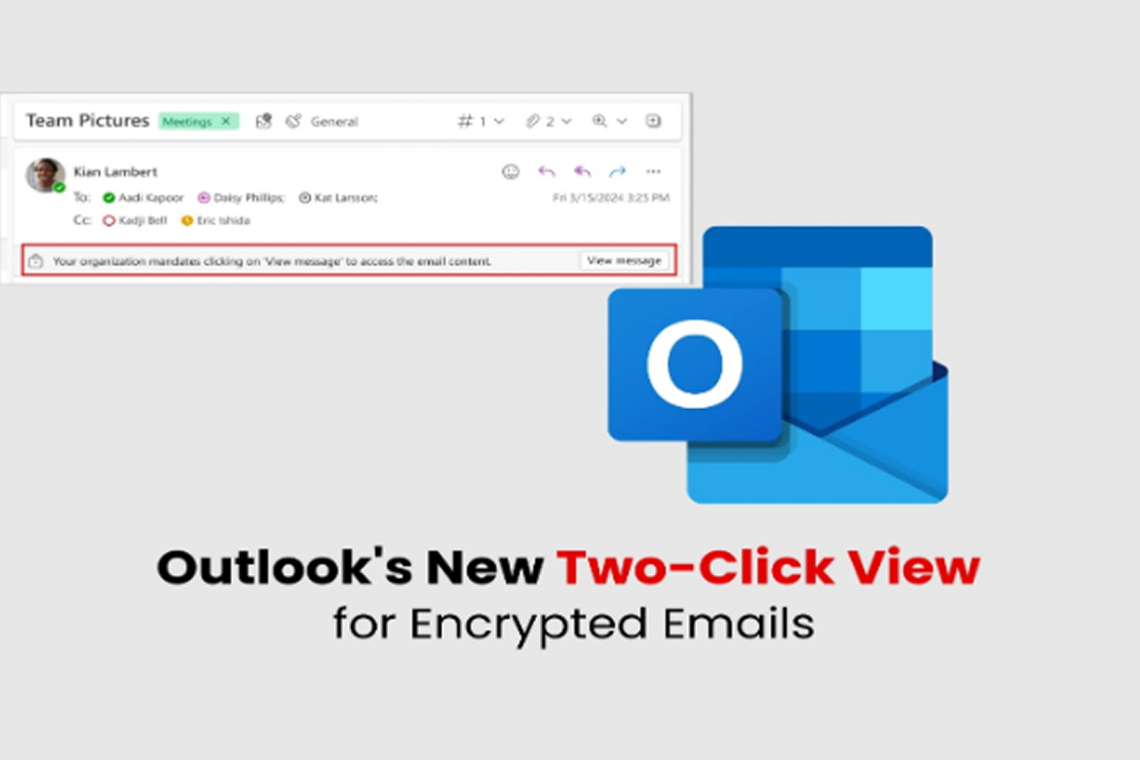
Microsoft to Introduce Two-Click Verification for Encrypted Outlook Emails Starting April 2025
Microsoft has announced a new security feature for Outlook that adds an extra layer of protection when accessing encrypted emails. Beginning in April 2025, the company will roll out a two-click verification process designed to prevent accidental exposure of sensitive information especially in public settings or during screen-sharing.
This enhancement, linked to Microsoft 365 Roadmap ID 483883, will require users to actively confirm their intent to view encrypted content. When receiving an encrypted email, users will first encounter a prompt stating, "Your organization mandates clicking ‘View Message’ to access the email content." Only after selecting this button will the message be displayed.
Rollout Timeline:
- General Outlook users: Phased rollout starts early April 2025, complete by the end of April.
- Government Community Cloud (GCC) users: Begins early May 2025, full deployment by end of May.
- Mobile users (iOS & Android): Update starts mid-June 2025, concluding by late June.
The feature will be available across all major Outlook platforms such as Windows desktop, web, iOS, and Android, and is aimed at boosting user awareness and minimizing unintentional data exposure.
By default, the two-click verification will be disabled, allowing organizations to opt in based on their security needs. IT admins can activate the feature using the Microsoft Azure portal or PowerShell.
