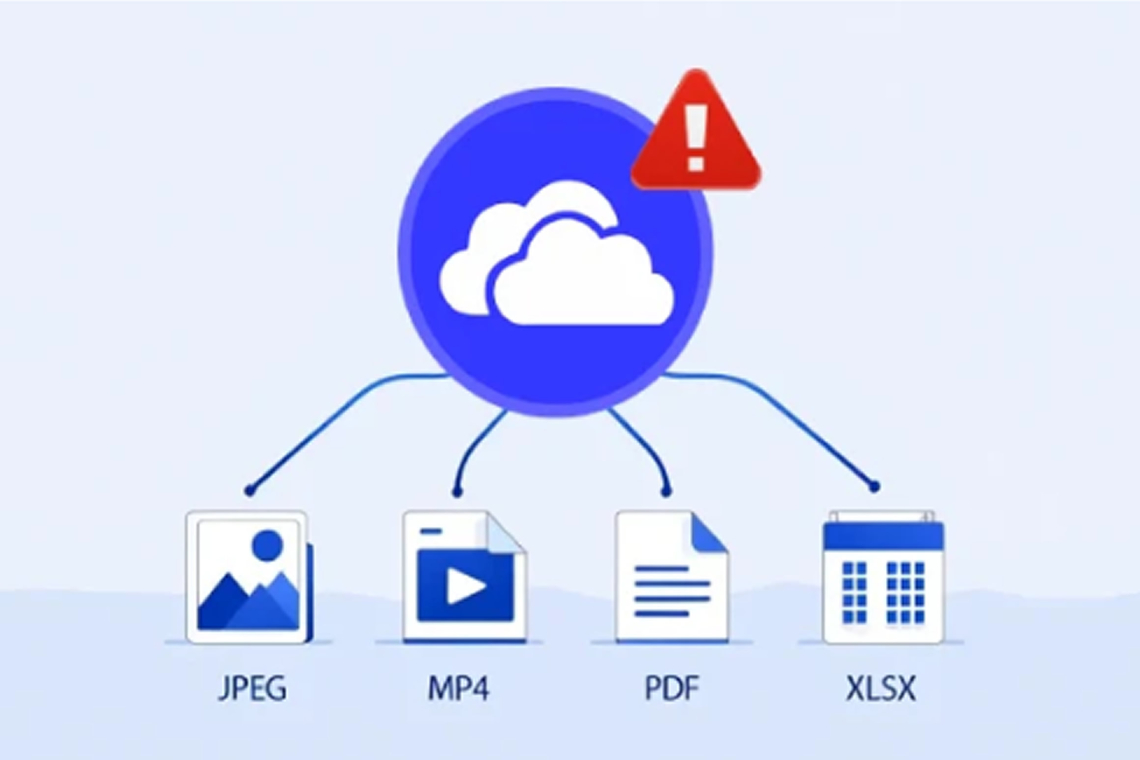
Cybersecurity researchers have identified a vulnerability in Microsoft's OneDrive File Picker
that could let websites access a user's entire cloud storage rather than just the files selected for upload.
According to a report shared with The Hacker News by the Oasis Research Team, the issue stems from broad OAuth scopes and consent screens that do not clearly communicate the level of access being granted. The flaw poses serious risks, including potential data leaks and non-compliance with regulations. The team noted that several apps such as ChatGPT, Slack, Trello, and ClickUp are affected due to their integration with Microsoft's cloud platform.
The root of the problem lies in the excessive permissions requested by the OneDrive File Picker. Even when a user uploads just one file, the tool asks for read access to the entire drive because OneDrive does not support more specific OAuth scopes.
Making matters worse, the consent screen shown to users before uploading is vague and fails to explain the depth of access involved. This exposes users to potential security threats without their full understanding.
