New ClickFix Malware Campaign Targets macOS Users with Atomic Stealer
Cybersecurity researchers are warning of a new malware campaign targeting macOS users through a social engineering tactic known as ClickFix. The attack delivers a strain of information-stealing malware called Atomic macOS Stealer (AMOS).
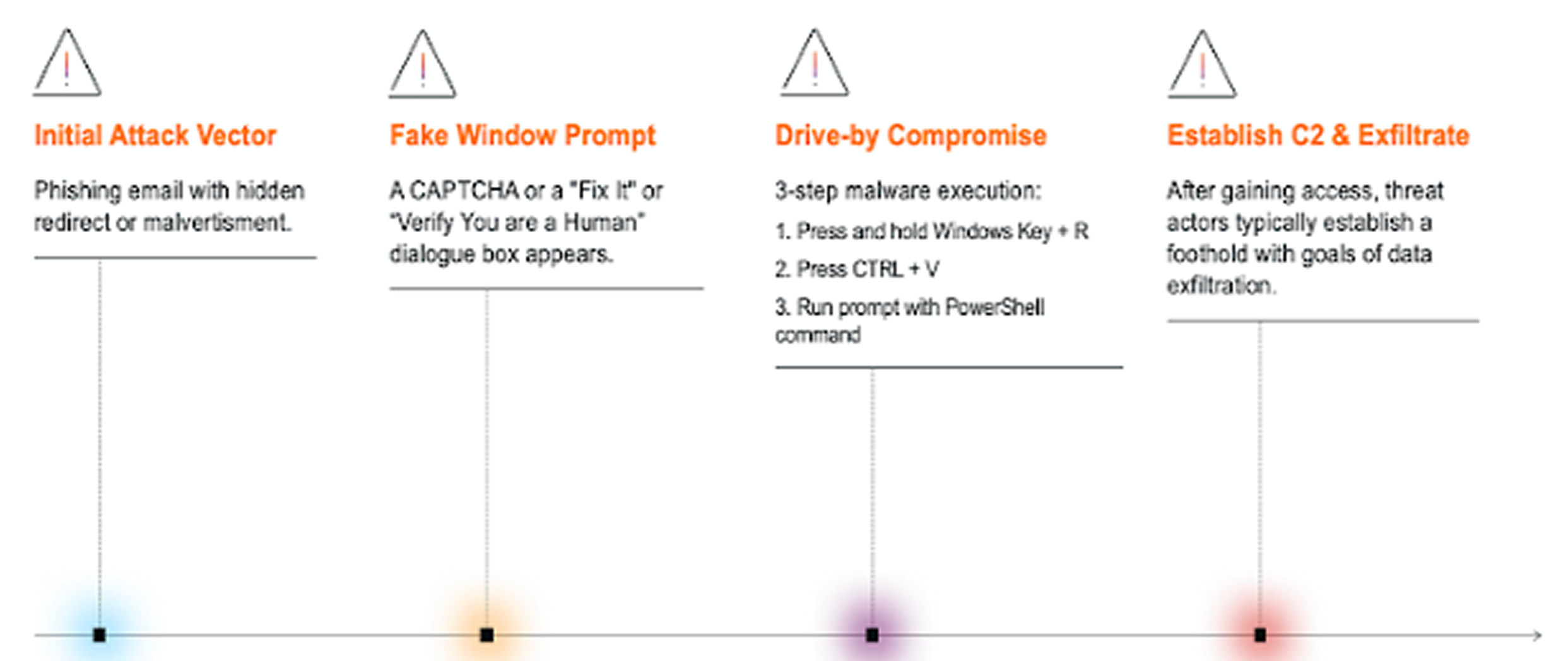
According to a report by CloudSEK, the campaign uses typosquatted domains that impersonate U.S. telecom provider Spectrum to trick users. Koushik Pal, a security researcher at CloudSEK, explained that users visiting these malicious sites are presented with a harmful shell script. This script is designed to collect system credentials, bypass security protections, and download a variant of AMOS for further exploitation.
The campaign appears to be operated by Russian-speaking threat actors, as evidenced by Russian-language comments found in the malware’s source code. The attack begins with a fake Spectrum-branded webpage, hosted on domains such as "panel-spectrum[.]net" or "spectrum-ticket[.]net." These pages prompt users to complete a hCaptcha verification under the pretext of securing their connection.
When users click the “I am human” checkbox, they are shown an error message indicating that the CAPTCHA verification failed. They are then encouraged to proceed with an "Alternative Verification" method.
Clicking this button copies a command to the user’s clipboard and provides tailored instructions based on the operating system. Windows users are prompted to run a PowerShell command, while macOS users are instructed to run a shell script via the Terminal application.
This shell script then prompts the user to enter their system password and proceeds to download the next-stage payload. In this case, it is Atomic Stealer, a known information-stealing malware.
Pal noted several flaws in the campaign's delivery infrastructure, describing the setup as hastily assembled. For example, Linux users were mistakenly served PowerShell commands, and both Windows and Mac users received prompts to press the Windows key, indicating inconsistent platform-specific instructions.
This incident adds to the growing number of attacks using ClickFix, a method that relies on social engineering to bypass security defenses. Threat actors use tactics such as spear phishing, drive-by downloads, and abuse of trusted platforms like GitHub to lure users into executing malicious commands.
The approach often involves redirecting users to fraudulent CAPTCHA verification pages that appear legitimate. These pages deceive users into believing they are completing routine security checks, but in reality, they are executing harmful commands on their systems.
Darktrace highlighted an incident from April 2025 where attackers used ClickFix to download hidden payloads, move laterally within networks, collect system data, and exfiltrate it through HTTP POST requests.
According to Darktrace, ClickFix campaigns are effective because they exploit user behavior. By making users believe they are performing ordinary tasks, attackers achieve initial system access and then extract sensitive data. Other campaigns have employed fake versions of CAPTCHA tools like Google reCAPTCHA and Cloudflare Turnstile, often embedded into legitimate but compromised websites.
These spoofed pages are nearly identical to the real ones, making them highly convincing. They have been used to distribute various malware families, including stealers like Lumma and StealC, as well as remote access tools such as NetSupport RAT.
Daniel Kelley of SlashNext pointed out that today’s internet users are frequently prompted with CAPTCHAs and other security checks. As a result, many instinctively click through them without scrutiny. This tendency, referred to as "verification fatigue," is what attackers rely on to make their scams successful.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



