A China-linked advanced persistent threat (APT) group, Salt Typhoon (also known by names like Earth Estries and FamousSparrow), compromised a European telecom firm in July 2025 by exploiting a vulnerability in a Citrix NetScaler Gateway for initial access.
Intrusion and Tactics
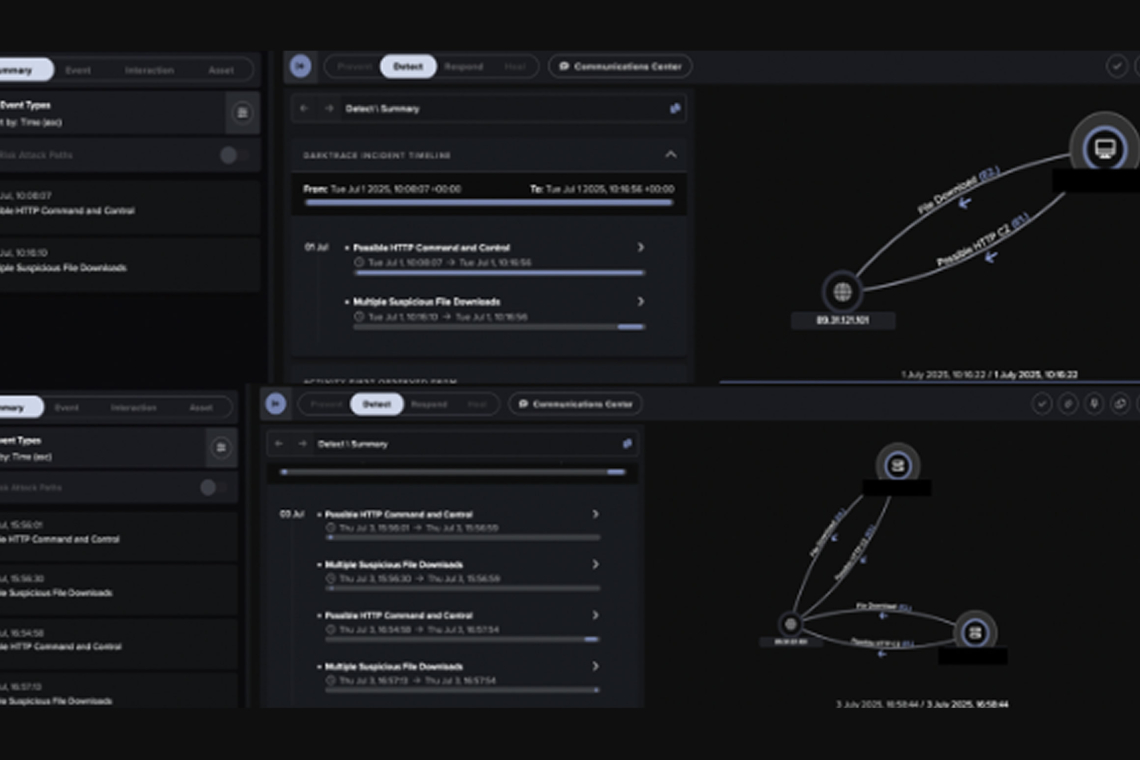
The cyberespionage activity was detected by Darktrace, who noted the attack's tactics were consistent with those used by Salt Typhoon, a group previously identified in late 2024 for targeting telecommunications companies globally. A senior White House official had previously revealed that this campaign had breached firms in dozens of countries, including at least eight US telecommunications firms.
The attackers likely started the intrusion by exploiting the Citrix NetScaler Gateway appliance in the first week of July 2025. From there, the threat actor pivoted to the client’s Citrix Virtual Delivery Agent (VDA) hosts, suggesting a focus on deep network access. The initial access activities were routed through an endpoint possibly associated with the SoftEther VPN service, indicating deliberate infrastructure obfuscation from the start.
Evasion and Backdoor Deployment
To maintain stealth and evade detection, the nation-state actors deployed the SNAPPYBEE (Deed RAT) backdoor. They achieved this through DLL sideloading, a technique that abuses legitimate antivirus executables from vendors like Norton and Bkav.
The attackers used LightNode VPS servers for their Command and Control (C2) communication, relying on HTTP and an unknown TCP protocol to avoid security monitoring. Darktrace's AI successfully identified and mitigated the intrusion before the attackers could escalate their activities further. The incident underscores the necessity of moving beyond traditional, signature-based security to focus on detecting subtle, unusual behaviors that characterize advanced threat groups like Salt Typhoon.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.