Newly Discovered Security Flaws in Solar Inverter Products Pose Risks to Electrical Grids
Cybersecurity researchers have uncovered 46 security vulnerabilities in solar inverters from three major vendors—Sungrow, Growatt, and SMA—which could allow attackers to seize control of devices, execute remote code, or disrupt power grids. These flaws, collectively codenamed SUN:DOWN by Forescout Vedere Labs, highlight the growing cyber risks in the renewable energy sector.
Key Security Flaws Identified
The newly discovered vulnerabilities enable attackers to:
- Execute remote code on SMA's sunnyportal[.]com by uploading malicious .aspx files.
- Enumerate usernames on Growatt’s server.growatt.com/userCenter.do endpoint.
- Access and take control of other users' devices via Growatt’s API endpoints.
- Steal smart meter serial numbers using a valid username, leading to account takeovers.
- Obtain and manipulate EV charger data, firmware information, and energy consumption details through Growatt’s evcharge.growatt.com/ocpp endpoint.
- Exploit weak encryption in Sungrow’s Android app, allowing attackers to decrypt communications between the app and iSolarCloud.
- Bypass security checks in Sungrow’s Android app, making it vulnerable to Adversary-in-the-Middle (AitM) attacks.
- Decrypt all firmware updates in Sungrow’s WiNet WebUI due to a hardcoded password.
- Exploit MQTT message vulnerabilities in Sungrow’s devices, leading to remote code execution or denial-of-service (DoS) attacks.
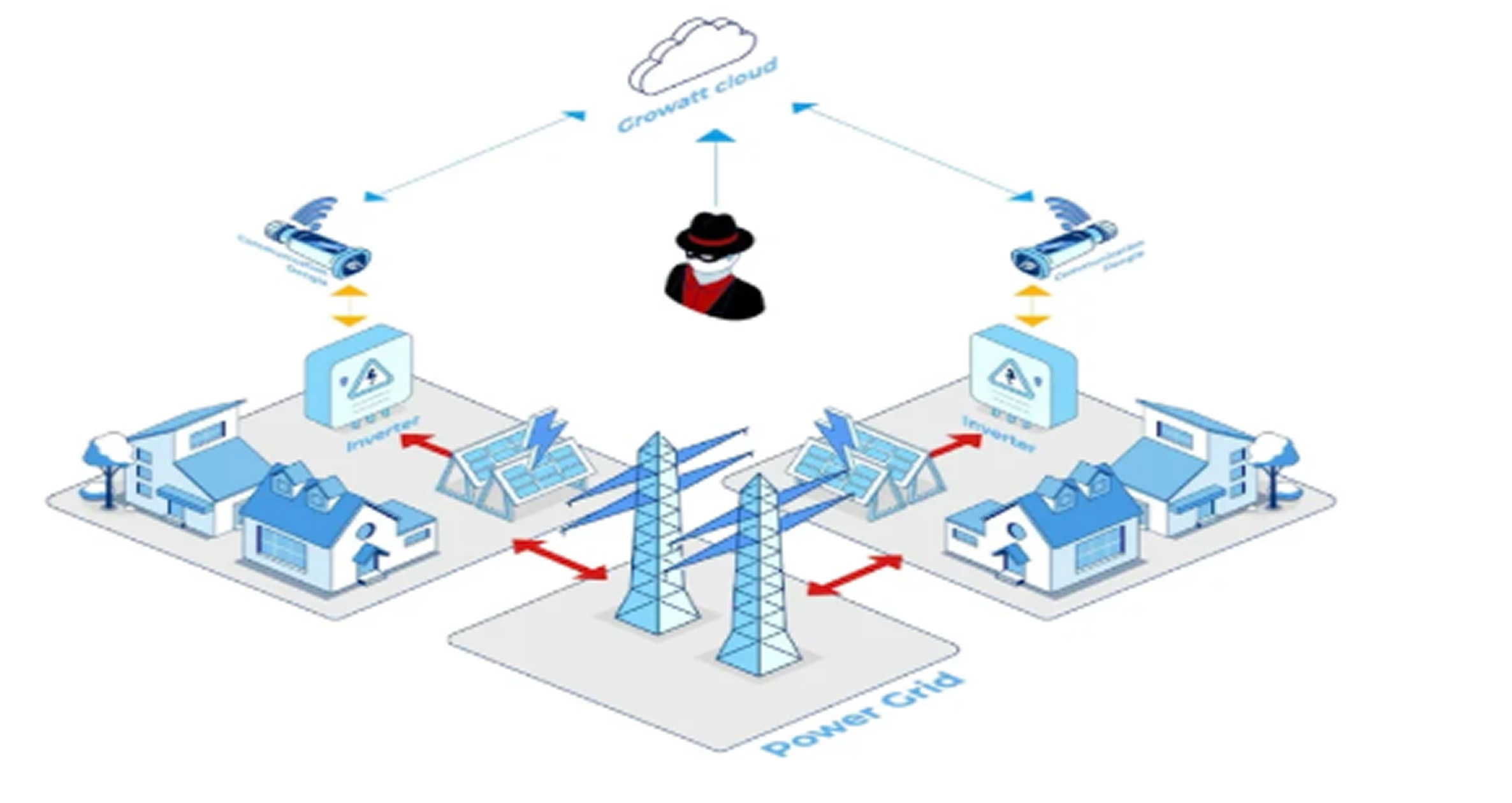
Potential Impact on Electrical Grids
Forescout warns that attackers gaining control of a large fleet of inverters could destabilize power grids by manipulating energy supply levels.
In a hypothetical attack on Growatt inverters, an attacker could:
- Guess usernames via an exposed API.
- Reset passwords to "123456" to hijack accounts.
- Control hijacked inverters as a botnet, amplifying the attack and disrupting the grid.
These vulnerabilities also increase the risk of cyber-physical ransomware attacks, where attackers alter energy flow to the grid, causing fluctuations and blackouts.
Mitigation Strategies
Daniel dos Santos, Head of Research at Forescout Vedere Labs, recommends the following steps to reduce risk:
- Enforce strict security requirements when purchasing solar equipment.
- Conduct regular risk assessments to identify vulnerabilities.
- Ensure full network visibility into solar inverters and related infrastructure.
The disclosure of these solar inverter flaws comes alongside reports of serious security issues in other industrial devices, including:
- Inaba Denki Sangyo’s production line monitoring cameras, which allow remote surveillance and interfere with recording production stoppages.
- GE Vernova N60 Network Relay, Zettler 130.8005 industrial gateway, and Wago 750-8216/025-001 PLCs, which attackers could exploit to gain full device control.
While Inaba Denki Sangyo has not yet patched the vulnerabilities, it has urged customers to restrict internet access and ensure these devices are placed in secure areas accessible only to authorized personnel.
With cyberattacks on critical infrastructure becoming increasingly sophisticated, organizations must prioritize cybersecurity measures to protect against potential disruptions and attacks on essential systems.


