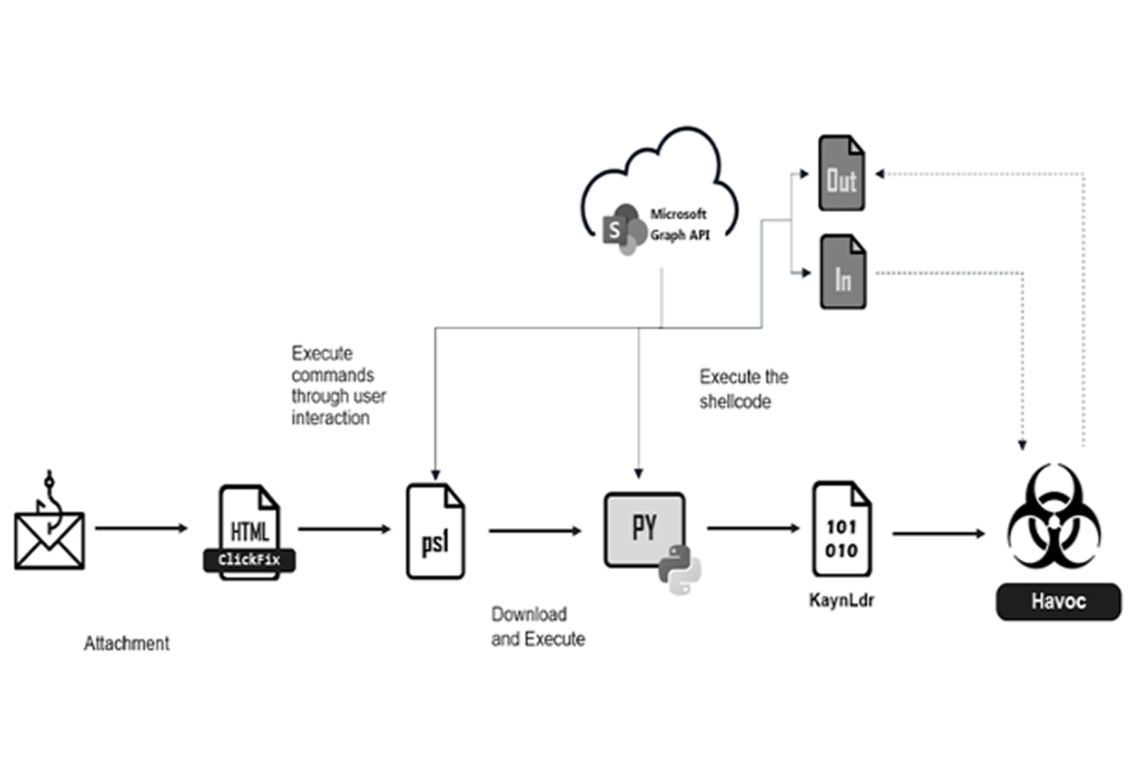
Cybersecurity researchers have identified a new phishing campaign that leverages the ClickFix technique to deliver
the open-source command-and-control (C2) framework, Havoc.
According to a report from Fortinet FortiGuard Labs, the attackers conceal each stage of the malware behind a SharePoint site while using a modified version of the Havoc Demon agent. They also integrate the Microsoft Graph API to disguise C2 communications within trusted and widely used services.
The attack starts with a phishing email containing an HTML attachment labeled “Documents.html.” When opened, the file displays an error message that employs the ClickFix trick to manipulate users into copying and executing a malicious PowerShell command. Once executed, the command downloads and runs a PowerShell script from a compromised SharePoint server.
