Orange Cyberdefense’s CSIRT has reported that hackers exploited two vulnerabilities in Craft CMS
to breach servers and steal sensitive data. The vulnerabilities, identified as CVE-2025-32432 and CVE-2024-58136, involve a remote code execution (RCE) flaw in Craft CMS and an input validation issue within the Yii framework used by the CMS.
Orange's investigation uncovered that the attackers used these flaws to compromise servers and upload a PHP file manager. The breach began with the exploitation of CVE-2025-32432, where the attackers sent a crafted request with a “return URL” saved in a PHP session file. They then leveraged CVE-2024-58136 in the Yii framework by sending a malicious JSON payload, which executed PHP code from the session file, allowing them to install a PHP-based file manager and further compromise the server.
Both vulnerabilities have been patched. CVE-2025-32432 was addressed in versions 3.9.15, 4.14.15, and 5.6.17 of Craft CMS, while Yii fixed its vulnerability with the release of Yii 2.0.52 on April 9th.
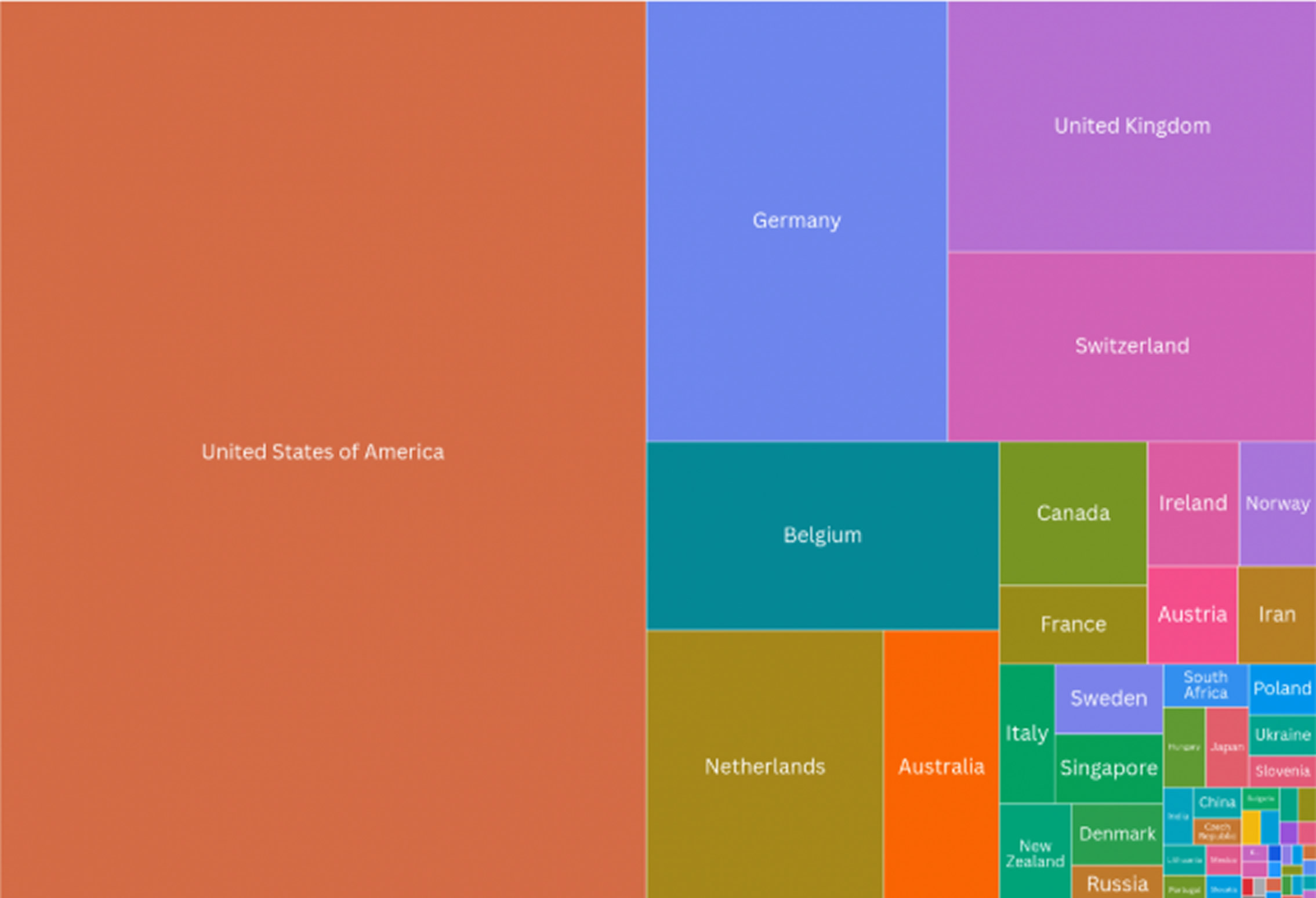
The investigation also revealed nearly 35,000 Craft CMS instances in the Onyphe asset database. Using a nuclei template, researchers identified around 13,000 vulnerable instances linked to approximately 6,300 IP addresses, mainly in the U.S. Further analysis flagged around 300 potentially compromised instances based on file patterns.
Indicators of compromise (IoCs) related to the attacks exploiting these vulnerabilities have been released by Orange Cyberdefense’s CSIRT.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.


