Apple has addressed a vulnerability that was exploited in zero-click attacks used to install Paragon Graphite spyware on the iPhones of two European journalists. The flaw, identified as CVE-2025-43200, was patched in iOS 18.3.1 back in February, but Apple only recently included the issue in its official security advisory.
According to the updated advisory, the vulnerability involved a logic issue in how the system processed maliciously crafted photos or videos shared via iCloud Link. “Apple is aware of a report that this issue may have been exploited in an extremely sophisticated attack targeting specific individuals,” the advisory states.
Although Apple did not disclose detailed information about the attack, the update coincided with the release of a Citizen Lab report that confirmed CVE-2025-43200 had been used in zero-click attacks to deliver Paragon spyware to the devices of two journalists in Europe.
Paragon Spyware Details Uncovered
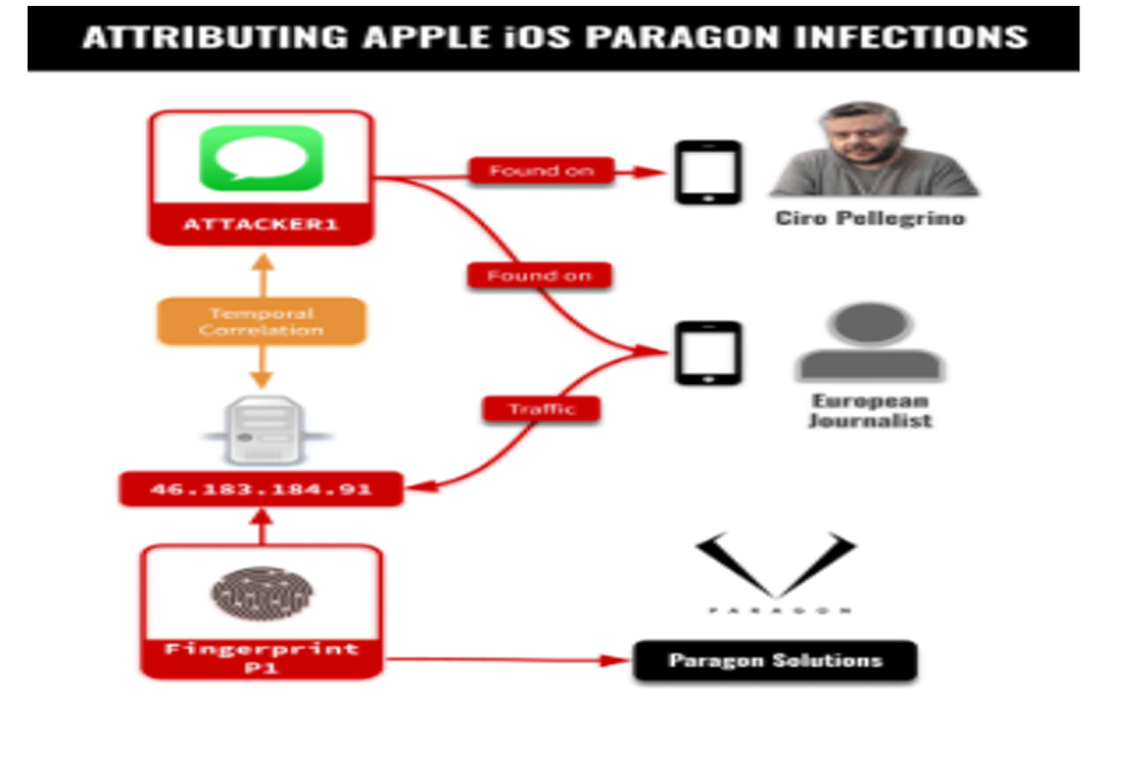
Citizen Lab reported that on April 29, 2025, Apple notified a select group of iOS users that they had been targeted by advanced spyware. While the exact size of the group remains unknown, two journalists, one unnamed and the other Italian journalist Ciro Pellegrino submitted their devices to Citizen Lab for technical analysis. The investigation linked both cases to the same Paragon spyware operator.
The identity of the operator and the reasons for targeting the journalists remain unclear.
Citizen Lab’s analysis revealed that the anonymous journalist’s device was compromised during January and early February 2025 while it was running iOS 18.2.1. Logs showed the device contacted a server associated with a previously identified fingerprint linked to Paragon’s Graphite spyware. This fingerprint, labeled P1, was matched with high confidence.
The analysis also discovered an iMessage account in the logs that corresponded with the period during which the device was in contact with a Paragon server at IP address 46.183.184[.]91. Based on forensic evidence, Citizen Lab concluded that the spyware was delivered using a sophisticated iMessage zero-click method that would have been invisible to the user.
Pellegrino’s iPhone contained log entries with the same iMessage account, suggesting an attempt to infect his device using a similar Graphite zero-click attack.
Citizen Lab explained that customers of mercenary spyware vendors usually have their own unique infrastructure. The shared iMessage account strongly indicated that a single Paragon client was responsible for targeting both individuals.
Additional Cases Involving Paragon Spyware
Pellegrino is the second journalist from Fanpage.it confirmed to have been targeted with Paragon spyware. This raises concerns that the media outlet itself may have been under surveillance.
In an earlier case, Fanpage editor Francesco Cancellato received a notification from WhatsApp in January 2025 alerting him that he had been targeted with the same spyware.
Citizen Lab stated that three European journalists have so far been confirmed as victims of Paragon’s Graphite spyware. Despite this, there has been no public explanation regarding who ordered the surveillance.
The repeated targeting of journalists, particularly from the same news outlet, raises serious questions about which Paragon customer was behind the attacks and under what legal framework, if any, the surveillance was authorized.
“The ongoing lack of accountability for spyware victims shows how journalists in Europe continue to face serious digital threats,” Citizen Lab concluded. “This situation underscores the risks associated with the spread and misuse of invasive surveillance tools.”
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.