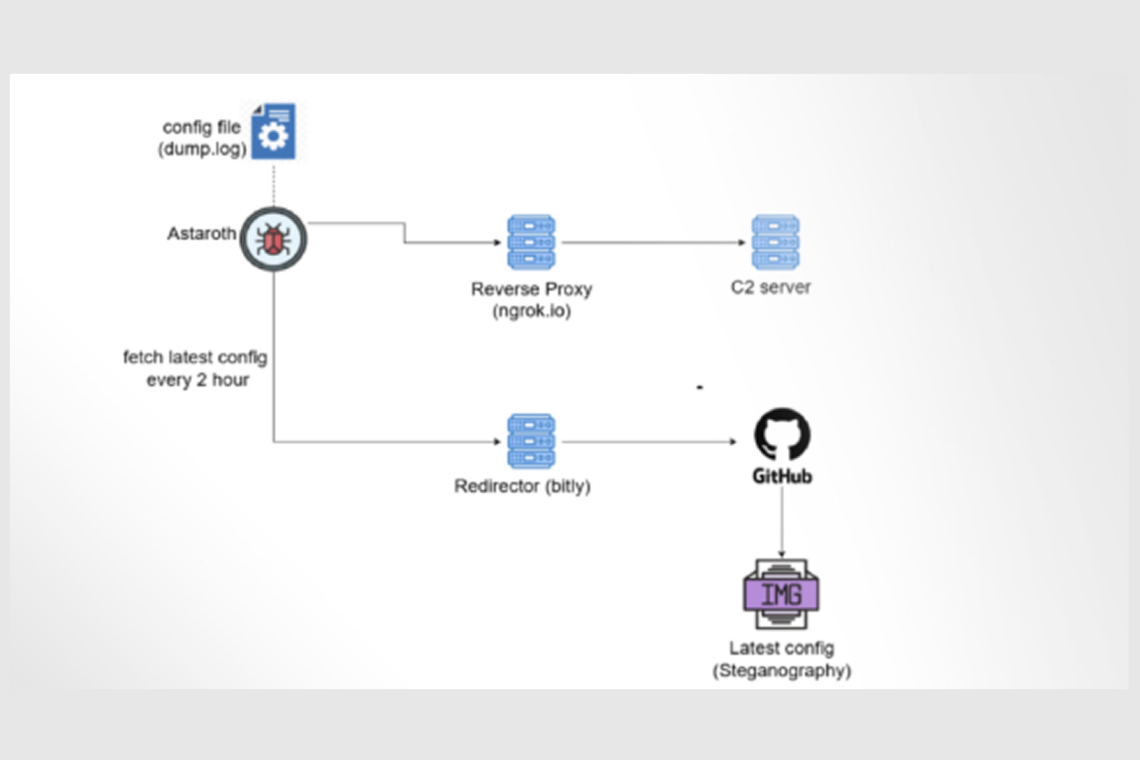
Cybersecurity researchers are highlighting a new campaign distributing the Astaroth banking trojan that utilizes GitHub as a resilient backup infrastructure for its command-and-control (C2) operations. This strategy allows the attackers to maintain persistence even if their primary C2 servers are shut down.
GitHub for Resilience
According to McAfee Labs, instead of relying solely on traditional C2 servers, Astaroth attackers are hosting critical malware configurations within GitHub repositories. This means that if law enforcement or security researchers succeed in taking down their main C2 infrastructure, the Astaroth trojan can simply pull fresh configurations from GitHub and continue running. The malware achieves this by using steganography, hiding configuration information within images that it hosts on the legitimate Microsoft-owned platform.
