Threat actors are actively exploiting a critical vulnerability, tracked as CVE-2025-5947 (CVSS score 9.8), in the Service Finder WordPress theme’s Bookings plugin (versions 6.0 and earlier).
Critical Authentication Bypass
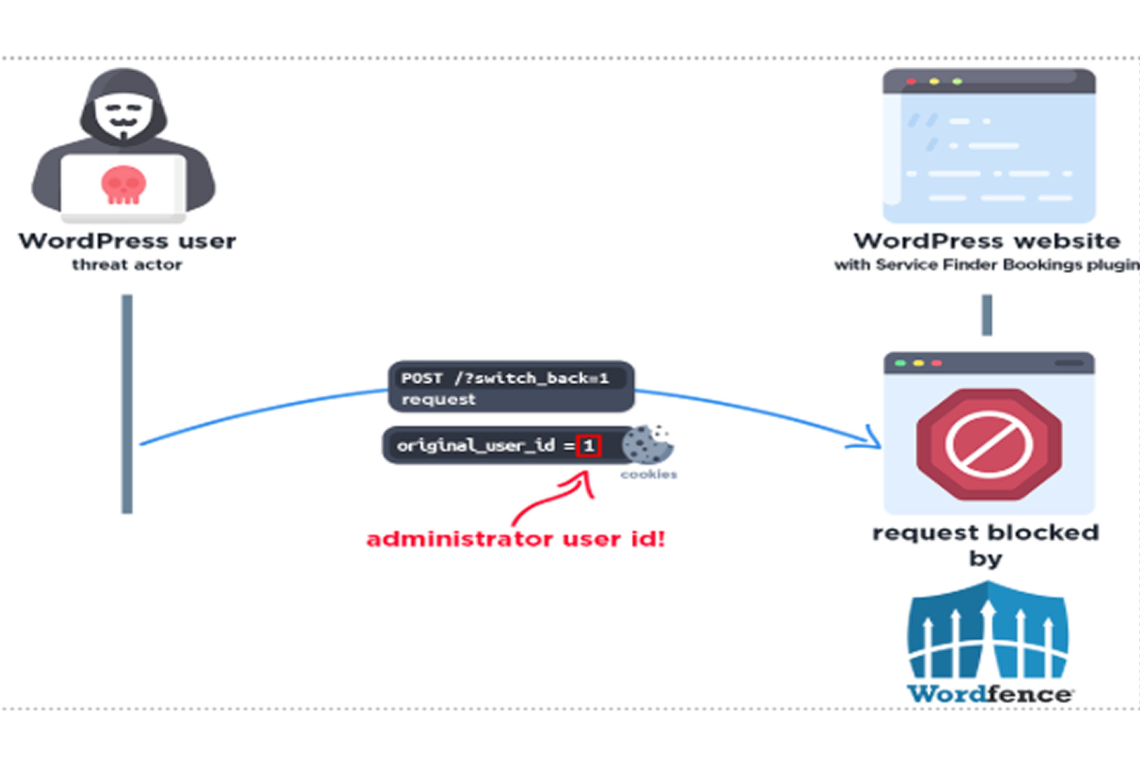
This flaw is an authentication bypass issue caused by the plugin's failure to properly validate a user's cookie value within the service_finder_switch_back() function. This severe lapse allows an unauthenticated attacker to log in as any user, including the site administrator, leading to full site compromise.
The vulnerability was publicly disclosed on July 31, 2025, after the vendor released a patched version on July 17. However, cybersecurity firm Wordfence warns that active exploitation began the very next day, August 1, 2025. Wordfence's firewall has already blocked over 13,800 exploit attempts targeting this flaw.
Mitigation and Warning
Exploiting this flaw allows attackers to completely take over any account, giving them administrative control to clear their tracks and potentially infect other vulnerable WordPress sites.
Although there are no clear, easily identifiable signs of compromise besides log requests containing the 'switch_back' parameter, Wordfence strongly recommends that site owners review their log files for requests originating from five specific malicious IP addresses currently known to be targeting the plugin. Users running a vulnerable version of the Service Finder Bookings plugin must update immediately to the patched version.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.