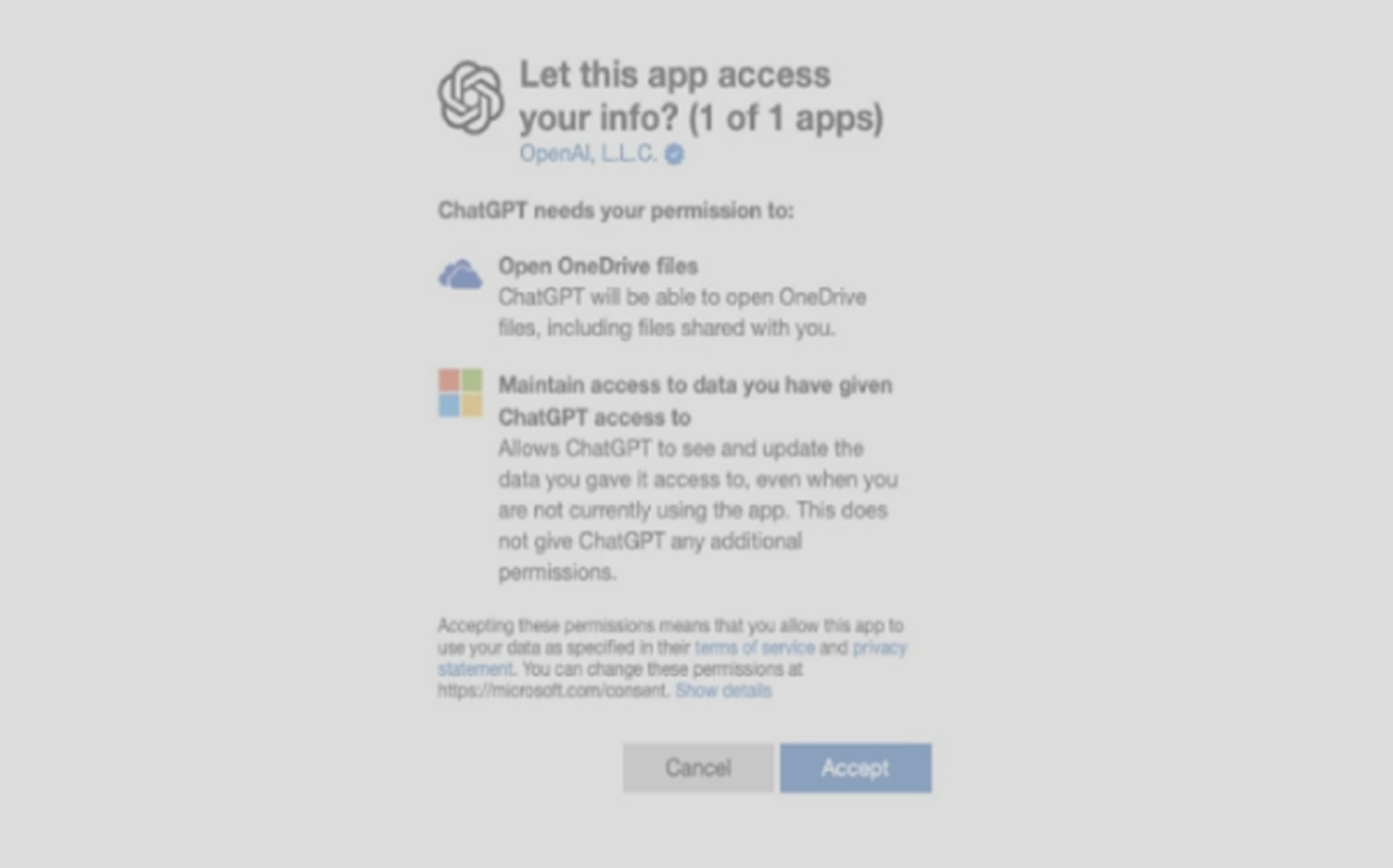
Oasis emphasized that the absence of fine-grained scopes makes it hard for users to tell the difference between malicious apps and legitimate ones that request too many permissions simply because there are no safer alternatives. They also warned that OAuth tokens used to grant access are sometimes stored insecurely. In some cases, these tokens are kept in the browser’s session storage in plain text.
