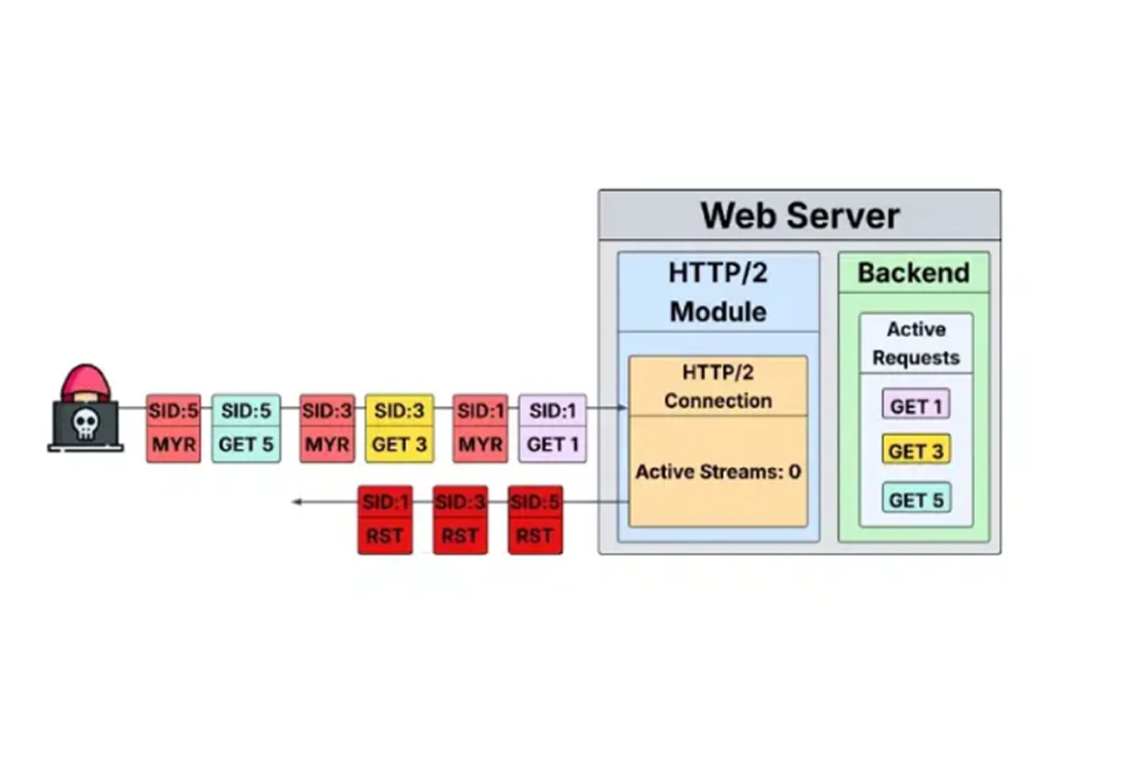
Researchers from Tel Aviv University have uncovered a new denial-of-service vulnerability in HTTP/2, identified as CVE-2025-8671. The flaw, dubbed "MadeYouReset," bypasses previous defenses set up after the 2023 "Rapid Reset" vulnerability and allows attackers to overload servers by manipulating malformed frames.
The vulnerability was publicly disclosed on August 13, though researchers had already been working with vendors since May to address it. According to Cloudflare, the issue affects only a limited number of unpatched HTTP/2 server implementations that fail to restrict malformed frame submissions.
Unlike Rapid Reset, which relied on clients canceling streams, MadeYouReset tricks servers into canceling valid requests. This creates excessive concurrent processing, leading to service disruption. The exploit uses six techniques involving control frames like WINDOW_UPDATE, PRIORITY, HEADERS, and DATA.
Cloudflare and Akamai confirmed their systems are not affected. Other vendors, including Apache Tomcat, F5, Fastly, h2o, Netty, and IBM WebSphere, have released patches or mitigations. Carnegie Mellon’s CERT Coordination Center listed several impacted projects with varying severity levels.
The disclosure coincides with new research from PortSwigger revealing serious vulnerabilities in HTTP/1.1, highlighting ongoing concerns in web protocol security.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.