Massive Black Basta Ransomware Leak Uncovers Internal Conflicts and Tactics
A recent leak of over a year’s worth of internal chat logs from the notorious ransomware gang Black Basta has shed light on their operations, internal disputes, and evolving attack methods. The exposed messages provide a rare glimpse into the inner workings of one of the world’s most dangerous cybercriminal groups.
The Russian-language chat logs, spanning from September 18, 2023, to September 28, 2024, surfaced online on February 11, 2025, courtesy of an anonymous figure known as ExploitWhispers. The individual claimed they released the data because Black Basta had started targeting Russian banks. However, the true identity of the leaker remains unknown.
Black Basta’s Rise and Global Impact
Black Basta first gained attention in April 2022, using the now largely obsolete QakBot (QBot) malware to spread its ransomware. According to a May 2024 advisory from the U.S. government, Black Basta had, by that time, already attacked over 500 organizations spanning private industries and critical infrastructure in North America, Europe, and Australia.
Reports from Elliptic and Corvus Insurance indicate that the ransomware group had amassed at least $107 million in Bitcoin ransom payments from over 90 victims by the end of 2023. These figures highlight the widespread damage inflicted by the cybercrime syndicate.
Infighting and Departures Weaken Black Basta
Swiss cybersecurity firm PRODAFT revealed that Black Basta, also known as Vengeful Mantis, has been relatively inactive in early 2025 due to significant internal strife. Some members reportedly scammed victims by taking ransom payments without providing decryption keys. This fraudulent behaviour caused major rifts within the organization, with several high-ranking members defecting to rival ransomware groups, such as CACTUS (Nurturing Mantis) and Akira.
According to PRODAFT, the infighting was largely fueled by an individual known as Tramp (LARVA-18), a cybercriminal operating a vast spam network responsible for distributing QBot. His actions contributed to Black Basta’s instability, leading to fragmentation within the group.
Key Figures Exposed in the Leaked Chats
The leaked chat logs, which contain nearly 200,000 messages, reveal important details about Black Basta’s internal hierarchy. Some key figures include:
- Lapa – One of the main administrators handling internal operations.
- YY – Another key administrator responsible for support tasks.
- Trump – Alias for Oleg Nefedov, who also goes by GG and AA, and is considered the primary leader of Black Basta.
- Cortes – Connected to the QakBot group, which has distanced itself following Black Basta’s controversial attacks on Russian banks.
- Bio – Worked alongside Trump in the now-disbanded Conti ransomware group.
- A 17-year-old affiliate – The leak suggests that at least one of Black Basta’s members is a minor actively participating in cybercriminal activities.
Furthermore, Black Basta has begun incorporating social engineering tactics into their ransomware campaigns. This shift appears to be inspired by the success of Scattered Spider, a cybercriminal group known for its effective use of social manipulation techniques.
How Black Basta Executes Attacks
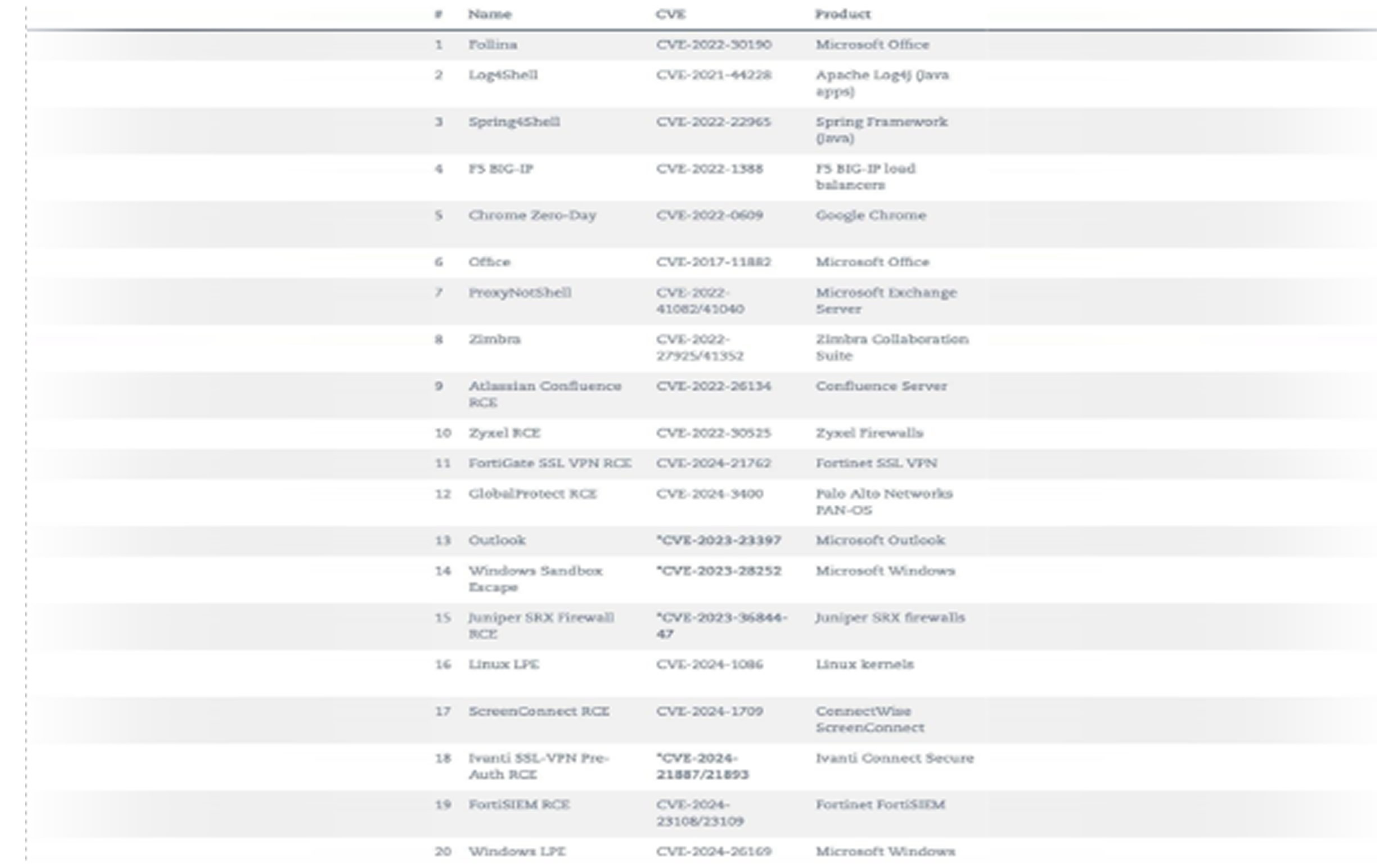