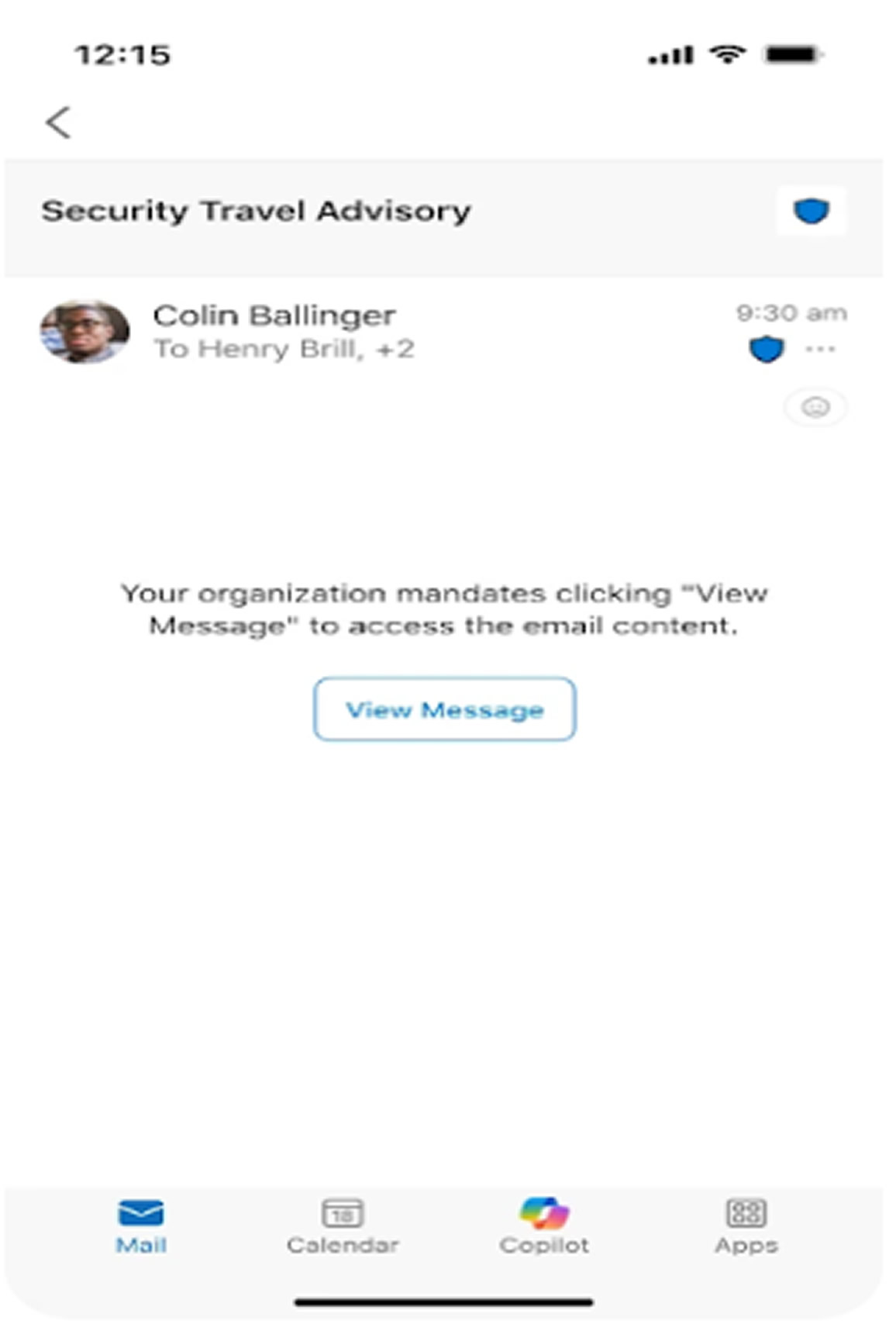
Microsoft emphasizes that while the added step increases protection, it preserves a seamless user experience. The prominent interface button maintains usability while prompting intentional interaction with sensitive messages.
This security update reflects Microsoft’s broader effort to help organizations safeguard confidential data, including intellectual property and regulated personal information, with minimal disruption to daily workflows.
Organizations planning to adopt the feature should begin preparing their IT teams ahead of the phased rollout.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.