A new malicious campaign, dubbed Operation MotorBeacon, is targeting Russia’s automobile and e-commerce sectors using a previously unknown .NET malware called CAPI Backdoor.
Attack Details
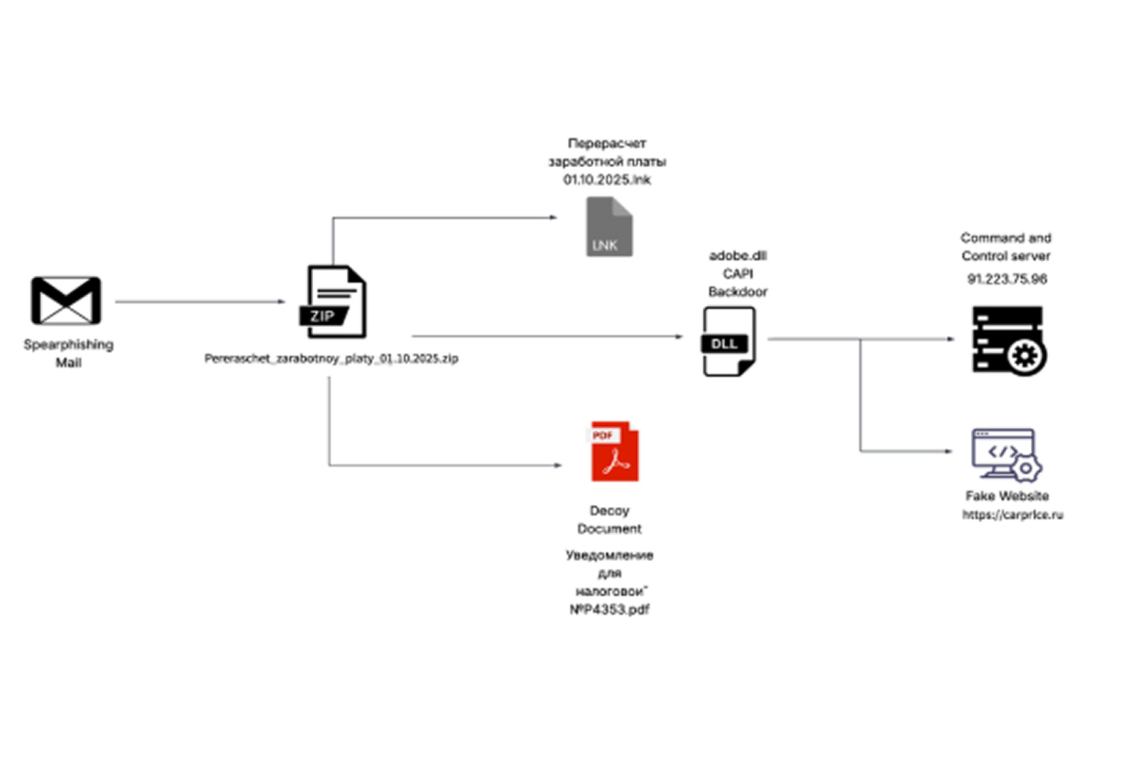
Cybersecurity researchers at Seqrite Labs uncovered the operation, which begins with phishing emails. These emails contain a ZIP archive misleadingly titled "Payroll Recalculation as of Oct 1, 2025." Inside the archive is a malicious LNK file that executes a hidden .NET implant using rundll32.exe. The archive also contains a decoy PDF notification that falsely poses as a tax update notice, detailing an increase in the PIT (Personal Income Tax) rate.
The LNK file launches the CAPI Backdoor DLL, checks for administrative privileges and security tools, and then opens the decoy tax document before connecting to its Command and Control (C2) server.
CAPI Backdoor Capabilities
CAPI Backdoor is a sophisticated stealer that supports multiple malicious functions, including:
- Data Theft Stealing browser data from Chrome, Edge, and Firefox.
- Surveillance Taking screenshots of the infected system.
- System Profiling Gathering detailed system information and listing folders.
- Evasion Running checks for virtual machines and analysis environments.
To ensure long-term access, the malware establishes persistence by creating a scheduled task and placing a LNK file in the Windows Startup folder to automatically launch the backdoor DLL from the user's Roaming directory upon login. The campaign has been active since October 3, using a fake domain that closely resembles a legitimate Russian car commerce site, confirming the sector-specific targeting. The CAPI Backdoor functions as both an information stealer and a persistent backdoor for future malicious activities.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.