Hackers compromise servers, networks, or software—accounted for 60% of total stolen funds, while the rest resulted from smart contract vulnerabilities
Hacks and exploits
The cryptocurrency industry continues to face significant cybersecurity threats, with both centralized exchanges and decentralized finance (DeFi) platforms being prime targets for hackers. In 2023, multiple high-profile breaches resulted in substantial financial losses, including the Mixin Network hack in September, which led to a $200 million loss, and the Euler Finance exploit in March, which drained $197 million. According to blockchain intelligence firm TRM Labs, there were 160 reported hacks as of November—similar to 2022 in frequency but significantly lower in total financial impact.
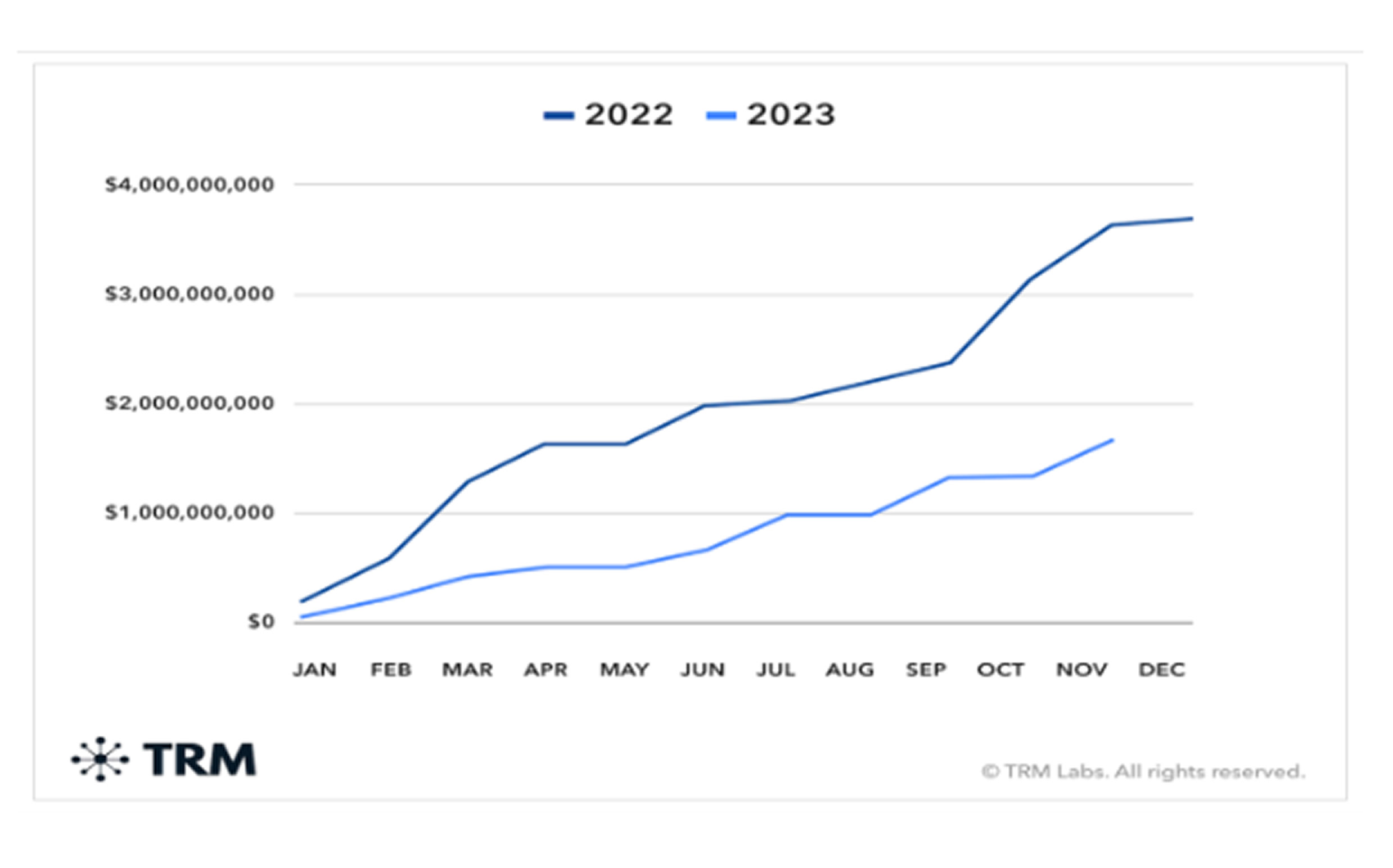
Cybercriminals managed to steal $1.7 billion in cryptoassets, a sharp decline from the previous year, which experts attribute to improved security measures, increased law enforcement intervention, and stronger industry-wide collaboration. However, infrastructure attacks—where hackers compromise servers, networks, or software—accounted for 60% of total stolen funds, while the rest resulted from smart contract vulnerabilities, code exploits, and protocol attacks. Notably, the KyberSwap hack in November introduced a new layer of cyber extortion, with the attacker demanding full control over the decentralized exchange in exchange for returning $50 million in stolen assets, a situation that remains unresolved.
