Cisco has addressed a critical vulnerability in its Identity Services Engine (ISE) that could let unauthenticated attackers perform malicious actions.
The flaw, identified as CVE-2025-20286 with a CVSS score of 9.9, affects cloud deployments of Cisco ISE on platforms such as AWS, Microsoft Azure, and Oracle Cloud Infrastructure. It allows remote attackers without authentication to access sensitive information, make limited administrative changes, alter configurations, or disrupt services.
This vulnerability stems from the way Cisco ISE generates credentials during cloud deployments. When using the same software version and cloud platform, the system creates identical login credentials across multiple instances. This flaw could allow an attacker to extract credentials from one instance and use them to access other deployments sharing the same version and platform setup. As a result, attackers could gain unauthorized access, modify settings, or interfere with system operations.
Cisco explained that the issue arises from improper credential generation during deployment, which leads to the reuse of credentials across different environments. If an attacker retrieves credentials from one cloud-based Cisco ISE instance, they can potentially use those to access others through unsecured ports. This could expose sensitive data and grant the attacker limited control over affected systems.
The vulnerability was discovered by Kentaro Kawane from GMO Cybersecurity. Cisco’s Product Security Incident Response Team (PSIRT) confirmed that proof-of-concept code exists but noted there is no evidence of the vulnerability being exploited in real-world attacks.
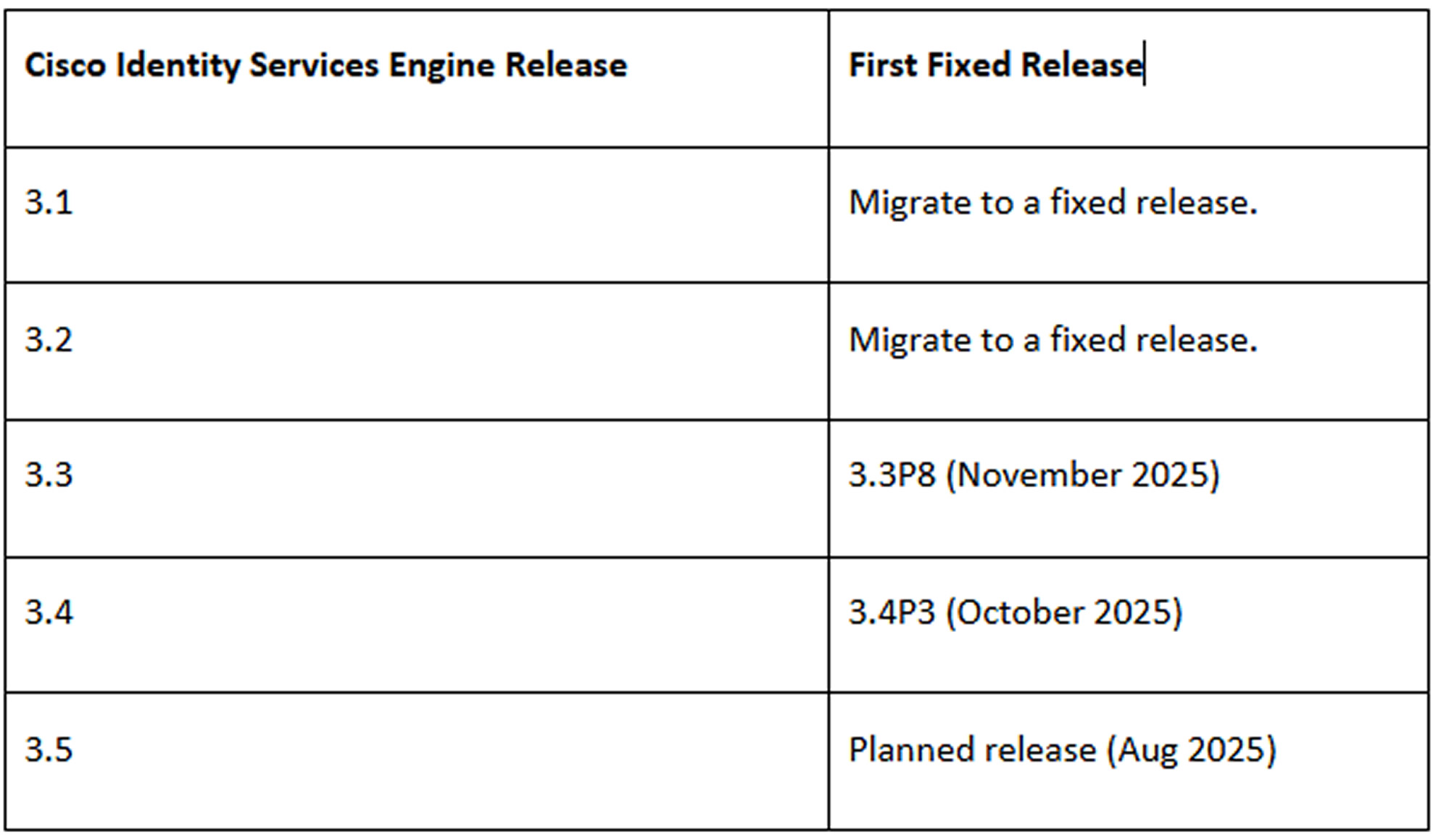
The flaw impacts the following versions:
There is no direct workaround for the Cisco Identity Services Engine (ISE) cloud vulnerability, but Cisco has outlined key mitigations administrators can implement.
To reduce exposure, access should be restricted to trusted source IP addresses. This can be done through cloud security groups or directly within the Cisco ISE interface.
For new deployments, Cisco advises running the application reset-config ise command on the primary node hosted in the cloud. This command regenerates fresh credentials by resetting the system to factory settings. However, administrators should be aware that restoring from a backup will also restore the original credentials, which may still be vulnerable.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



