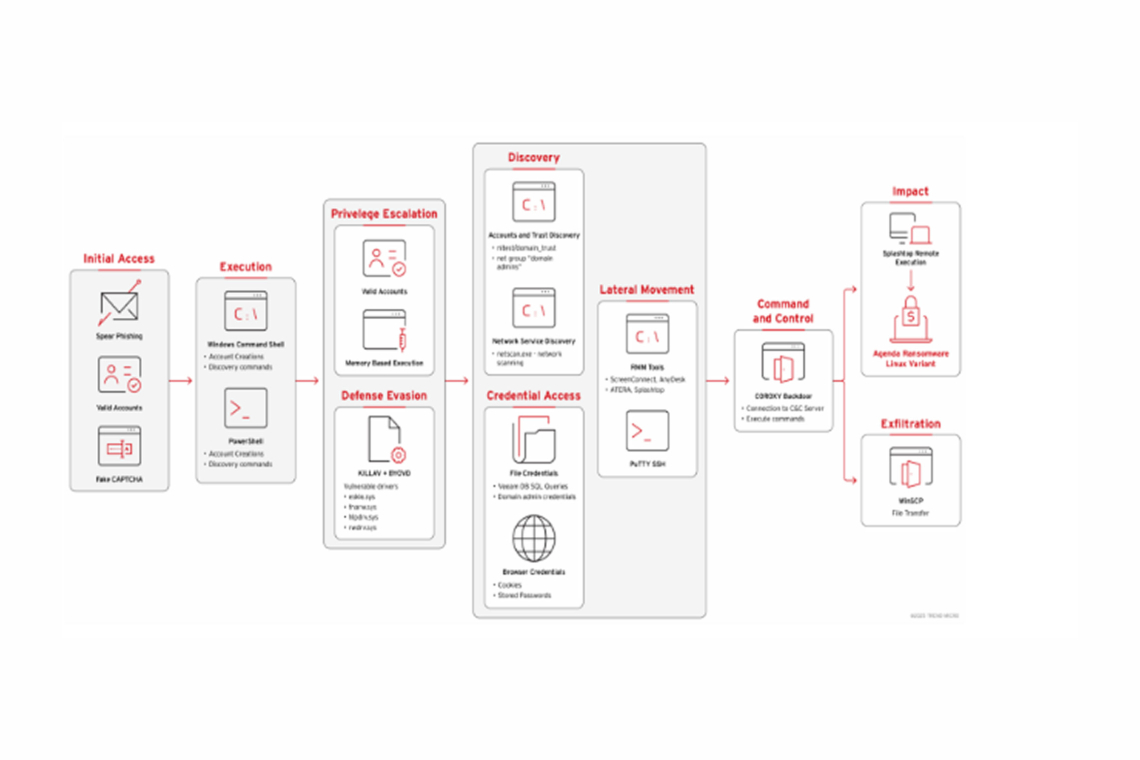
The Qilin ransomware group (also known as Agenda) is utilizing a sophisticated new methodology that deploys Linux ransomware binaries on Windows systems to bypass traditional endpoint detection and response (EDR) solutions. This cross-platform tactic is designed to steal backup credentials, disable endpoint security, and ensure stealthy network traversal.
Cross-Platform Evasion and Stealth
Qilin’s new method challenges security controls that are typically focused on Windows binaries. Attackers use legitimate remote tools such as WinSCP and Splashtop Remote to transfer and execute the Linux ransomware binary on Windows machines. They also abuse remote management software like AnyDesk via ATERA RMM, ScreenConnect, and MeshCentral to maintain persistence and evade detection by masking malicious activity as normal administrative work.
The group also employs Bring Your Own Vulnerable Driver (BYOVD) exploits to disable endpoint protection, and they specifically target Veeam backup credentials to sabotage recovery efforts, highlighting an escalating level of attacker sophistication.
Trend Micro analysts emphasized that this deployment of Linux ransomware on Windows bypasses EDR systems not configured to detect or prevent this specific execution method via remote management channels.
Initial Access and Reconnaissance
The Qilin ransomware operation has been highly active since 2022, becoming one of the most prolific Ransomware as a Service (RaaS) groups in 2025.
Initial access is often gained through fake Google CAPTCHA pages hosted on Cloudflare R2. These pages trick users into running malicious JavaScript that launches a multistage payload system. This system delivers info-stealers that harvest credentials, tokens, and cookies, allowing Qilin to bypass multi factor authentication (MFA) and move laterally using valid user sessions.
Once inside, attackers conduct extensive reconnaissance using tools like ScreenConnect and the NetScan utility to map the network and gather information about domain trusts and administrator accounts.
Disabling Defenses and Data Theft
To disable defenses and move across the network quietly, Qilin uses advanced anti analysis techniques. They deploy executables that load a signed driver, eskle.sys, which performs checks for virtual machines and debuggers while actively killing security processes. This driver's signature points to a repurposed Chinese game related vendor, suggesting it may be a modified game cheat driver.
For lateral movement, the attackers use renamed PuTTY binaries to SSH into Linux hosts, confirming a true cross platform operation. They also create a distributed C2 network by planting multiple COROXY SOCKS proxy instances across trusted application folders (like Veeam and Adobe), hiding malicious tunnels within normal application traffic and ensuring redundant communication.
Crucially, the attackers target the Veeam backup infrastructure by executing PowerShell scripts that extract and decrypt stored credentials from SQL databases. This provides them with highly privileged credentials for domain controllers and other critical systems, effectively blocking victim recovery.
The Qilin ransomware operation combines BYOVD style evasion, distributed SOCKS proxies, and legitimate remote tools to achieve resilient, low noise control and cross platform encryption capability, fundamentally undermining traditional endpoint defenses.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.