The state sponsored Iranian hacker group MuddyWater has launched a campaign targeting over 100 government entities across the Middle East and North Africa. The attacks primarily deployed version 4 of their sophisticated malware, the Phoenix backdoor.
Campaign Details and Phishing Lures
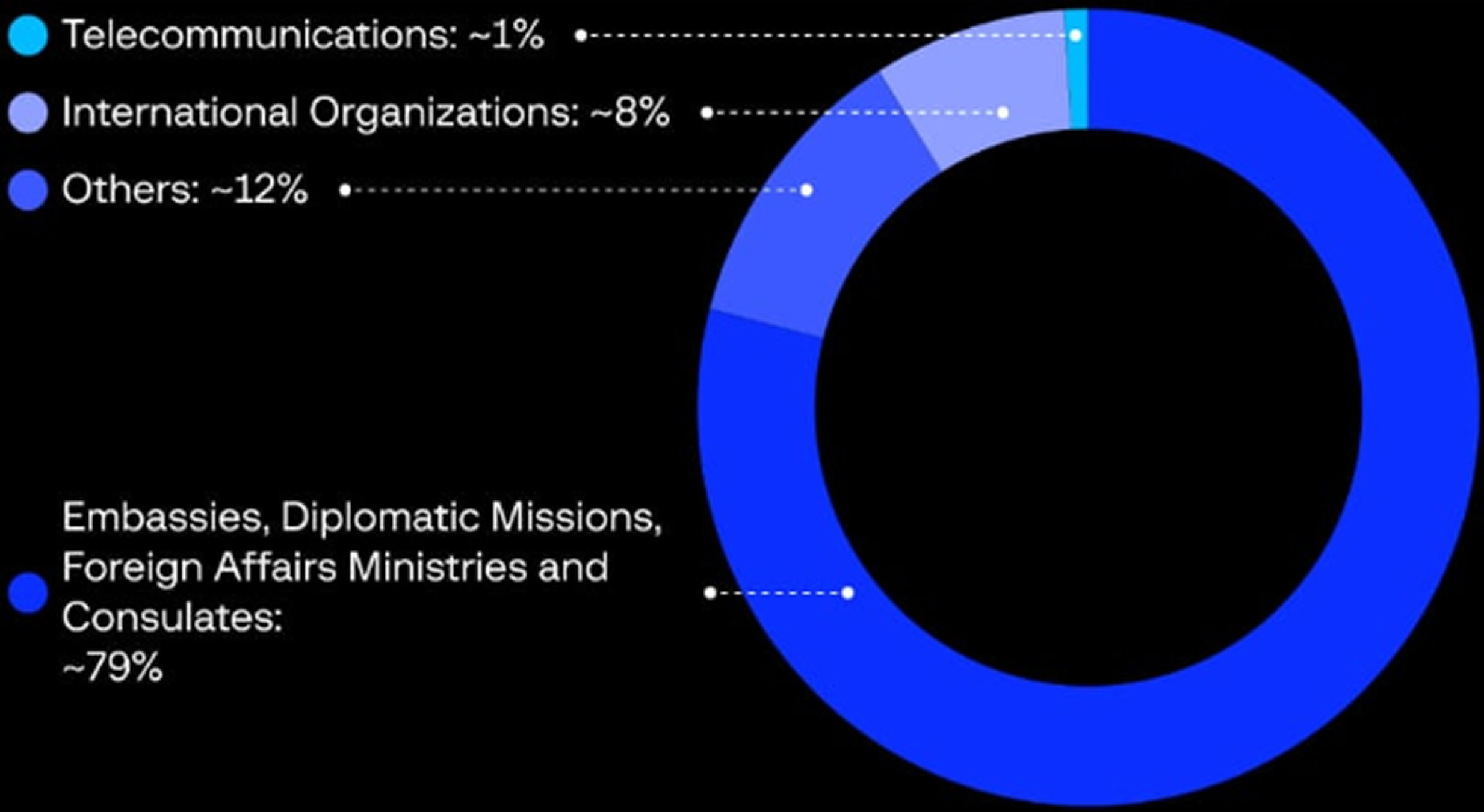
The campaign began around August 19 with a wave of phishing emails sent from a compromised account accessed through the NordVPN service. MuddyWater, also known as Static Kitten and Mercury, focused its attacks on embassies, diplomatic missions, foreign affairs ministries, and consulates in the targeted regions, Group IB reports.
The hackers reverted to an older, proven technique: delivering malware through malicious Microsoft Word documents containing macro code. The emails attached these documents, instructing recipients to "enable content" in Microsoft Office. This action triggers a VBA macro that writes the FakeUpdate malware loader onto the disk.
The Phoenix Backdoor and Toolset
The FakeUpdate loader then decrypts and deploys the Phoenix backdoor, which is an embedded, AES encrypted payload. The malware establishes persistence by modifying Windows Registry entries and uses a new COM based mechanism in version 4.
Once active, the Phoenix backdoor gathers system information and connects to its command and control (C2) server via WinHTTP to poll for commands. These commands allow the hackers to execute a shell, upload and download files, and adjust the sleep interval time, giving them complete remote control.
In addition to the Phoenix backdoor, MuddyWater used a custom infostealer designed to exfiltrate database information, credentials, and master keys from popular browsers including Chrome, Opera, Brave, and Edge. The researchers also discovered legitimate remote monitoring and management tools like PDQ utility and Action1 RMM on the C2 infrastructure, tools previously associated with Iranian hackers. Group IB attributes the attacks to MuddyWater with high confidence based on the specific malware, coding techniques, and targeted patterns seen in past campaigns
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