As cyber threats in the crypto space persist, users and organizations must prioritize robust security strategies to safeguard digital assets. Cybersecurity experts recommend minimizing exposure on centralized exchanges, as they remain prime targets for attackers, and instead securing funds in hardware wallets or other cold storage solutions. Additionally, regular smart contract audits, multi-factor authentication (MFA), and network security enhancements can help mitigate risks associated with DeFi protocols. With threat actors continuously refining their attack techniques, the industry must remain proactive in strengthening cybersecurity defenses to counter evolving exploits and protect the integrity of blockchain ecosystems.
Scam
Crypto scams continue to pose a significant cybersecurity challenge, encompassing various deceptive tactics such as exit scams, investment fraud, and malicious smart contracts. These schemes are often multi-layered, combining elements like investment fraud and romance scams to maximize deception. Given the bullish trend in the Bitcoin and crypto market this year, one might expect scammer activity to surge. However, the first half of 2023 saw a notable decline in scam-related earnings. According to blockchain analytics firm Chainalysis, crypto scammers amassed $3.3 billion less in 2023 compared to the previous year, totalling just over $1 billion. This downturn is largely due to the disappearance of two major fraudulent investment platforms, VidiLook and Chia Tai Tianqing Pharmaceutical Financial Management, which had previously siphoned off significant amounts from unsuspecting investors. 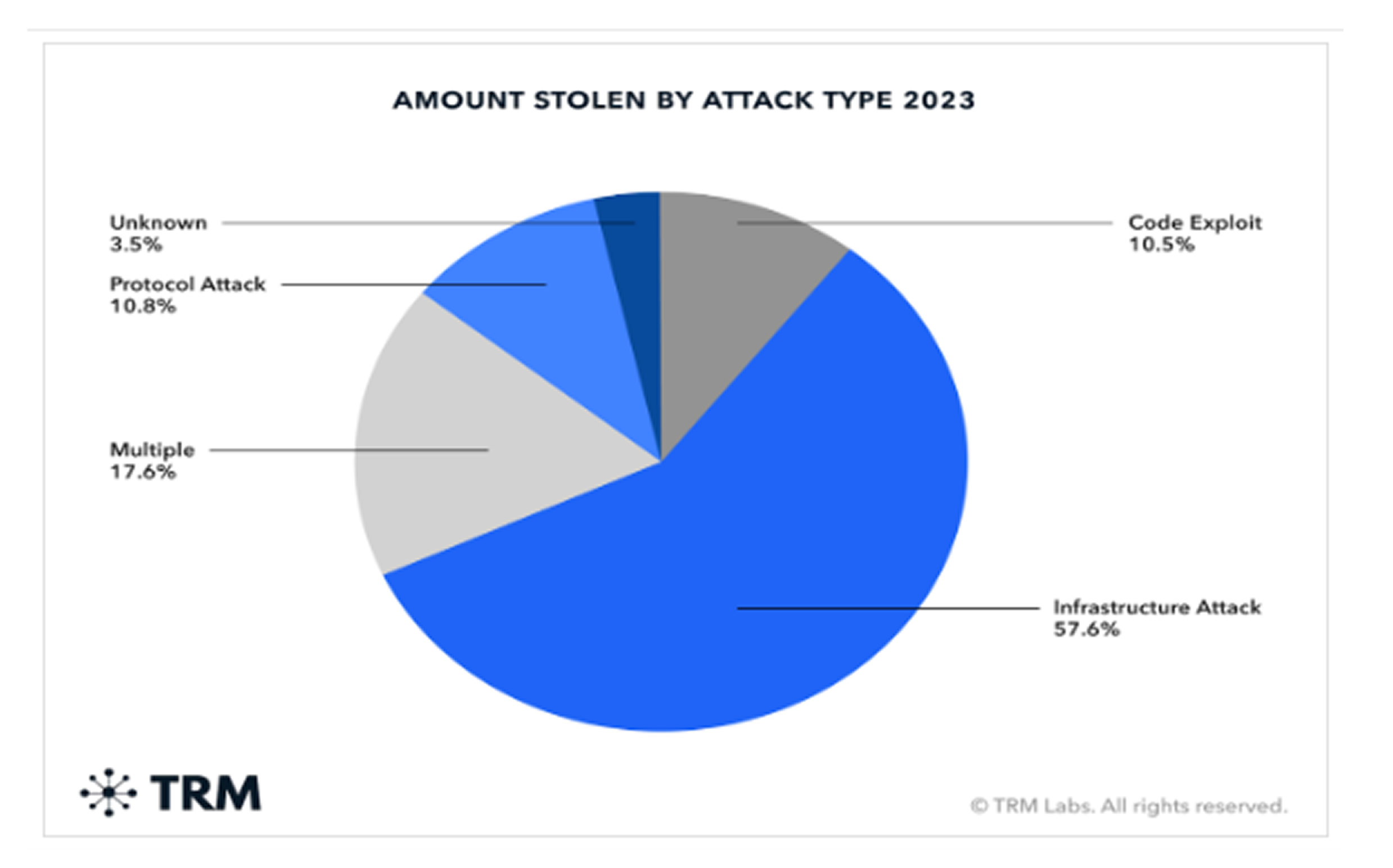
Despite the decline in overall scam revenue, state-sponsored threat actors remain highly active in crypto-related fraud. The North Korean Lazarus Group, a notorious hacking syndicate responsible for stealing over $3 billion in crypto assets over six years, has now shifted focus to phishing scams targeting the crypto industry via Telegram. Cybersecurity firm SlowMist warns that Lazarus-affiliated hackers are impersonating