Cybersecurity researchers have discovered a new security flaw in the NVIDIA Container Toolkit,
allowing attackers to bypass container isolation and gain full access to the host system.
The vulnerability, CVE-2025-23359 (CVSS score: 8.3), affects the following versions:
-
NVIDIA Container Toolkit (All versions up to 1.17.3) – Fixed in 1.17.4
-
NVIDIA GPU Operator (All versions up to 24.9.1) – Fixed in 24.9.2
This flaw is a bypass for a previously patched vulnerability, meaning attackers could still exploit systems that haven't updated to the latest versions. Organizations using NVIDIA GPU containers are urged to apply patches immediately to prevent potential security risks.
NVIDIA Container Toolkit for Linux contains a Time-of-Check Time-of-Use (TOCTOU) vulnerability when used with default configuration, where a crafted container image could gain access to the host file system," the company said in an advisory on Tuesday.
"A successful exploit of this vulnerability might lead to code execution, denial of service, escalation of privileges, information disclosure, and data tampering."
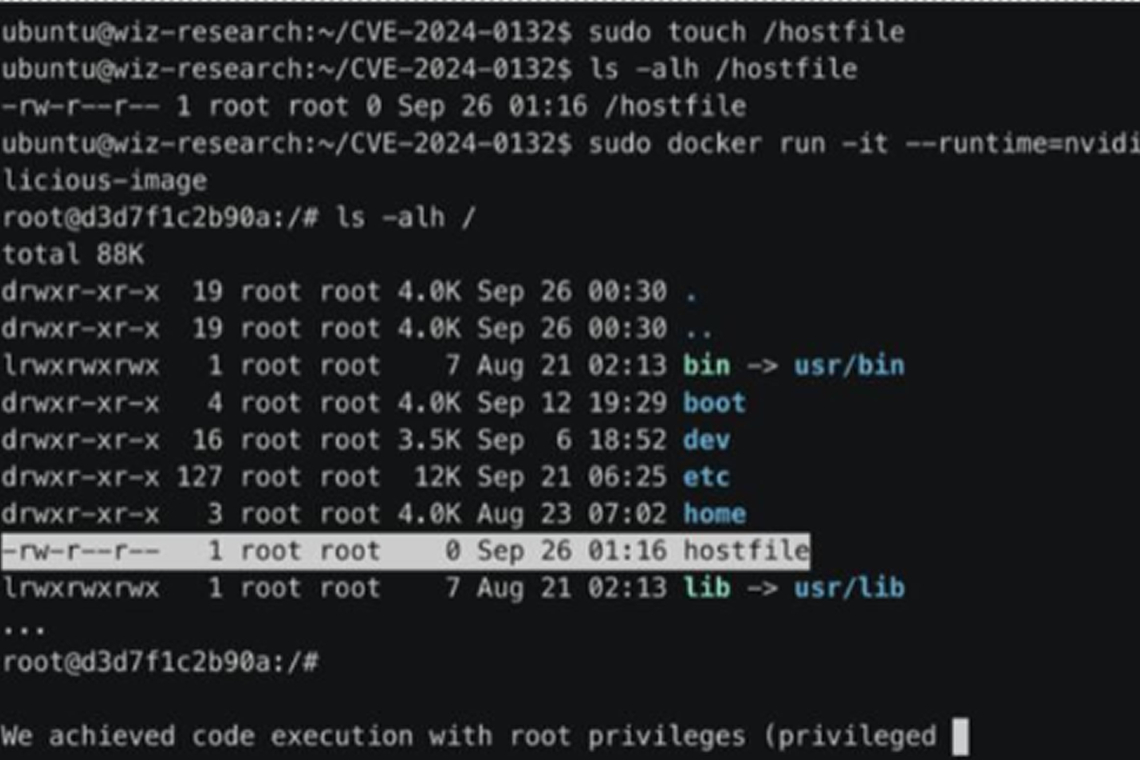
Cloud security firm Wiz, which shared additional technical specifics of the flaw, said it's a bypass for another vulnerability (CVE-2024-0132, CVSS score: 9.0) that was addressed by NVIDIA in September 2024.
In a nutshell, the vulnerability enables bad actors to mount the host's root file system into a container, granting them unfettered access to all files. Furthermore, the access can be leveraged to launch privileged containers and achieve full host compromise via the runtime Unix socket.
Wiz researchers security researchers Shir Tamari, Ronen Shustin, and Andres Riancho said their source code analysis of the container toolkit found that the file paths used during mount operations could be manipulated using a symbolic link such that it makes it possible to mount from outside the container (i.e., the root directory) into a path within "/usr/lib64."
Attackers exploiting the NVIDIA Container Toolkit vulnerability initially gain read-only access to the host file system. However, this restriction can be bypassed by leveraging Unix sockets to launch new privileged containers, ultimately granting full control over the file system.
With this escalated access, threat actors can:
✅ Monitor network traffic
✅ Debug and manipulate active processes
✅ Execute various host-level operations
To mitigate this risk, security researchers advise updating to the latest patched version. Additionally, organizations should ensure that the "--no-cntlibs" flag remains enabled in production environments to prevent exploitation.