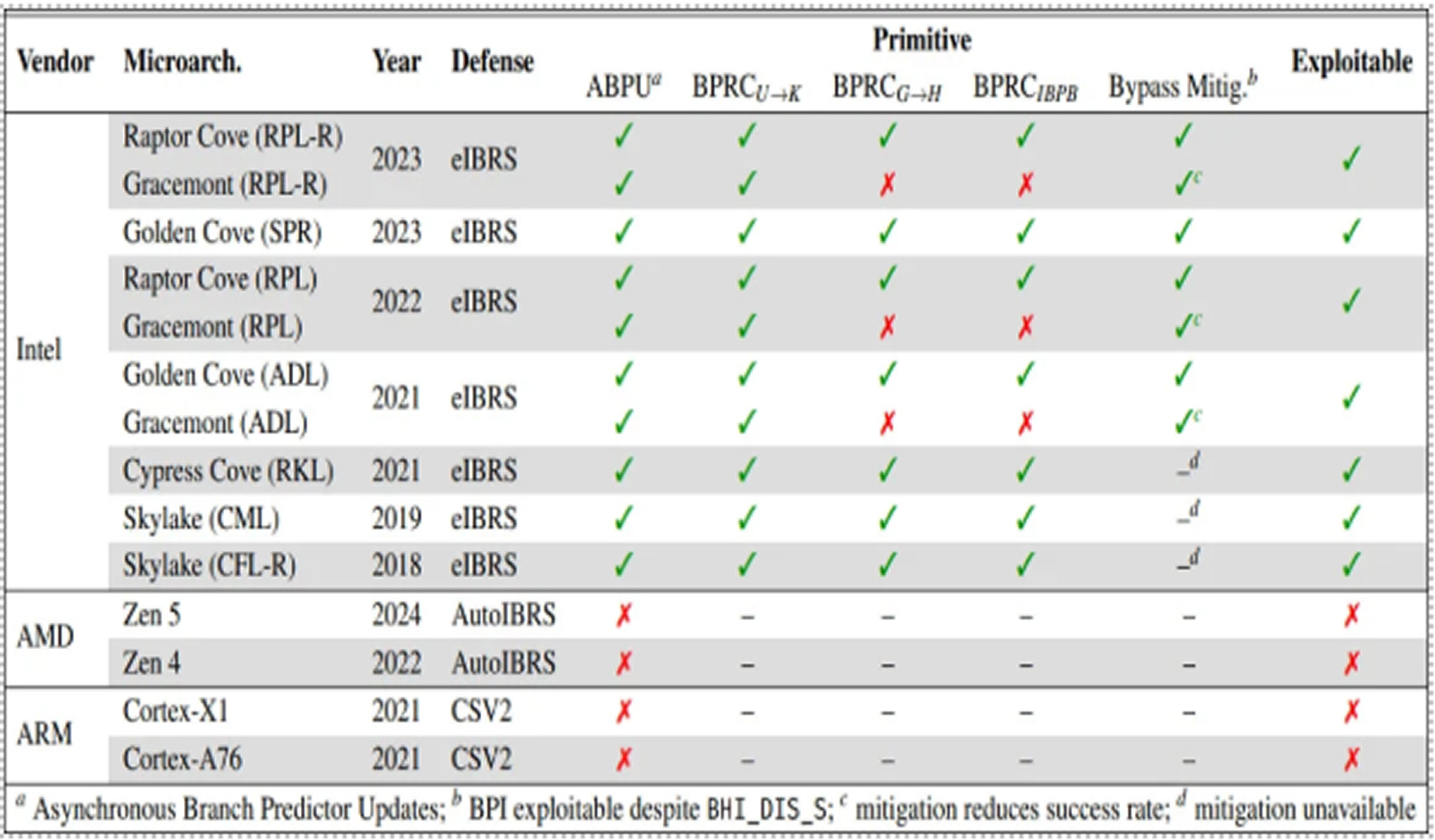
CVE-2024-45332 affects all Intel CPUs from the ninth generation onward, including Coffee Lake, Comet Lake, Rocket Lake, Alder Lake, and Raptor Lake. Researchers also observed that predictions bypassed the Indirect Branch Prediction Barrier (IBPB) on processors as far back as the seventh generation (Kaby Lake). However, older generations, which do not support Enhanced Indirect Branch Restricted Speculation (eIBRS), are less relevant to this exploit and may be more vulnerable to older Spectre v2-like attacks.
Arm Cortex-X1, Cortex-A76, and AMD Zen 5 and Zen 4 chips were also tested but do not show the same behavior, so they are not vulnerable to CVE-2024-45332.
While the attack was demonstrated on Linux, the flaw exists at the hardware level and is theoretically exploitable on Windows as well.
The researchers reported the vulnerability to Intel in September 2024, and Intel has since released microcode updates to mitigate the issue on affected models. These firmware-level mitigations introduce a 2.7% performance overhead, while software mitigations cause a performance impact ranging from 1.6% to 8.3%, depending on the CPU.
The risk for regular users is low, as attacks require several strong prerequisites to be realistically exploited. However, it is still recommended to apply the latest BIOS/UEFI and OS updates.
ETH Zurich will present the full details of their exploit in a technical paper at the upcoming USENIX Security 2025 conference. Intel expressed appreciation for the research and collaboration on public disclosure, stating that they are strengthening their Spectre v2 hardware mitigations and recommending that customers contact their system manufacturer for the appropriate update. To date, Intel is not aware of any real-world exploits of transient execution vulnerabilities.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