legitimate investment institutions to trick crypto projects into transferring funds to fraudulent wallets. As phishing attacks become more sophisticated, crypto investors and industry players must remain vigilant by implementing strong cybersecurity measures, conducting thorough due diligence, and verifying counterparties before engaging in financial transactions.
Phishing
Phishing scams remain one of the most prevalent cybersecurity threats in the crypto space, with attackers using impersonation, fake websites, and social engineering to deceive victims and gain unauthorized access to their funds. One of the most alarming cases occurred in December, when a former employee of Ledger, a leading hardware wallet manufacturer, unknowingly fell victim to a phishing attack. This breach allowed the attacker to inject malicious code into Ledger's software, which is responsible for managing third-party applications’ access to crypto assets stored on hardware wallets. The impact was widespread, prompting security advisories for users to halt interactions with all decentralized applications (dApps) until further notice. The exploit resulted in the theft of approximately $600,000 in crypto assets, highlighting the critical need for robust security measures in the DeFi and Web3 ecosystem.
In parallel, Chainalysis raised concerns about a growing variant of phishing scams known as approval phishing. Unlike traditional phishing methods, this scam manipulates victims into signing malicious blockchain transactions, unknowingly granting scammers spending authority over specific tokens in their wallets. Some victims have reportedly suffered losses in the tens of millions, underscoring the devastating consequences of these attacks. To mitigate these risks, crypto users must adopt strict verification practices, ensuring they double-check the authenticity of websites and individuals before signing any transaction. Additionally, scrutinizing wallet approval requests and verifying addresses before initiating transactions are essential steps in safeguarding assets against evolving phishing threats.
