New Malware "Arcane" Targets VPNs, Network Tools via YouTube Scam
A sophisticated new malware strain known as "Arcane" is actively targeting VPN clients, network utilities, and file transfer applications, putting thousands of users at risk.
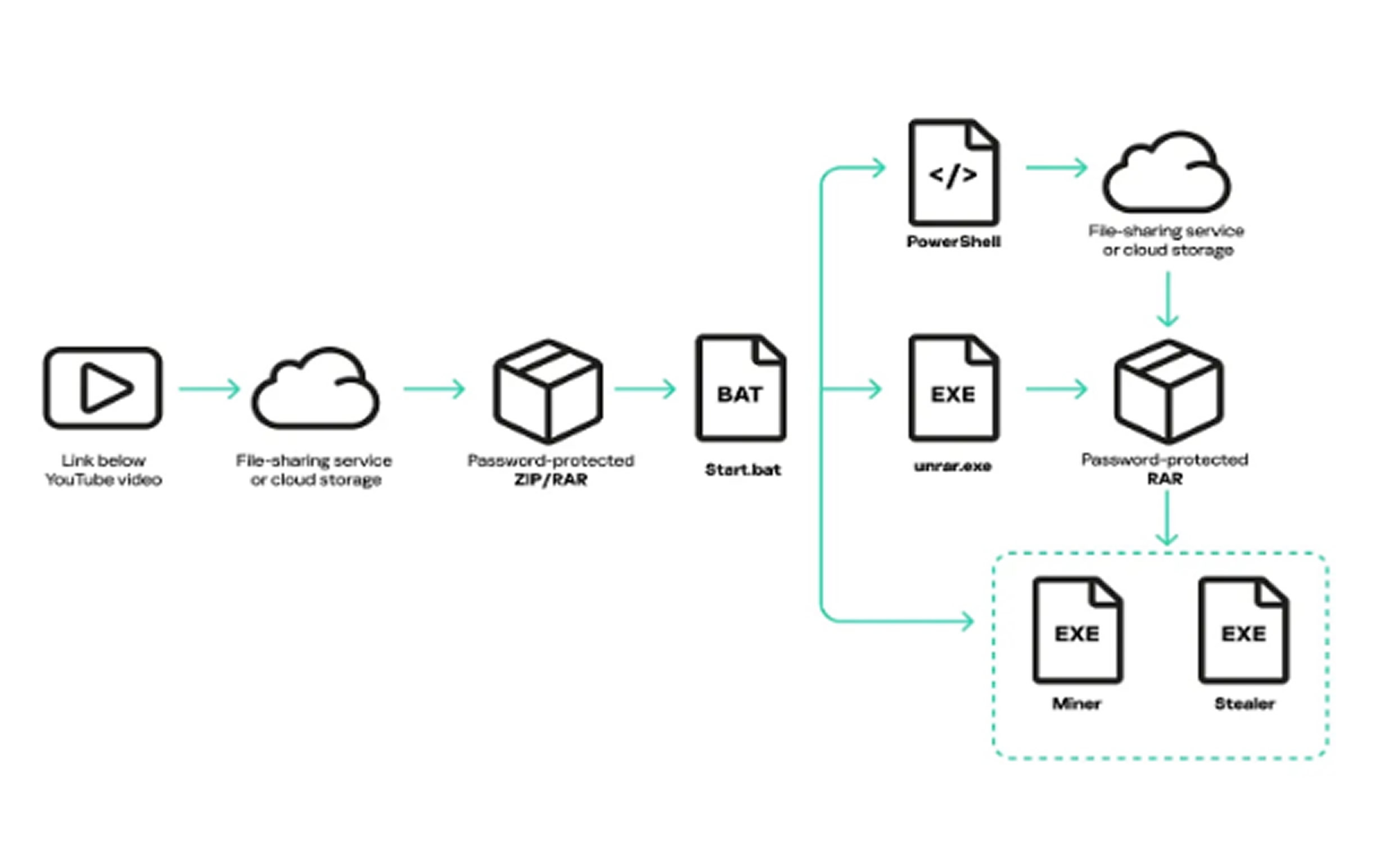
Discovered in late 2024, Arcane is being distributed through deceptive YouTube videos promoting game cheats and cracks. Attackers lure victims with download links to password-protected archives containing a malicious start.bat file. Once executed, this file disables Windows SmartScreen protection and downloads additional malware onto the system.
Security researchers tracking the campaign highlight Arcane's ability to steal account credentials and configuration data from a wide range of applications. The malware specifically targets VPN clients such as OpenVPN, Mullvad, NordVPN, IPVanish, Surfshark, ProtonVPN, CyberGhost, ExpressVPN, and PIA.
Additionally, Arcane extracts data from network utilities including ngrok, Playit, Cyberduck, FileZilla, and DynDNS. It also employs advanced techniques to steal browser data, using the Data Protection API (DPAPI) to obtain encryption keys and the Xaitax utility to crack browser keys. Furthermore, the malware uses a unique debug port method to extract cookies by secretly launching browser instances.