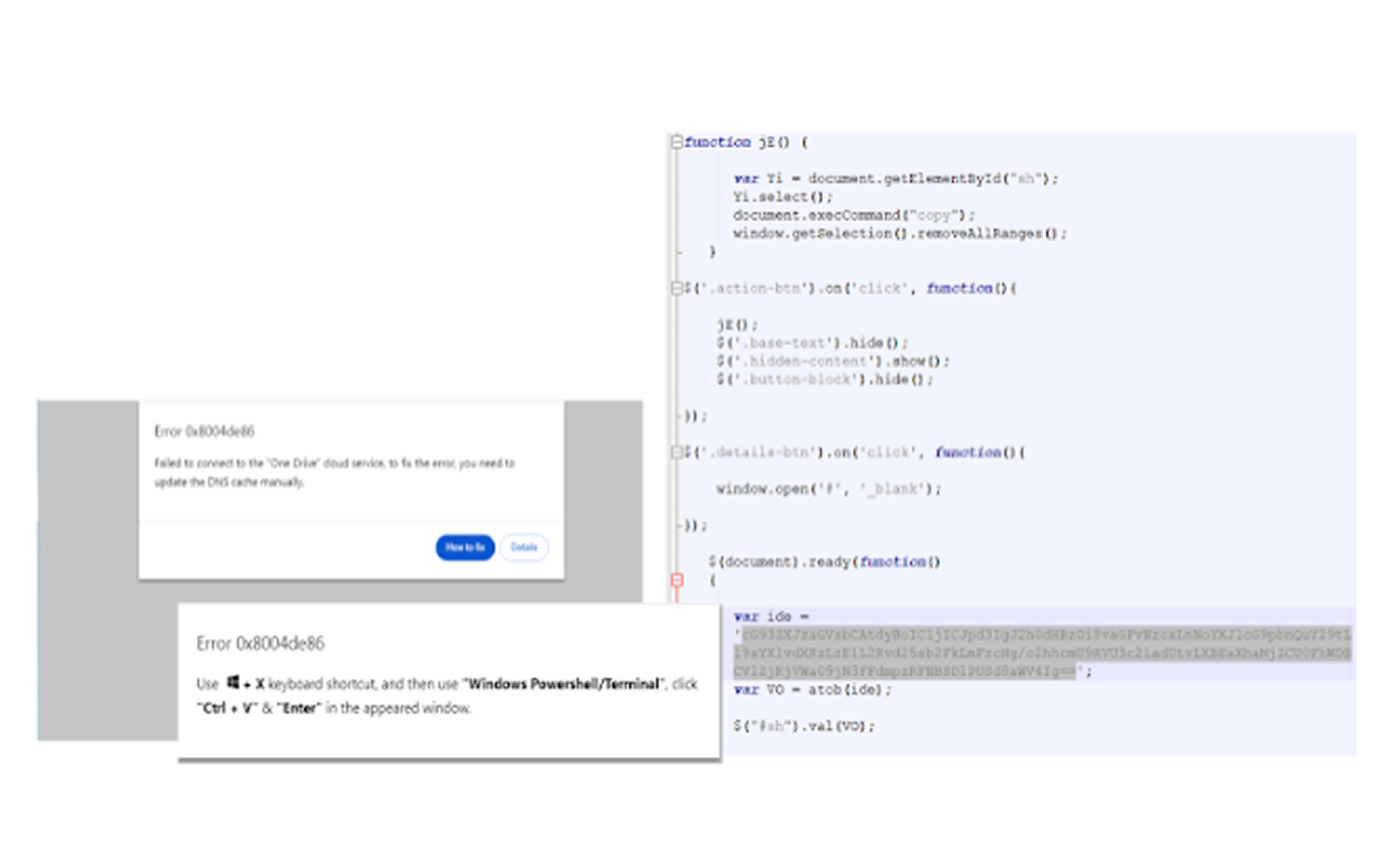
Before proceeding, the script checks whether it is running in a sandboxed environment. If not, it downloads the Python interpreter ("pythonw.exe") if it is not already installed on the system. Next, a Python script is retrieved and executed from the same SharePoint server, acting as a shellcode loader for KaynLdr—a reflective loader written in C and assembly. This loader is designed to launch an embedded DLL, in this case, the Havoc Demon agent, on the compromised system.
Fortinet notes that by utilizing the Microsoft Graph API, attackers effectively obscure C2 traffic within legitimate services. The Havoc framework enables threat actors to execute commands, collect system information, manipulate tokens, perform file operations, and even launch Kerberos attacks.
This development follows recent findings from Malwarebytes, which revealed that cybercriminals are continuing to exploit vulnerabilities in Google Ads policies. Attackers have been impersonating PayPal through fraudulent ads, tricking users searching for help with account or payment issues into calling fake support numbers, ultimately leading to the theft of personal and financial information.
According to Jérôme Segura, Senior Director of Research at Malwarebytes, the loophole in Google’s policies allows scammers to create deceptive ads by using misleading final URLs. This enables cybercriminals to impersonate well-known brands while directing victims to malicious landing pages. Segura noted that scammers actively target high-traffic search terms, particularly those related to customer service and online assistance.