Pump & dump schemes and rug pulls 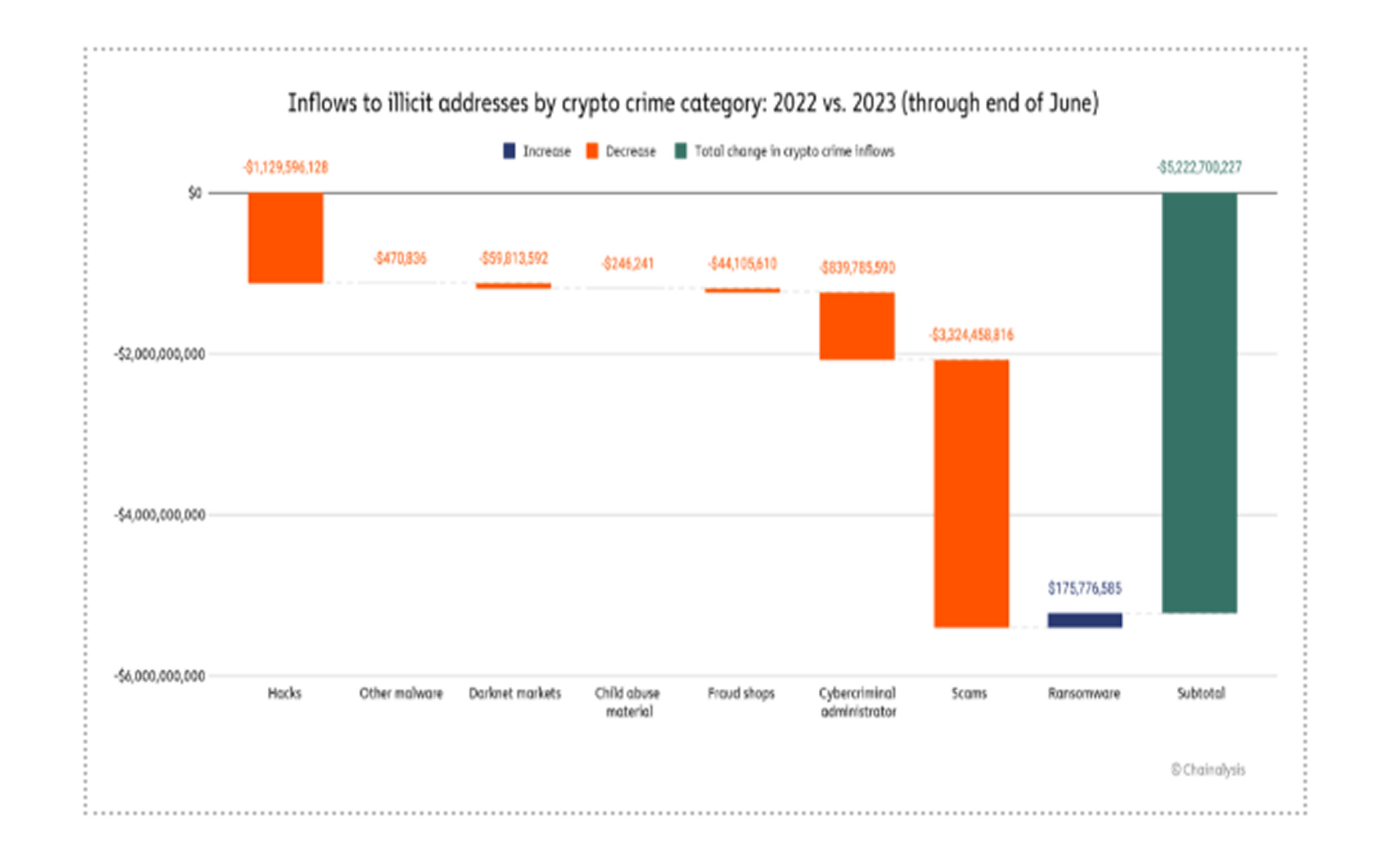
Participants in the cryptocurrency space must remain vigilant against market manipulation tactics such as pump-and-dump schemes and rug pulls, both of which have caused significant financial losses. Pump-and-dump schemes involve artificially inflating a token’s price through misleading statements and hype, enticing investors to buy at a high price before the orchestrators sell off their holdings, leaving victims with devalued assets. While data for this year is still being analyzed, Chainalysis reported that in the previous year, 24% of newly launched tokens experienced a sharp price drop within the first week, signaling possible pump-and-dump activity. This highlights the need for investors to conduct thorough due diligence before investing in newly launched tokens.
Another major threat is rug pulls, where fraudulent crypto projects lure investors with false promises before abruptly vanishing with all funds. Hacken reports that in Q3 of this year, rug pulls accounted for 65% of all crypto-related losses, with 78 incidents costing investors nearly $50 million. One effective way to mitigate rug pull risks is to verify whether a project has undergone an independent third-party audit, which can help detect potential vulnerabilities. However, Hacken’s findings indicate that only 12 out of 78 rug-pulled projects claimed to have been audited, and even then, some received poor security ratings. This underscores the importance of not only checking for audits but also assessing their quality before investing in any crypto project.