Initially, attackers distributed VGS stealer, a variant of the Phemedrone Trojan, but by November 2024, they switched to the more advanced Arcane stealer. Despite the name, this malware is unrelated to the older “Arcane Stealer V” from 2019.
More recently, the hackers have refined their approach. Instead of directly promoting game cheats, they now advertise a fake program called “ArcanaLoader”, claiming to provide popular cracks and cheats. This loader, which features a graphical user interface, is promoted via YouTube channels controlled by the attackers.
To further spread the malware, the attackers have set up a Discord server, where they post updates and even recruit bloggers to promote their malicious software. Researchers confirmed that ArcanaLoader secretly installs the Arcane stealer upon execution.
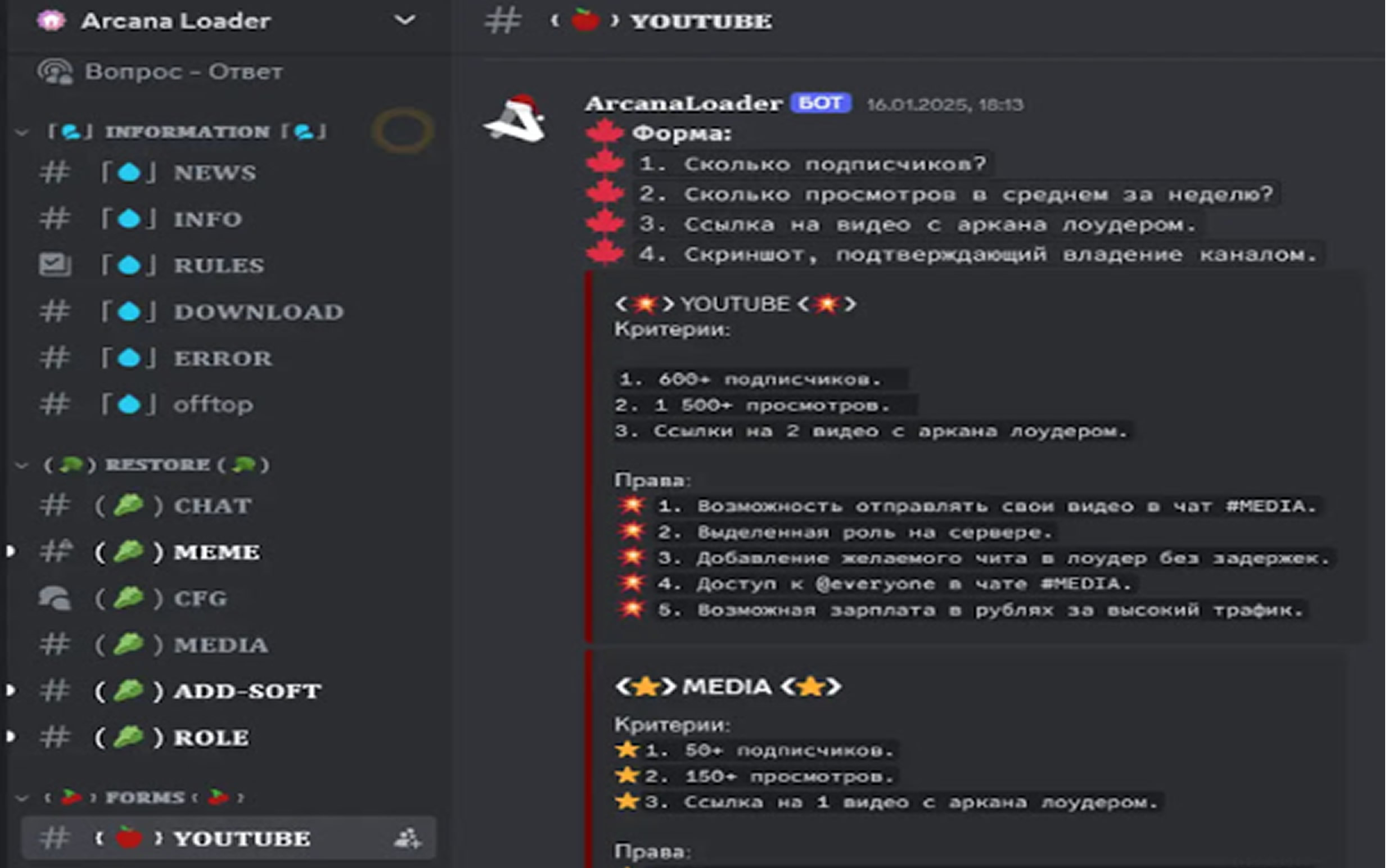
Based on telemetry data, Discord conversations, and YouTube activity, researchers believe the attackers are primarily targeting Russian-speaking users. Most victims have been detected in Russia, Belarus, and Kazakhstan.
Cybersecurity experts warn that Arcane’s advanced data collection capabilities pose a serious threat to personal and corporate security. Users are urged to avoid downloading game cheats or cracks from YouTube, particularly those requiring password-protected archives or batch file execution.
With Arcane’s ability to compromise VPNs, network tools, and browser credentials, unsuspecting users could inadvertently expose sensitive data, login credentials, and financial information to cybercriminals.


