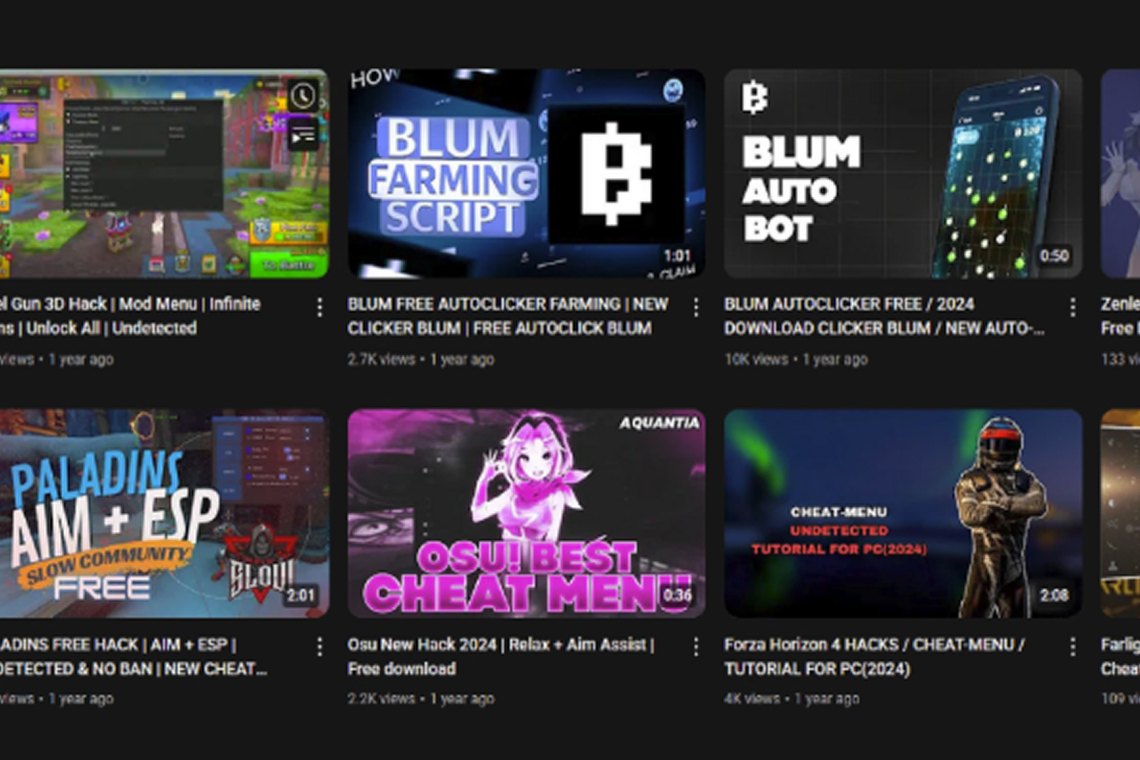
A massive malicious network of YouTube accounts is actively abusing the video platform's popularity and built in trust to spread malware. The network has been active since 2021 and has published over 3,000 malicious videos to date, with the volume of such videos tripling since the start of this year.
The YouTube Ghost Network
Check Point has codenamed the operation the YouTube Ghost Network. This campaign relies on hacking legitimate, existing YouTube accounts and replacing their content with new, malicious videos. These videos center around topics like pirated software and Roblox game cheats, aiming to infect users who are searching for them with various types of stealer malware. Some of these videos have gained significant traction, racking up hundreds of thousands of views. Google has since stepped in to remove the majority of these clips.
According to Check Point's Eli Smadja, the operation successfully took advantage of trust signals, including the videos' views, likes, and comments, to make the malicious content seem safe. This scale, modularity, and sophistication make it a blueprint for how threat actors now weaponize engagement tools to distribute malware.