Ransomware
While crypto scams declined in the first half of this year, one particular type of crypto-related crime surged—ransomware attacks. According to Chainalysis, ransomware was the only category of crypto crime that saw significant growth this year. By June 2023, cybercriminals had extorted at least $449 million, marking a 64% increase compared to the same period in 2022. This rise comes after a temporary decline in ransomware-related losses in 2022, as large organizations strengthened cybersecurity defenses, improved data backup strategies, and became more resistant to ransom demands. 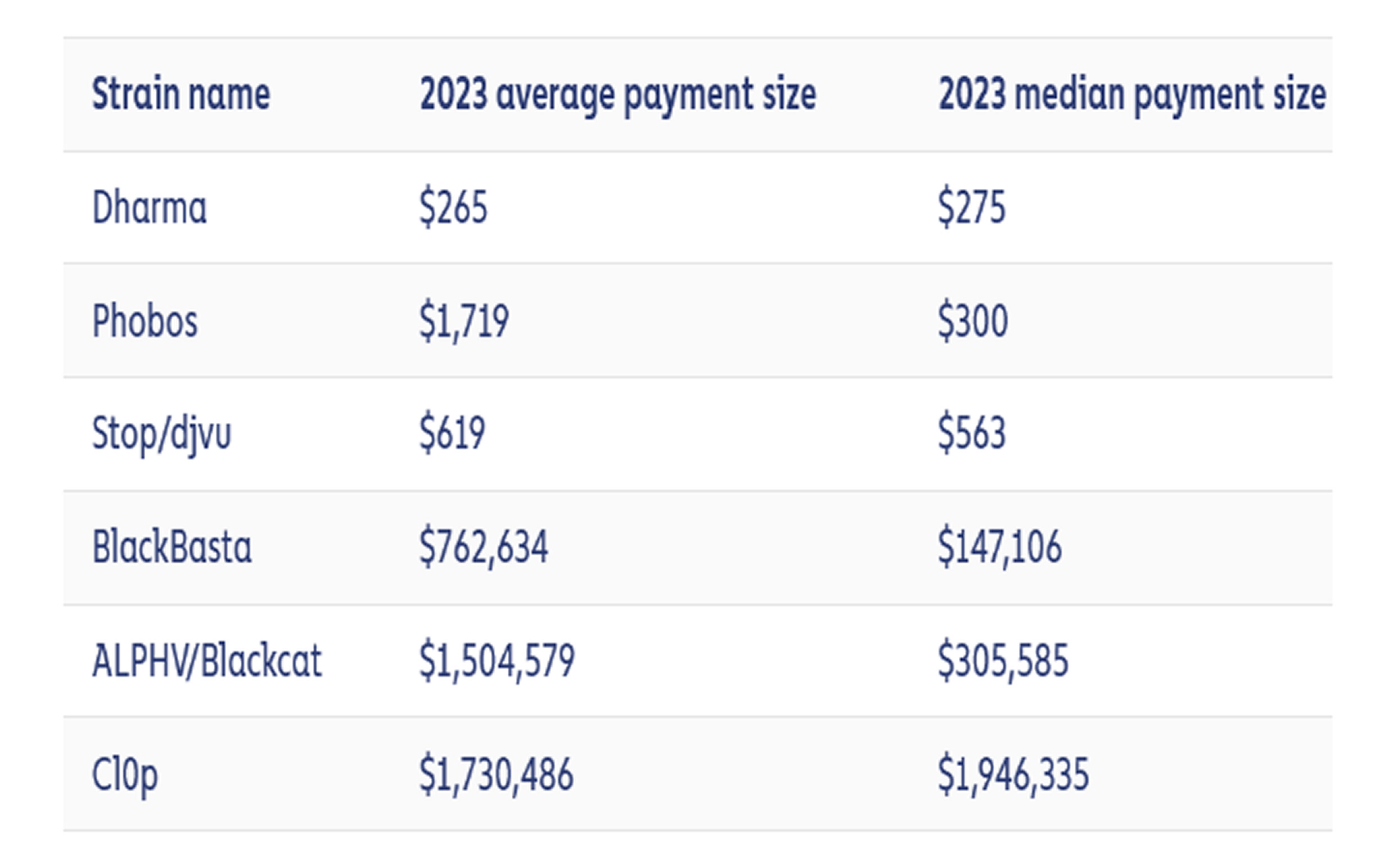
However, the resurgence of ransomware attacks this year is largely due to threat actors shifting their focus to high-value targets, aiming for bigger financial gains. At the same time, there has been an increase in successful small-scale ransomware attacks, further driving up overall losses. This trend underscores the persistent threat of ransomware and highlights the need for robust cybersecurity measures, including regular backups, employee awareness training, and advanced endpoint protection, to mitigate the risks posed by ransomware operators.