Targeting Latin America
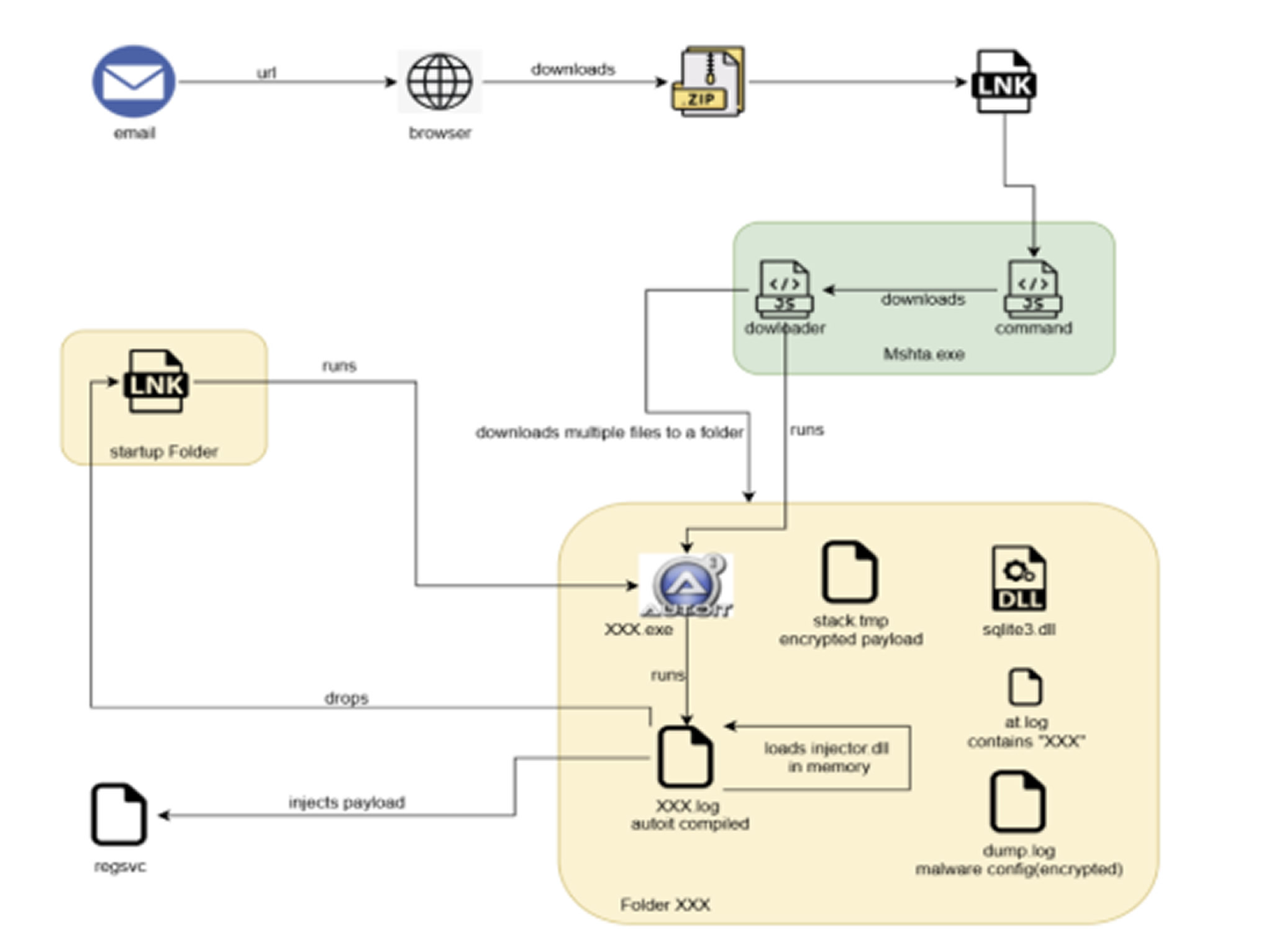
The campaign is primarily focused on Brazil, although Astaroth is known to target financial institutions and cryptocurrency sites across multiple Latin American countries, including Mexico, Argentina, and Chile. The latest attack begins with a phishing email themed around DocuSign, containing a link that downloads a zipped Windows shortcut (.lnk) file.
Executing the .lnk file triggers a complex, multi-stage infection chain involving obfuscated JavaScript, AutoIt scripts, and shellcode. This process ultimately loads and injects the Delphi-based Astaroth malware into a newly created RegSvc.exe process.
Stealing Financial Data
Once running, Astaroth acts as a keylogger and info-stealer. It continuously monitors the victim's active browser window, specifically looking for visits to banking or cryptocurrency websites. If a targeted site is detected, the malware hooks keyboard events to steal credentials and other captured information, which is then transmitted to the attackers using the Ngrok reverse proxy.
To avoid detection, Astaroth is equipped with strong anti-analysis capabilities and automatically shuts down if it detects debugging or security tools such as IDA Pro, Wireshark, or QEMU Guest Agent. Furthermore, the malware includes geofencing checks, ensuring it only runs on machines with a system locale not set to English or the U.S.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.