Hackers Exploiting Remote Monitoring Software for Network Infiltration and Persistence
Cybersecurity experts have identified a growing trend in which threat actors exploit legitimate Remote Monitoring and Management (RMM) software to infiltrate networks, maintain persistent access, and move laterally across compromised systems.
RMM tools, commonly used by IT administrators for system maintenance and support, provide attackers with powerful capabilities that evade traditional security measures due to their trusted status within enterprise environments. Among the most frequently misused RMM applications are AnyDesk, TeamViewer, ScreenConnect, Quick Assist, and Splashtop. These tools are widely deployed for software updates, asset management, and endpoint troubleshooting, making it difficult to distinguish between legitimate and malicious usage.
How Attackers Gain Access to RMM Software
According to Intel471 analysts, cybercriminals initially gain access to RMM tools by:
- Compromising user credentials through social engineering tactics.
- Exploiting vulnerabilities in outdated software.
Once inside the system, attackers often create additional accounts within the RMM platform to ensure persistence, even if compromised credentials are reset.
One particularly concerning technique involves attackers impersonating IT support personnel. In a documented case, cybercriminals flooded an employee’s inbox with spam, then called the victim pretending to be internal IT support, offering to install “anti-spam software.” The unsuspecting employee was then tricked into installing a remote access tool like AnyDesk, unknowingly granting full system access to the attackers.
The Black Basta ransomware group, one of the most significant ransomware operations since its emergence in April 2022, has been regularly using RMM tools as part of its attack chain. Leaked chat messages from February 2025 confirm that the Russian-speaking cybercrime group has integrated RMM software into its tactics for gaining and maintaining unauthorized access.
Detecting Malicious RMM Usage
To identify suspicious RMM deployments, security teams can analyze execution patterns. One effective method involves scanning for process executions of RMM tools like "AnyDesk.exe" in unusual locations, excluding legitimate directories like AppData, Downloads, and Program Files.
Running these queries against Sysmon logs can help detect hidden RMM installations in locations like the Public Music directory, a tactic frequently used by attackers to avoid detection.
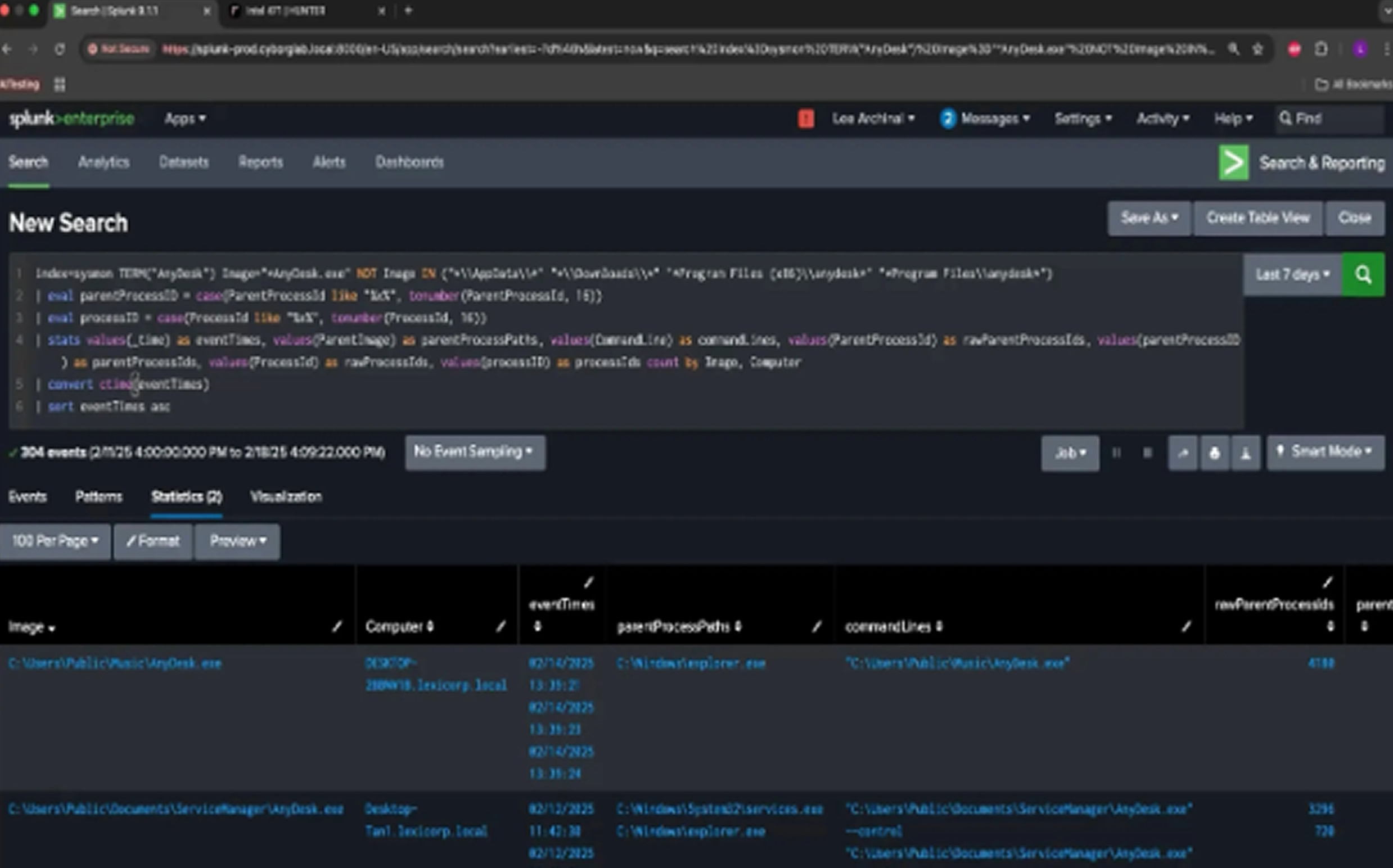
To mitigate the risks associated with malicious RMM usage, Intel471 recommends organizations implement:
- Strict application control policies to regulate RMM software use.
- Continuous monitoring of network connections for signs of unauthorized command and control (C2) traffic.
- Regular security awareness training to help employees identify social engineering attacks.
As cybercriminals increasingly weaponize trusted enterprise tools, organizations must enhance their detection strategies and enforce strong security policies to prevent unauthorized access and system compromise.


