Cybersecurity researchers have detailed an active malware campaign named Stealit that is exploiting Node.js's Single Executable Application (SEA) feature for payload distribution. Select versions of the malware also use the open-source Electron framework to deliver the code.
Distribution and Pricing
Fortinet FortiGuard Labs assesses that the malware is spread through counterfeit installers for games and VPN applications uploaded to file-sharing sites like Mediafire and Discord. The SEA feature allows Node.js applications to run as a standalone executable even on systems without the Node.js runtime installed. This approach is effective because it removes the need for pre-installed dependencies.
The threat actors operate a dedicated website where they market their "professional data extraction solutions" through various subscription plans. The malware offerings include a Remote Access Trojan (RAT) for Android and a stealer for Windows. Pricing ranges from weekly for the Windows Stealer up to for a lifetime license for the Android RAT. The RAT boasts features such as file extraction, webcam control, live screen monitoring, and ransomware deployment.
Attack Mechanics and Evasion
The fake executables contain an installer that first performs anti-analysis checks to ensure it is not running in a virtual or sandboxed environment. A key step involves writing a Base64-encoded, 12-character alphanumeric authentication key to the %temp%\cache.json file. This key is used to authenticate with the Command-and-Control (C2) server and allows subscribers to monitor and control their victims.
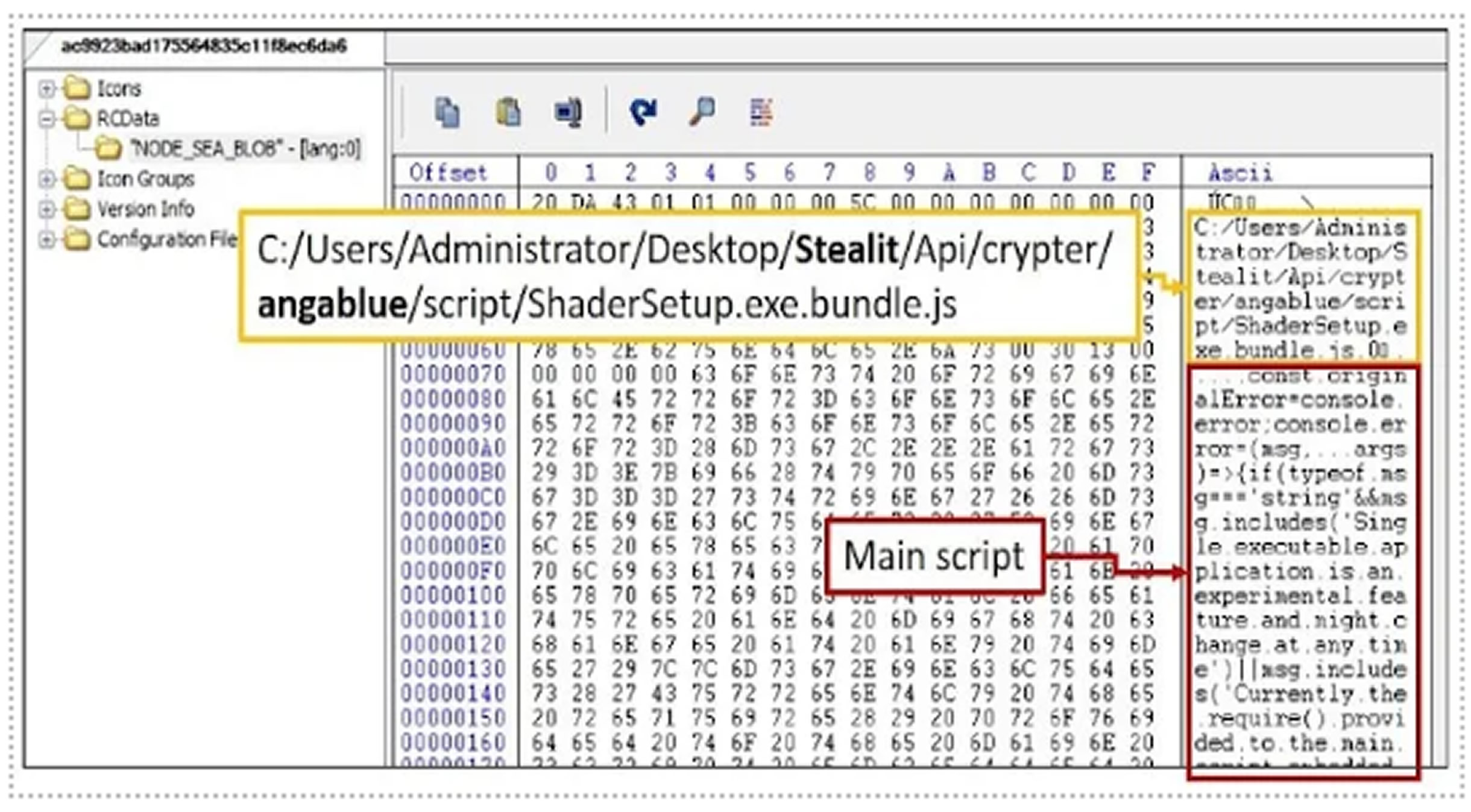
The malware is engineered to configure Microsoft Defender Antivirus exclusions for the folder containing the downloaded components, helping it evade detection. Stealit uses three main executables to perform different functions:
- save_data.exe: If running with elevated privileges, it drops a tool to extract information from Chromium-based browsers.
- stats_db.exe: Designed to steal data from messengers (Telegram, WhatsApp), cryptocurrency wallets (Atomic, Exodus), and game launchers (Steam, Epic Games).
- game_cache.exe: Sets up persistence, communicates with the C2 to stream the victim's screen in real-time, executes commands, transfers files, and can change desktop wallpaper.
Fortinet notes that by using the experimental Node.js SEA feature, which is still under development, the threat actors may be exploiting its novelty to catch existing security applications and malware analysts off guard.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



