The North Korean threat actor behind the Contagious Interview campaign is aggressively refining its toolset by merging the functionality of its key malware programs, BeaverTail and OtterCookie. Cisco Talos reports that recent operations show the two malware families are growing closer, with OtterCookie gaining new features for keylogging and taking screenshots.
Evolving Toolset and Tactics
This group known by various monikers including Famous Chollima and UNC5342, is recognized for its elaborate recruitment scams. These campaigns involve hackers impersonating legitimate hiring entities to trick job seekers into installing information-stealing malware under the guise of a technical assessment.
This development follows recent discoveries by Google and Mandiant that the threat actor is using EtherHiding, a technique that leverages BNB Smart Chain or Ethereum blockchains to host and fetch next-stage payloads. This marks the first time a nation-state actor has been documented using decentralized infrastructure as a resilient Command and Control (C2) mechanism.
The New OtterCookie v5
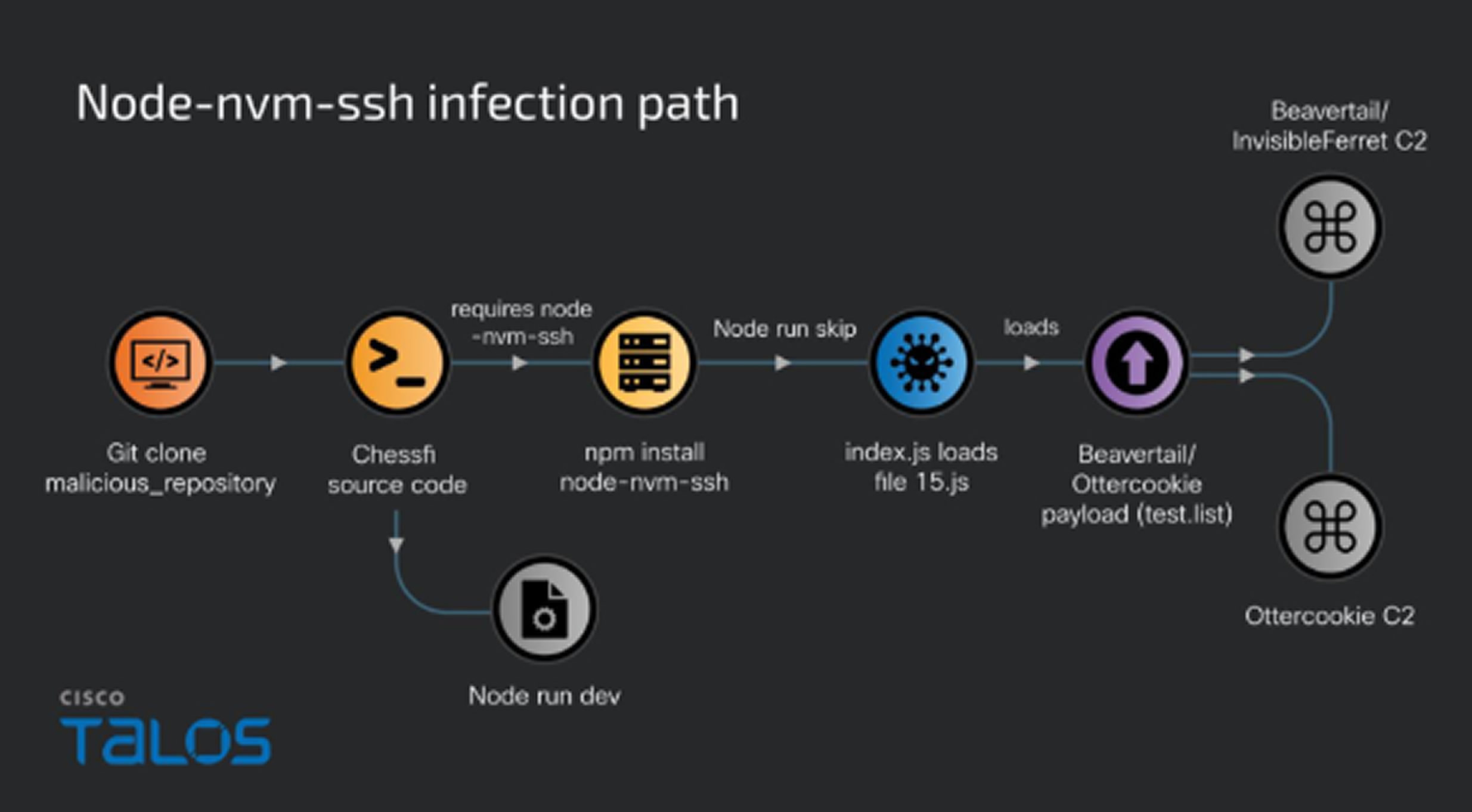
The activity detected by Cisco Talos involved a system in Sri Lanka, likely infected after a user downloaded a trojanized Node.js application called Chessfi from Bitbucket as part of a fake interview. The malicious software contained a dependency published to the official npm repository, which triggered the attack.
Further analysis of the malware used in this attack revealed it shared characteristics of both BeaverTail and OtterCookie, effectively blurring the lines between the two. The updated version, codenamed OtterCookie v5, now incorporates new keylogging and screenshotting modules that use legitimate npm packages to capture keystrokes and take images, exfiltrating the data to the C2 server.
The new modular program has evolved from basic data-gathering to a comprehensive tool for data theft and remote command execution. It includes functions similar to BeaverTail, such as:
- Enumerating browser profiles and extensions.
- Stealing data from web browsers and cryptocurrency wallets, specifically targeting extensions like MetaMask and Phantom.
- Installing AnyDesk for persistent remote access.
- Downloading a Python backdoor called InvisibleFerret.
Other modules include a remote shell for receiving commands and a file uploading module that systematically searches drives for sensitive files matching patterns like "metamask," "bitcoin," and "phrase," uploading them to the C2 server. The constant evolution and merging of these tools underscore the group's commitment to building highly effective, sophisticated espionage platforms.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



