Authentication Coercion Remains a Major Threat to Windows Environments in 2025
Windows authentication coercion attacks continue to pose significant risks to enterprise Active Directory environments in 2025, despite Microsoft's ongoing security updates. These attacks allow low-privileged threat actors to escalate privileges and potentially compromise entire networks within hours of gaining a foothold.
Exploiting Core Windows Services
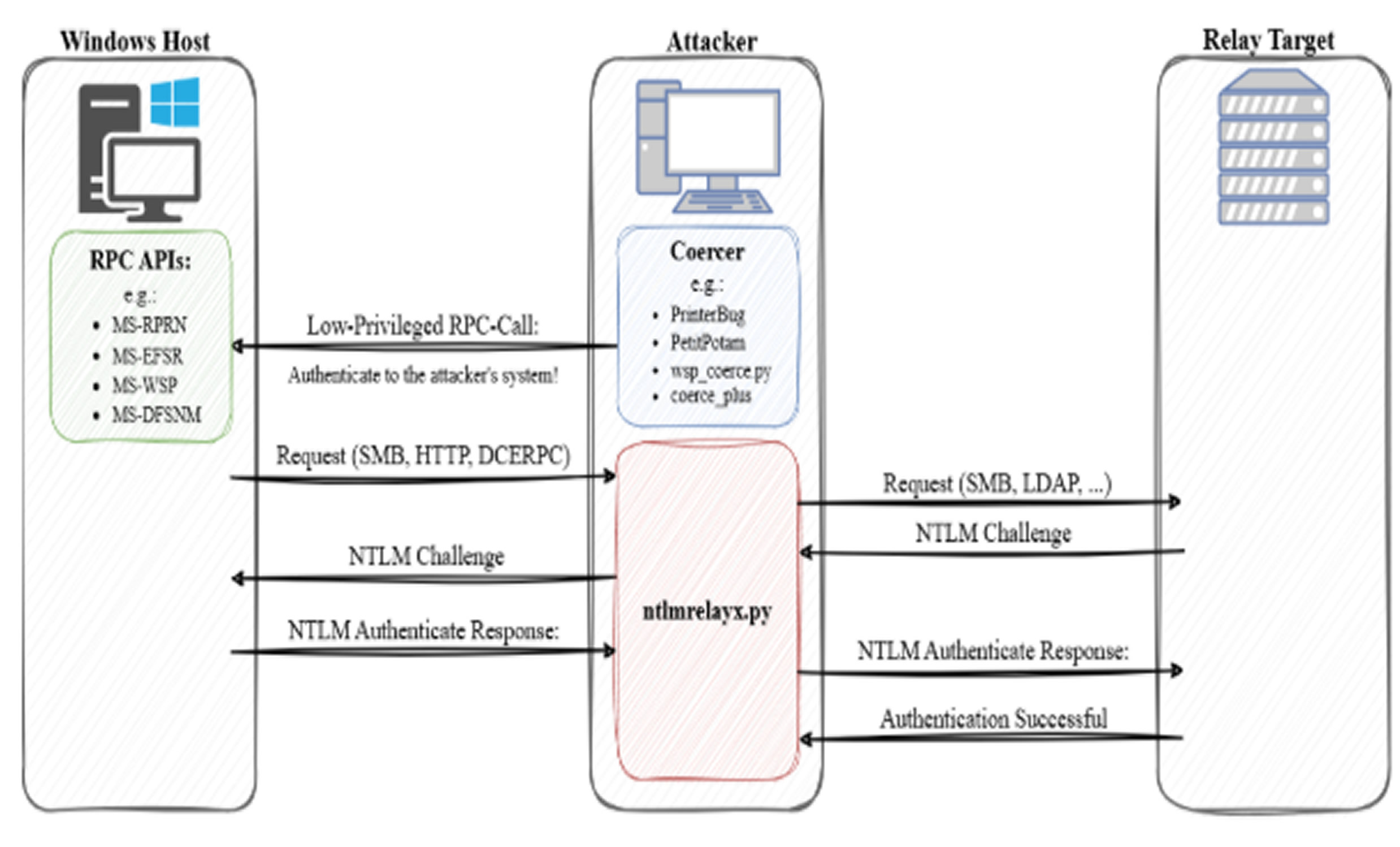
As detailed by RedTeam Pentesting, these attacks use Remote Procedure Call (RPC) interfaces to coerce Windows machines into authenticating with attacker-controlled systems. Key techniques include MS-RPRN (PrinterBug), MS-EFSR (PetitPotam), MS-DFSNM (DFS Coercion), and MS-WSP (WSP Coercion).
Each method manipulates legitimate services to force systems to initiate connections, which attackers then intercept and relay to privileged targets. MS-RPRN remains especially dangerous due to its widespread availability on standard Windows installations.
Updated attack tools like ntlmrelayx.py now support RPC server features, allowing attackers to maintain effectiveness even when traditional SMB and HTTP paths are blocked.
MS-EFSR attacks have seen limited mitigation in Windows Server 2022 23H2, which introduces on-demand activation for the relevant service. However, attackers can still trigger it through tools like NetExec’s efsr_spray, which attempts to encrypt files via SMB shares, including print queues.
Security Measures and Their Limitations
Microsoft has responded with protections such as Extended Protection for Authentication (EPA), LDAP channel binding, and mandatory SMB signing. These enhancements appear in recent versions like Windows Server 2022 23H2 and Windows 11 24H2.
However, these features often apply only to clean installations. Upgraded systems may retain legacy configurations that leave them vulnerable. One example is the WebClient service, a common attack vector, which can still be exploited through specially crafted .searchConnector-ms files on shared drives.
The persistence of coercion attacks is tied to the strength of computer accounts. These accounts can impersonate users through techniques like S4U2Self abuse and Resource-Based Constrained Delegation (RBCD). If attackers target a domain controller account, they can obtain DCSync capabilities, allowing them to extract credentials for every user in the domain.
An Ongoing Challenge for Defenders
As Microsoft moves to phase out NTLM authentication, attackers are shifting focus toward Kerberos relaying and coercion. Enterprise security teams face difficulties in fully applying all the necessary protections due to the complexity and variation of Windows environments.
Experts stress that until every Windows service enforces strong signing and secure channel binding, authentication coercion will remain a serious and urgent security threat for enterprises around the world.
Found this article interesting? Follow us on X(Twitter) ,Threads and FaceBook to read more exclusive content we post.



