Cyble Research and Intelligence Labs (CRIL) has uncovered a malicious crypto phishing campaign involving over 20 fraudulent apps on the Google Play Store targeting crypto wallet
users. These apps impersonate popular wallet platforms to trick users into revealing their sensitive 12-word mnemonic phrases, allowing attackers to gain control of their digital assets.
Fake Apps Mimic Trusted Crypto Wallets
CRIL’s report highlights that these phishing apps pretended to be well-known crypto wallets such as SushiSwap, PancakeSwap, Hyperliquid, and Raydium. They featured polished, realistic user interfaces closely resembling the genuine platforms. When users opened the fake apps, they were asked to enter their mnemonic phrase, a key piece of information needed to access real wallets.
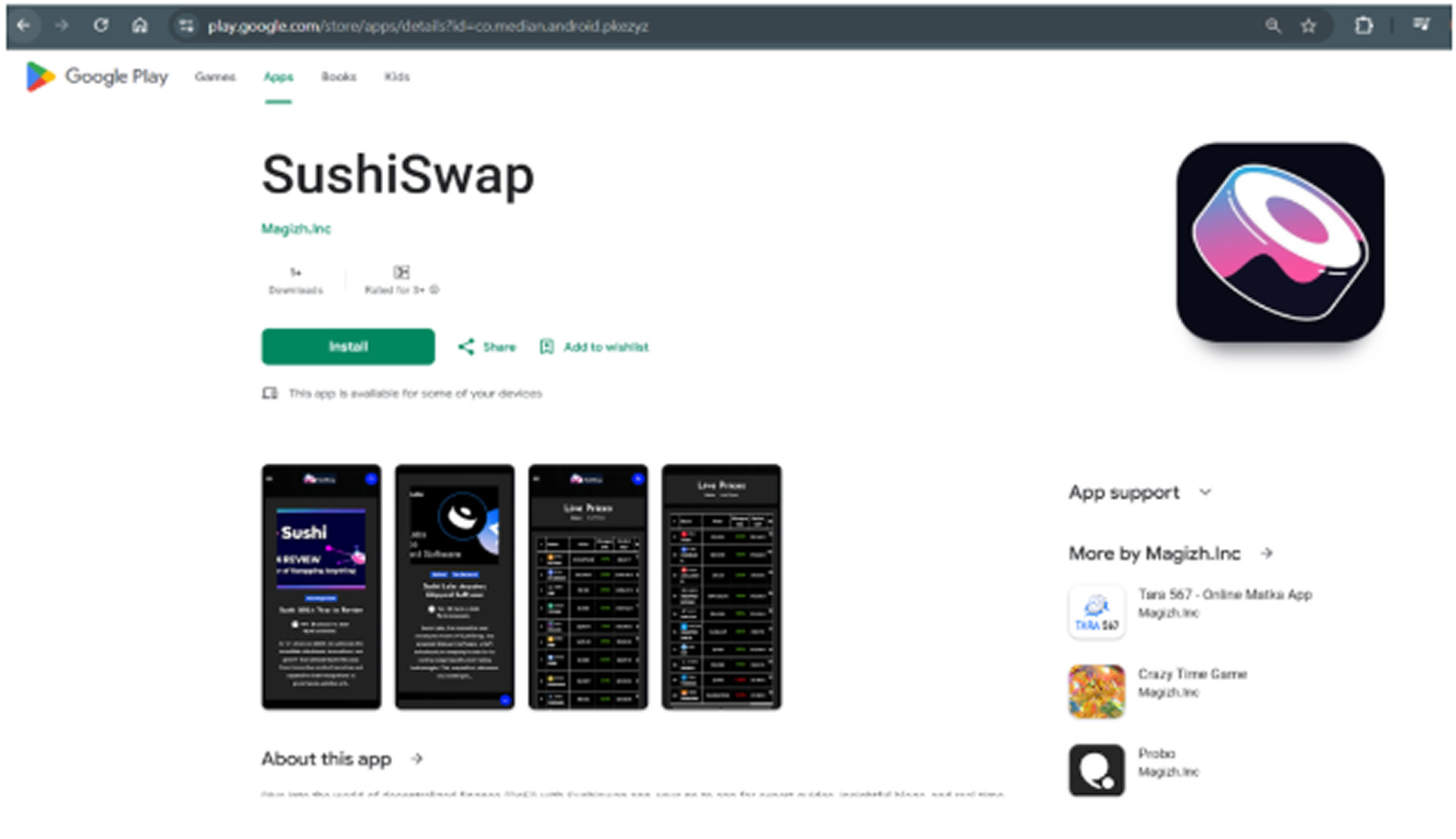
Available Directly on the Play Store
Unlike typical malicious apps distributed through shady channels, these apps were published on the official Google Play Store, giving them an appearance of legitimacy. The attackers exploited compromised or repurposed developer accounts, some with a history of legitimate apps boasting over 100,000 downloads.
Phishing Techniques and Distribution Methods
Many of the phishing apps embedded malicious URLs within their privacy policies. They shared similar package names and descriptions, suggesting coordination by a single or connected group of attackers. These apps were built using frameworks like Median, which allows quick conversion of websites into Android apps. Often, phishing sites were loaded inside the apps via WebView components. For example, one URL, hxxps://pancakefentfloyd.cz/api.php, mimicked PancakeSwap and asked users for their mnemonic phrases. Technical analysis revealed that the IP address hosting one phishing domain (94.156.177.209) was linked to over 50 other phishing domains, showing the campaign’s scale and organization.
Identified Malicious Apps Include:
- Pancake Swap (co.median.android.pkmxaj)
- Suiet Wallet (co.median.android.ljqjry)
- Hyperliquid (co.median.android.jroylx)
- Raydium (co.median.android.yakmje)
- BullX Crypto (co.median.android.ozjwka)
- OpenOcean Exchange (co.median.android.ozjjkx)
- Meteora Exchange (co.median.android.kbxqaj)
- SushiSwap (co.median.android.pkezyz)
Two additional apps, Raydium (cryptoknowledge.rays) and PancakeSwap (com.cryptoknowledge.quizzz), used different naming but linked to the same phishing privacy policy hosted on TermsFeed.
A Coordinated and Large-Scale Phishing Operation
This campaign is not a random effort by low-level scammers. The infrastructure behind these apps, with dozens of associated phishing domains, points to a well-planned operation targeting the growing crypto user base. By impersonating trusted apps on the official Play Store, attackers exploited users’ trust and bypassed standard security measures.
Once users provide their mnemonic phrases through these phishing apps, attackers gain instant access to their wallets and can transfer funds, often permanently. Unlike traditional banking, crypto transactions usually cannot be reversed or recovered.
How to Protect Yourself
To guard against these crypto phishing scams, users should only download apps from verified developers, avoid apps that ask for sensitive details like mnemonic phrases, and carefully check app ratings and authenticity, especially for new releases. Enabling Google Play Protect, using trusted antivirus programs, turning on multi-factor authentication, and activating biometric security features add extra protection. Users should also avoid clicking suspicious links received via SMS or email.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.