Role-Based Structure and Evasion
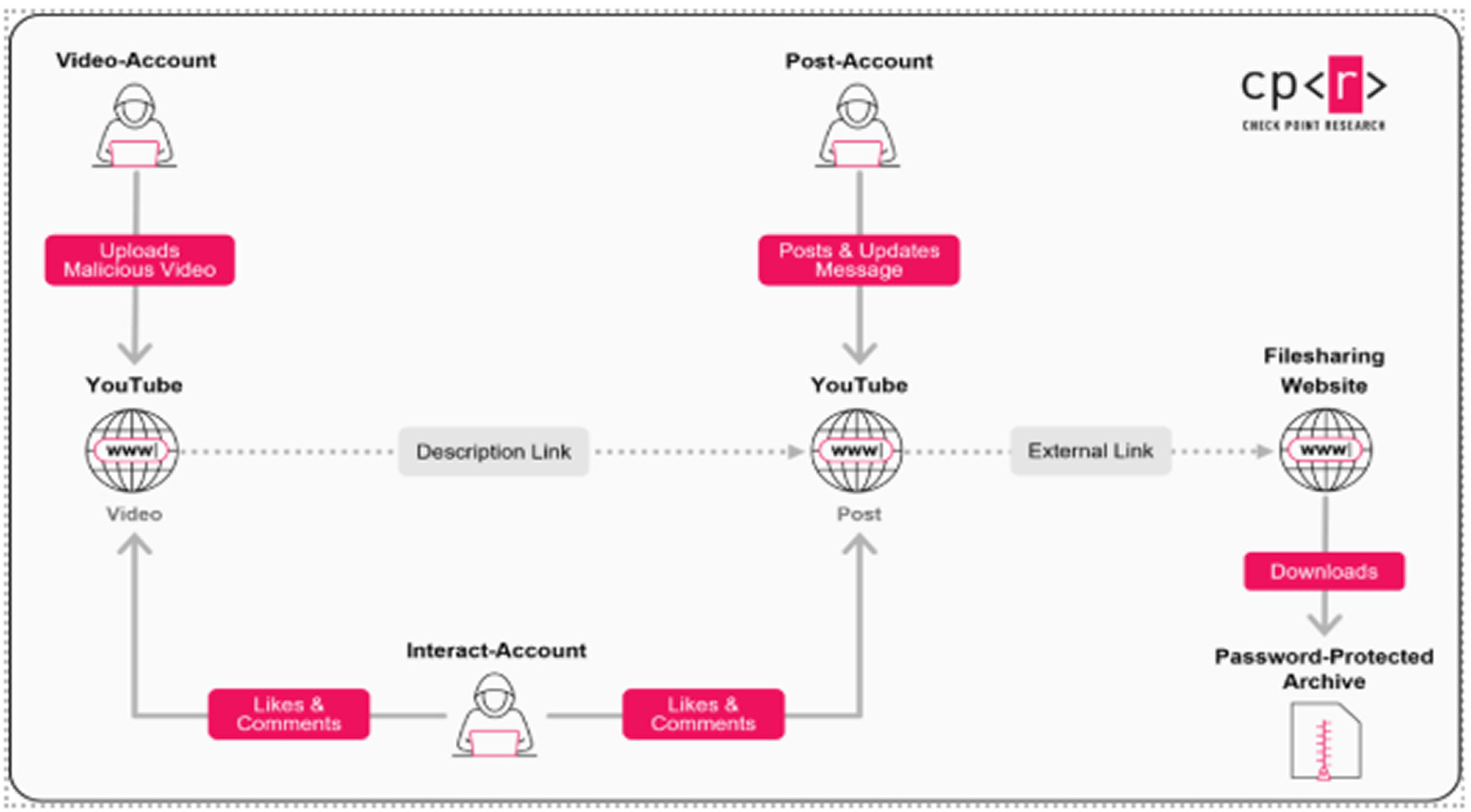
The network’s success stems from its role based structure, which ensures operational continuity even when individual accounts are banned. The network primarily consists of compromised YouTube accounts, each assigned a specific function:
Video accounts: These upload the phishing videos and include malicious download links in the video descriptions, pinned comments, or even as part of the on screen installation process.
Post accounts: These publish community messages and posts that contain links to external malicious sites.
Interact accounts: These accounts are used to like and post encouraging comments, giving the videos a false sense of trust and credibility.
Delivery and Payloads
The download links direct users to a wide range of legitimate services like MediaFire, Dropbox, or Google Drive, or to phishing pages hosted on Google Sites and Blogger. To mask the true destination, the links are often concealed using URL shorteners.
The YouTube Ghost Network has been used to distribute several highly dangerous malware families, including Lumma Stealer, Rhadamanthys Stealer, RedLine Stealer, and Phemedrone Stealer.
Check Point emphasizes that the continued evolution of malware distribution methods demonstrates the adaptability of threat actors in bypassing traditional security defenses. Adversaries are increasingly shifting toward sophisticated, platform-based strategies like Ghost Networks, which leverage the trust inherent in legitimate accounts and the engagement mechanisms of popular platforms to orchestrate large scale, persistent, and highly effective malware campaigns.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.