According to Qualys, Black Basta exploits known vulnerabilities, system misconfigurations, and weak security protocols to gain access to target networks. The leaked discussions indicate that their primary attack methods include:
- Exploiting misconfigured SMB services.
- Taking advantage of exposed RDP servers.
- Using default VPN credentials and brute-force attacks to obtain login details.
- Deploying malware droppers to infiltrate systems with ransomware.
To evade detection, Black Basta has been observed using legitimate file-sharing platforms like transfer.sh, temp.sh, and send.vis.ee to host malicious payloads.
“Ransomware groups are accelerating their attacks once they breach an organization’s network,” said Saeed Abbasi, Manager at Qualys Threat Research Unit (TRU). “Recent data from Black Basta indicates that they are moving from initial access to full network compromise within hours—or even minutes.”
Cl0p Ransomware Resurgence & Global Cybercrime Threats
Meanwhile, another notorious ransomware group, Cl0p, has resurfaced with renewed attacks. According to Check Point’s Cyberint Research Team, Cl0p has begun listing breached organizations on its data leak site after exploiting a newly disclosed vulnerability (CVE-2024-50623) in Cleo’s managed file transfer software.
The group has taken an aggressive approach, directly contacting victims and providing secure chat links for negotiations. “If companies ignore their demands, Cl0p threatens to expose their full names within 48 hours,” Check Point warned in a recent update.
U.S. Cybersecurity Agencies Warn About Ghost Ransomware
In a separate development, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about the Ghost ransomware group, which has been targeting organizations across more than 70 countries, including China.
Ghost actors have been observed modifying their ransomware payloads, altering file extensions of encrypted files, and updating ransom notes. This has led researchers to refer to them by different names, including Cring, Crypt3r, Phantom, Strike, Hello, Wickrme, HsHarada, and Rapture.
According to CISA, Ghost ransomware actors have been active since early 2021, exploiting outdated software and firmware to gain access to networks. Their victims include:
- Critical infrastructure sectors.
- Educational institutions (schools and universities).
- Healthcare organizations.
- Government agencies.
- Technology and manufacturing firms.
- Small- and medium-sized businesses.
- Ghost’s Attack Methods and Tools
- Ghost actors exploit well-known vulnerabilities in multiple systems, including:
- Adobe ColdFusion (CVE-2009-3960, CVE-2010-2861).
- Fortinet FortiOS appliances (CVE-2018-13379).
- Microsoft Exchange Server (CVE-2021-34473, CVE-2021-34523, CVE-2021-31207 – also known as ProxyShell).
Upon gaining access, attackers deploy web shells to install and execute the Cobalt Strike framework, a powerful penetration testing tool frequently abused by cybercriminals. The group also uses credential-harvesting tools like Mimikatz and BadPotato for privilege escalation.
“Ghost actors utilize elevated privileges and Windows Management Instrumentation Command-Line (WMIC) to run PowerShell commands on additional systems,” CISA stated. “In cases where lateral movement attempts fail, they have been known to abandon attacks altogether.”


