Fake Zoom Installer Spreading Malware and Ransomware Attacks
A fraudulent Zoom installer is circulating online, deceiving users into downloading malware that silently takes control of their systems. To protect your data from cybercriminals, be cautious when installing Zoom from unverified sources.
Cybersecurity researchers have identified a malicious Zoom installer that mimics the official software, tricking unsuspecting users into downloading harmful software. DFIR security experts warn that Windows users are at risk of being infected with BlackSuit ransomware, which has been targeting critical sectors, including healthcare and education.
How the Malware Operates
Once installed, the malware remains dormant for several days before launching a full-scale attack stealing sensitive data, encrypting files, and demanding ransom payments.
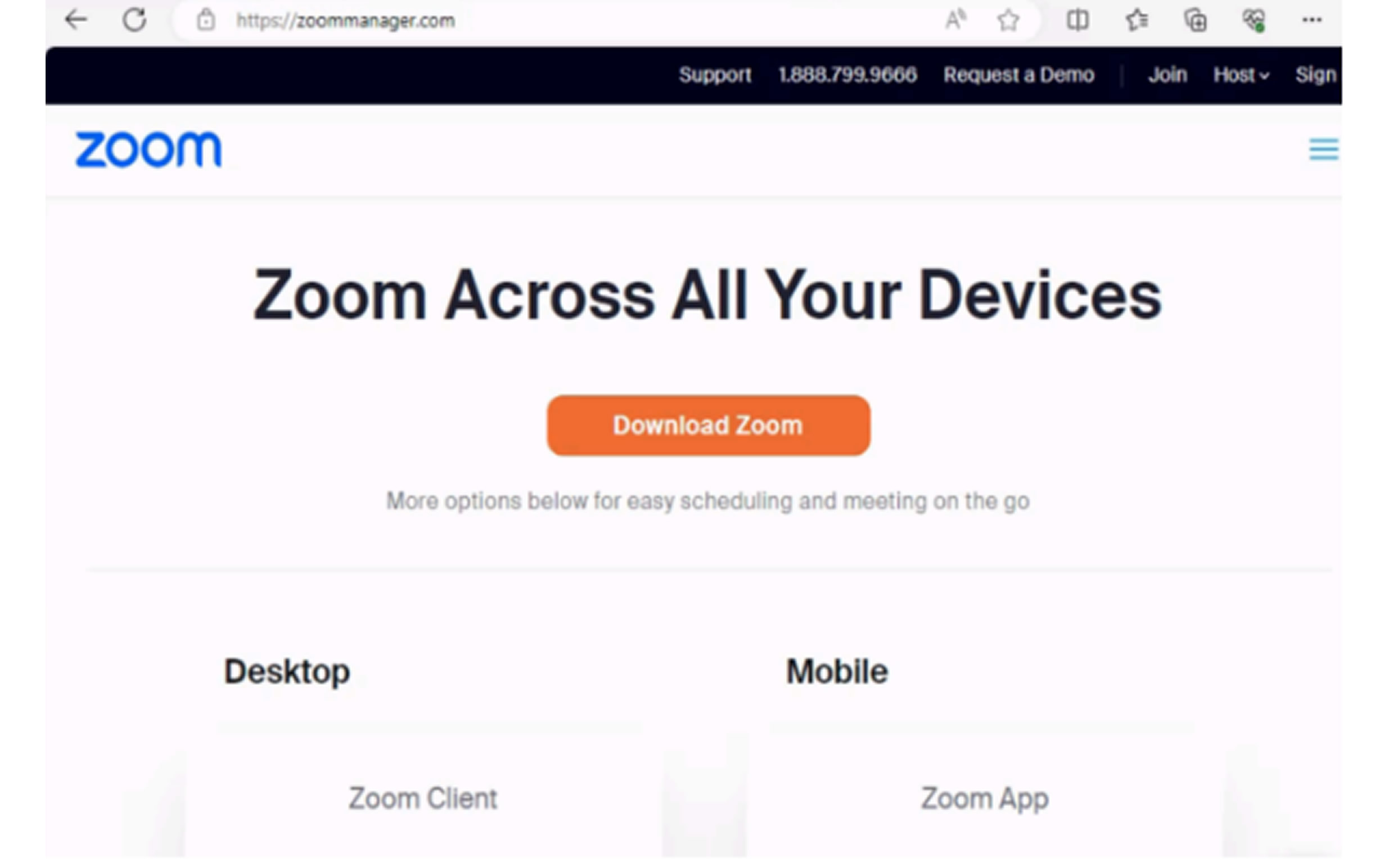
A key indicator of the scam is the fake website zoommanager[.]com, which is not affiliated with Zoom Video Communications. Clicking on the link triggers the download of a malicious loader that evades security detection by disabling Windows Defender.
The malware then connects to a Steam Community page to retrieve further instructions and downloads two archive files one containing the genuine Zoom installer and the other packed with malicious software.
Upon execution, the malware injects itself into a legitimate Windows process (MSBuild.exe) and stays inactive for eight days before initiating the next phase of the attack.
On the ninth day, it activates additional malware, collects system data, and deploys Cobalt Strike, a powerful hacking tool that enables lateral movement across networks. Attackers also install QDoor, a backdoor tool that grants remote control over infected systems. The malware then extracts sensitive data and deploys BlackSuit ransomware, encrypting files and leaving a ransom note demanding payment.
The BlackSuit Ransomware Threat
BlackSuit ransomware first appeared in early 2023 and has since targeted major industries, particularly healthcare and education.
- Kershaw County School District (KCSD), South Carolina (2024): The gang claimed to have stolen 17GB of data from the district, which serves over 11,000 students across 19 schools.
- CDK Global Attack (June 2024): This ransomware attacks crippled car dealerships across the U.S., forcing businesses to revert to manual record-keeping. Rumors suggest CDK Global paid a ransom to restore operations.
- Kansas City Police Department (KCKPD) Breach (June 2024): After KCKPD refused to pay the ransom, hackers leaked sensitive data, including payroll records, crime scene photos, and fingerprint databases.
- Kansas City Hospice Breach (October 2024): BlackSuit claimed responsibility for breaching this nonprofit healthcare provider, exposing patient information.
- Connexure (Formerly Young Consulting) Attack (May 2024): Nearly one million individuals were notified that their personal data had been compromised.
Protect Yourself
To avoid falling victim to such cyber threats:
- Download software only from official sources.
- Verify website URLs before clicking on links.
- Keep your security software updated.
- Be cautious of unexpected downloads.
Cybercriminals are constantly refining their tactics, making it essential to stay informed and vigilant against potential threats.
Found this article interesting? Follow us on X(Twitter) and FaceBook to read more exclusive content we post.