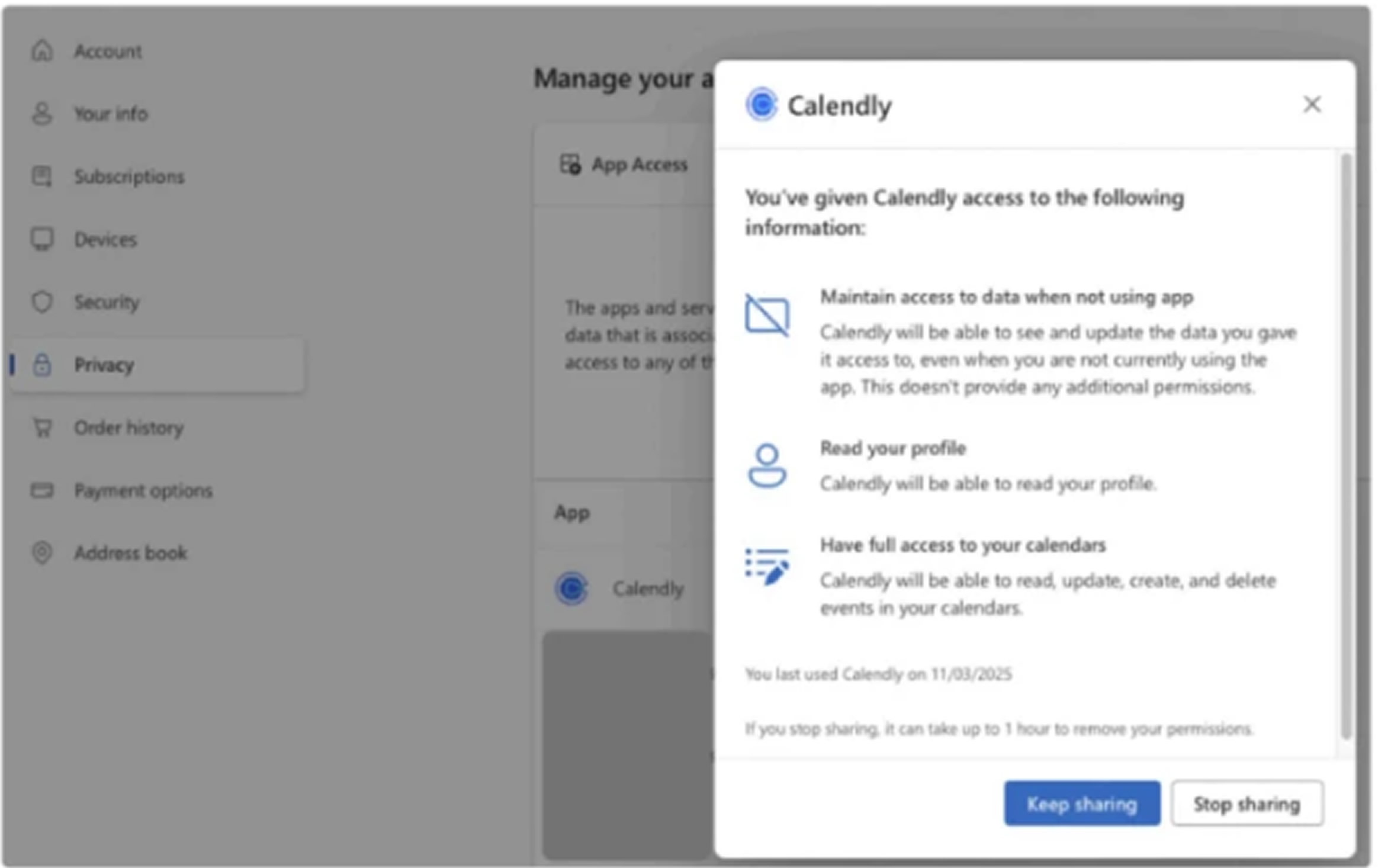
Another concern is the use of refresh tokens, which allow apps to maintain access to user data by generating new access tokens even after the original expires. This can result in continued access without requiring the user to log in again.
Microsoft has acknowledged the issue after responsible disclosure, although no fix has been released yet. In the meantime, it is recommended to temporarily disable file uploads via OneDrive using OAuth until a safer solution is implemented. Alternatively, users should avoid using refresh tokens, securely store access tokens, and delete them once they are no longer needed.
The Hacker News has contacted Microsoft for additional comments and will provide updates if new information becomes available.
Oasis concluded by saying the combination of broad OAuth scopes and unclear prompts from Microsoft presents a real danger to both personal and business users. They stressed the need for ongoing monitoring, regular security reviews, and careful OAuth scope management to safeguard user data.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.