Hackers Exploit PHP Vulnerability to Deploy Cryptocurrency Miners and Remote Access Trojans
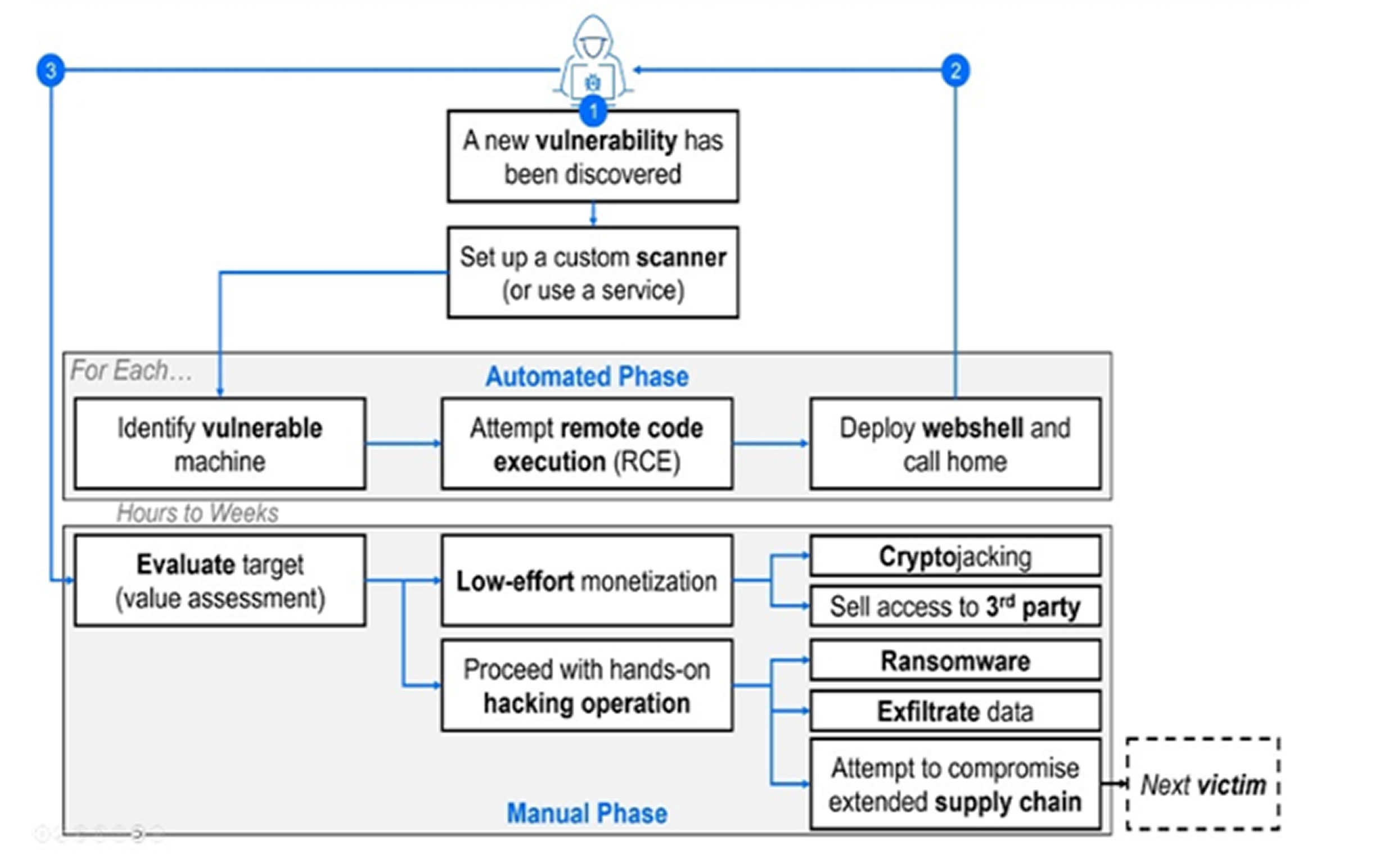
Cybercriminals are actively exploiting a severe security flaw in PHP, tracked as CVE-2024-4577, to distribute cryptocurrency miners and remote access trojans (RATs) such as Quasar RAT.
The vulnerability affects Windows-based systems running PHP in CGI mode and allows remote attackers to execute arbitrary code. According to cybersecurity firm Bitdefender, exploitation attempts have surged since late 2024, with a majority of attacks targeting Taiwan (54.65%), Hong Kong (27.06%), Brazil (16.39%), Japan (1.57%), and India (0.33%).
Bitdefender’s analysis found that 15% of the detected attacks involved basic vulnerability checks, using commands like "whoami" and "echo <test_string>". Another 15% were focused on system reconnaissance, gathering information about processes, networks, users, and domains.
Approximately 5% of attacks resulted in the deployment of XMRig, a popular cryptocurrency miner used in cryptojacking operations. In a related campaign, attackers deployed NiceHash miners, disguising the malicious process as legitimate applications like "javawindows.exe" to evade detection.
Other exploitation attempts delivered remote access tools such as Quasar RAT or executed malicious Windows installer (MSI) files from external servers using cmd.exe.
In a bizarre twist, Bitdefender observed attackers modifying firewall configurations on compromised servers to block access to known malicious IPs associated with the exploit.
This unusual behavior suggests that rival cryptojacking groups are competing for control over vulnerable systems, preventing other hackers from re-infecting machines they already control. Similar tactics have been observed in the past, where cryptojacking malware terminates rival miner processes before deploying its own payload.
The discovery follows a recent report from Cisco Talos, which uncovered a campaign targeting Japanese organizations using the same PHP vulnerability. The increasing number of attacks highlights the growing threat to servers running outdated PHP versions.
Security experts urge organizations to update PHP installations immediately to patch the vulnerability. Additionally, Bitdefender’s technical solutions director Martin Zugec recommends limiting the use of Living Off the Land (LOTL) tools such as PowerShell to only privileged users like system administrators.
As threat actors continue to weaponize critical software vulnerabilities, organizations must remain vigilant by applying security patches, monitoring unusual network activity, and restricting the use of powerful administrative tools.


