CISA Adds GitHub Action Vulnerability to Known Exploited List Amid Supply Chain Attack
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity vulnerability linked to the supply chain compromise of the GitHub Action tj-actions/changed-files to its Known Exploited Vulnerabilities (KEV) catalog. This move follows reports that attackers injected malicious code into the GitHub Action, allowing them to steal sensitive information from affected repositories.
The vulnerability, tracked as CVE-2025-30066, has a CVSS severity score of 8.6. It allows remote attackers to access sensitive data by exploiting the compromised GitHub Action’s logs. This breach poses a significant risk, as attackers could extract AWS access keys, GitHub personal access tokens (PATs), npm tokens, and private RSA keys from workflows using the compromised action.
How the Attack Unfolded
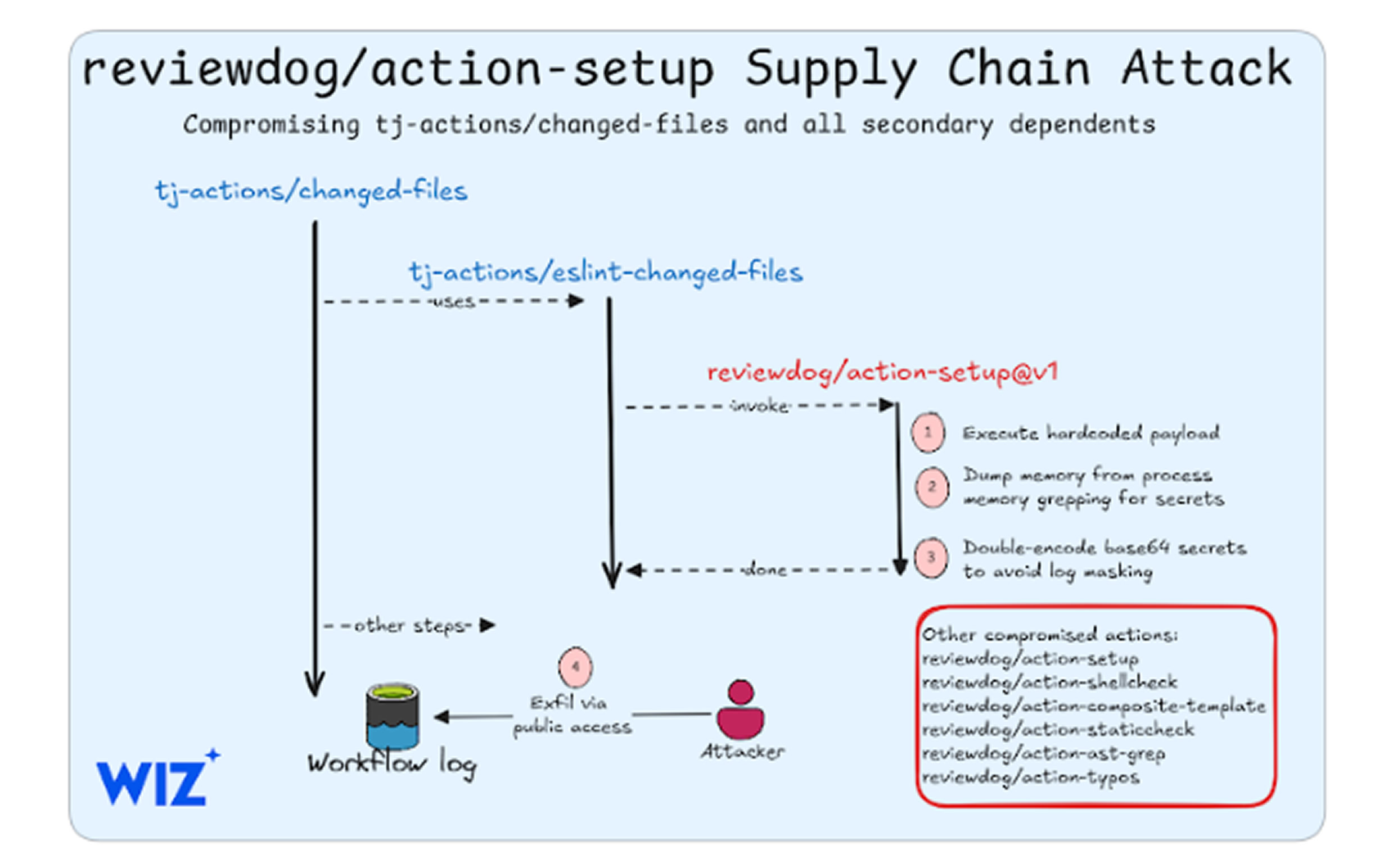
Cloud security firm Wiz revealed that this attack was likely part of a cascading supply chain compromise. Security researchers discovered that attackers first compromised the reviewdog/action-setup@v1 GitHub Action before using it to infiltrate tj-actions/changed-files.
The reviewdog action was compromised on March 11, 2025, and the breach of tj-actions/changed-files occurred before March 14, 2025. Attackers injected a Base64-encoded payload into a script file (install.sh), which was executed during CI/CD workflows. This payload exposed secrets stored in repository logs, allowing attackers to access sensitive credentials without immediate detection.
The attack was made possible by a compromised GitHub Personal Access Token (PAT), which granted unauthorized modification rights to the affected repository. This allowed the attacker to update the v1 tag with malicious code from a forked version of the repository, ensuring that any project using the action would unknowingly execute the compromised script.
Wider Security Implications
One of the factors that contributed to the success of this attack was the large contributor base of the reviewdog GitHub organization. Researchers noted that contributors were being added automatically, increasing the risk of unauthorized access. This suggests that either an existing contributor was compromised, or the attacker gained access by posing as a legitimate contributor.
This incident underscores the risks of software supply chain attacks, where attackers manipulate open-source components to compromise multiple downstream users. Given the widespread adoption of GitHub Actions in CI/CD pipelines, such breaches can have far-reaching consequences across multiple organizations.
Mitigation and Next Steps
CISA has urged all affected users and federal agencies to update tj-actions/changed-files to version 46.0.1 by April 4, 2025, to mitigate active threats. However, due to the nature of the attack, security experts warn that there is a high risk of re-occurrence if additional measures are not implemented.
To strengthen security, organizations should:
- Replace affected GitHub Actions with trusted alternatives.
- Conduct thorough audits of past CI/CD workflows for any suspicious activity.
- Rotate any compromised secrets to prevent further unauthorized access.
- Pin GitHub Actions to specific commit hashes rather than version tags to reduce the risk of similar attacks in the future.
This latest incident highlights the increasing risks to software supply chains and reinforces the need for robust security measures when managing CI/CD pipelines and open-source dependencies. As attackers continue to target automation tools and software repositories, organizations must remain vigilant and proactively secure their development environments.


