New Threat Actor UAT-5918 Targets Taiwan’s Critical Infrastructure
Threat hunters have identified a new advanced persistent threat (APT) group, dubbed UAT-5918, actively targeting critical infrastructure entities in Taiwan since at least 2023.
According to Cisco Talos researchers Jungsoo An, Asheer Malhotra, Brandon White, and Vitor Ventura, UAT-5918 is primarily focused on establishing long-term access to infiltrate networks and steal sensitive information. The group employs a mix of web shells and open-source hacking tools to maintain persistence, harvest credentials, and conduct post-compromise activities. Aside from critical infrastructure, UAT-5918 has also targeted IT, telecommunications, academia, and healthcare sectors.
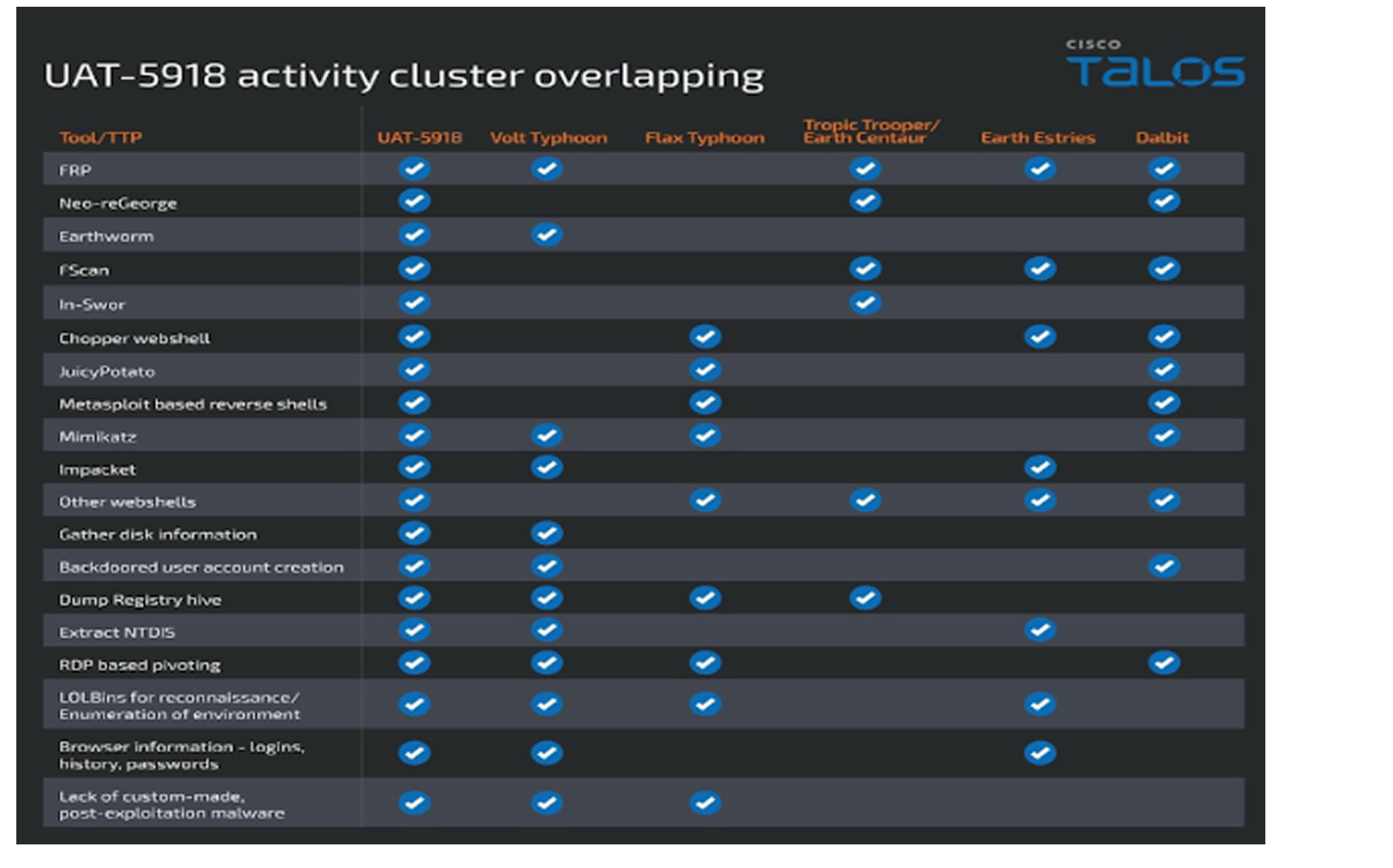
Security analysts note tactical overlaps between UAT-5918 and other Chinese-affiliated hacking groups, including Volt Typhoon, Flax Typhoon, Tropic Trooper, Earth Estries, and Dalbit. Their attack strategy begins with exploiting unpatched web and application server vulnerabilities (N-day flaws) to gain initial access. Once inside, they deploy various open-source tools to conduct network reconnaissance, gather system data, and move laterally across the environment.
A key aspect of UAT-5918’s post-exploitation tactics is its use of Fast Reverse Proxy (FRP) and Neo-reGeorge, which establish reverse proxy tunnels for remotely accessing compromised systems. The group also relies on well-known credential theft tools like Mimikatz, LaZagne, and BrowserDataLite. BrowserDataLite, in particular, is used to extract login credentials, cookies, and browsing history from web browsers. Additionally, the attackers utilize Chopper web shell, Crowdoor, and SparrowDoor, the latter two of which have been linked to the Earth Estries hacking group.
Beyond credential theft, UAT-5918 conducts systematic data exfiltration by scanning both local and shared drives for sensitive files. Security researchers emphasize that the group’s operations appear to be manually executed, indicating a deliberate and targeted approach. Furthermore, they deploy web shells across sub-domains and exposed servers, ensuring multiple entry points into the victim's network.
UAT-5918’s stealthy and persistent tactics make it a serious threat to Taiwanese infrastructure and beyond, reinforcing the need for regular patching, threat monitoring, and proactive security measures to mitigate potential breaches.
Found this article interesting? Follow us on X(Twitter) and Instagram to read more exclusive content we post.