Technical details released for Cisco IOS XE WLC critical file upload vulnerability (CVE-2025-20188)
Technical information about a maximum-severity arbitrary file upload vulnerability in Cisco IOS XE WLC, identified as CVE-2025-20188, has now been made publicly available. This disclosure brings the security community closer to a functional exploit.
Researchers from Horizon3 published a detailed write-up that does not include a full proof-of-concept remote code execution exploit. However, it contains enough guidance for experienced attackers or automated tools to reconstruct a working exploit.
Due to the high potential for weaponization and widespread attacks, it is strongly advised that affected users take immediate steps to secure their systems.
Overview of the Cisco IOS XE WLC vulnerability
Cisco publicly disclosed this critical vulnerability on May 7, 2025. The issue affects IOS XE Software used in Wireless LAN Controllers and enables remote, unauthenticated attackers to gain complete control of vulnerable devices.
The vulnerability exists due to a hardcoded JSON Web Token (JWT) that allows remote attackers to upload files, carry out path traversal, and execute arbitrary commands with root-level access.
Cisco clarified that the flaw only poses a threat when the 'Out-of-Band AP Image Download' feature is active. The following device models are at risk when that feature is enabled:
- Catalyst 9800-CL Wireless Controllers for Cloud
- Catalyst 9800 Embedded Wireless Controllers for Catalyst 9300, 9400, and 9500 Series Switches
- Catalyst 9800 Series Wireless Controllers
- Embedded Wireless Controller on Catalyst Access Points
Details from Horizon3’s research
Horizon3’s analysis revealed that the vulnerability stems from a hardcoded fallback JWT secret value ("notfound") used by backend Lua scripts in the file upload mechanism. When the '/tmp/nginx_jwt_key' file is absent, the backend falls back to this default string to verify tokens. This allows attackers to generate valid JWTs using 'HS256' and 'notfound' without needing access to real secrets.
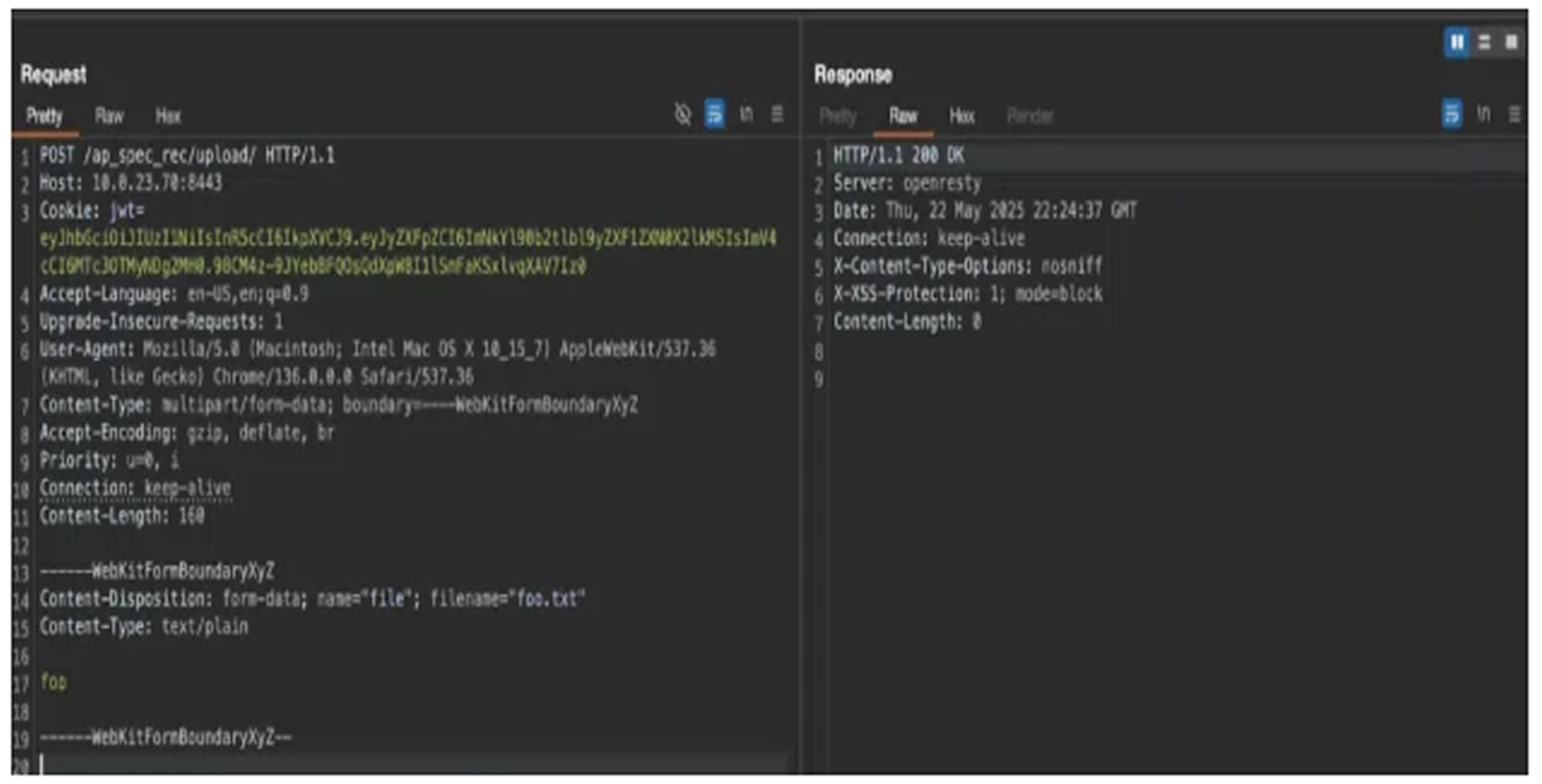
In their demonstration, Horizon3 used an HTTP POST request to the '/ap_spec_rec/upload/' endpoint over port 8443. They were able to perform path traversal and place a benign file (foo.txt) outside the intended directory. To achieve remote code execution, an attacker could overwrite backend configuration files, upload malicious web shells, or manipulate monitored files to carry out unauthorized operations.
In one example, the researchers targeted the 'pvp.sh' service, which monitors specific directories. By altering its configuration and forcing a reload, they could execute arbitrary commands.
Recommended response and mitigation
Given the severity and likelihood of exploitation, users should upgrade to a fixed version, specifically IOS XE version 17.12.04 or later, without delay.
As a temporary protective measure, administrators can disable the Out-of-Band AP Image Download feature to prevent access to the vulnerable service.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



