A Chinese state-sponsored hacking group has compromised a military company in the Philippines using a new, previously unknown fileless malware framework called EggStreme.
According to a report by cybersecurity firm Bitdefender, this multi-stage tool operates with a low profile by injecting malicious code directly into memory. The core component, called EggStremeAgent, is a full-featured backdoor that allows the hackers to conduct extensive system reconnaissance, move laterally across a network, and steal data using an injected keylogger.
The targeting of the Philippines follows a pattern for Chinese hacking groups, particularly due to geopolitical tensions in the South China Sea. Bitdefender, which first detected the activity in early 2024, describes EggStreme as a well-integrated set of malicious tools designed to maintain a persistent presence on infected machines.
The attack begins with a payload called EggStremeFuel, which profiles the system and then deploys EggStremeLoader to establish persistence. This ultimately leads to the activation of EggStremeAgent. EggStremeFuel itself can perform functions such as getting drive information, starting a command prompt session, reading and transmitting files, and dumping its own configuration to disk.
EggStremeAgent, described as the framework's "central nervous system," monitors new user sessions and injects a keylogger called EggStremeKeylogger to steal keystrokes and other sensitive data. It communicates with a command-and-control server using the Google Remote Procedure Call (gRPC) protocol and supports 58 commands that enable network discovery, privilege escalation, data exfiltration, and the injection of other malicious implants.
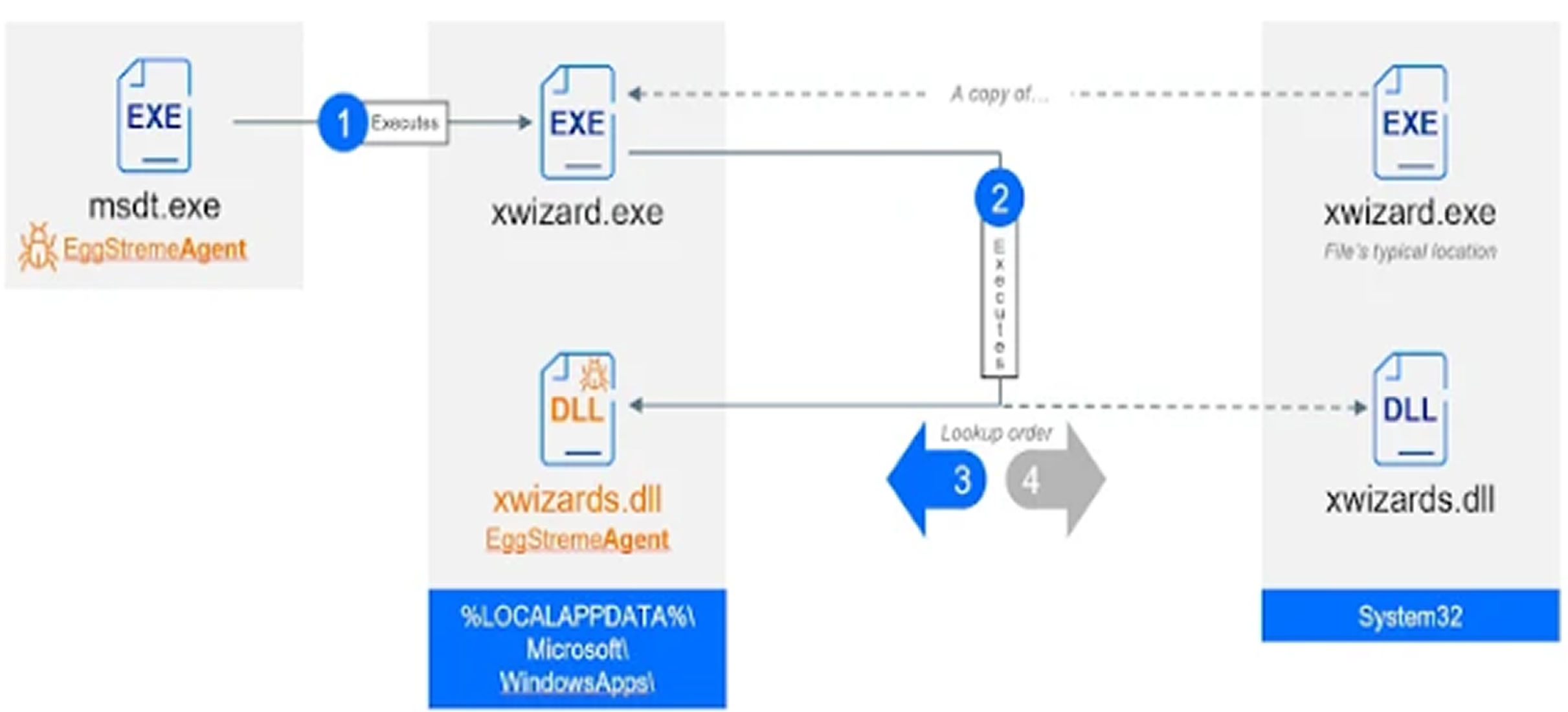
The hackers also use DLL sideloading, a technique where they trick a legitimate program into loading a malicious library. This method is used consistently throughout the attack chain and helps them to evade detection. The attackers also use a proxy utility called Stowaway to establish a foothold inside a network.
The fileless nature of the framework further complicates detection because the malicious code is executed in memory and leaves no traces on the disk. This, combined with the use of DLL sideloading and a sophisticated, multi-stage process, allows the framework to operate with a low profile. Bitdefender describes the EggStreme malware as a highly advanced and sophisticated threat.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



