A sophisticated malware campaign targeting Android TV devices has rapidly spread across multiple countries, with Brazil, South Africa, Indonesia, Argentina
Vo1d Botnet Expands, Infecting Over 1.59 million Android TVs Across 226 Countries
A sophisticated malware campaign targeting Android TV devices has rapidly spread across multiple countries, with Brazil, South Africa, Indonesia, Argentina, and Thailand among the primary victims. The botnet, known as Vo1d, has significantly evolved, enhancing its stealth and resilience while evading detection.
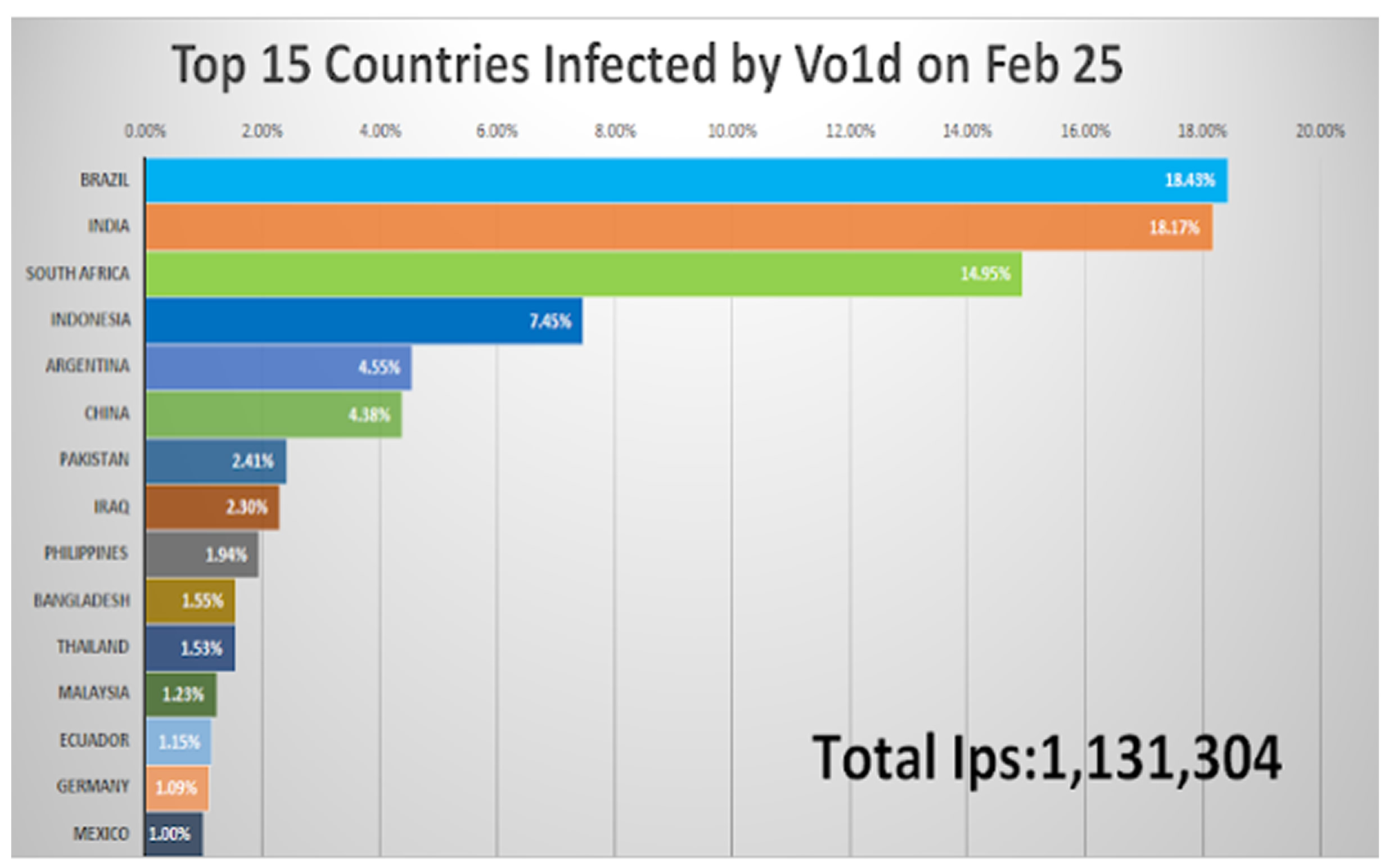
At its peak on January 19, 2025, Vo1d infected 1,590,299 Android TVs worldwide, with 800,000 daily active IP addresses. The infection rate in India has surged dramatically, rising from just 3,901 devices to 217,771—an 18.17% share of the total infections as of February 25, 2025.
Advanced Capabilities and Infection Methods
Security researchers at QiAnXin XLab revealed that Vo1d utilizes RSA encryption to secure network communications, preventing command-and-control (C2) takeover by researchers. Each malware payload is delivered through a unique downloader with XXTEA encryption and RSA-protected keys, making analysis and mitigation challenging.
Originally discovered by Doctor Web in September 2024, Vo1d primarily affects Android-based TV boxes through a backdoor that allows remote execution of additional malicious files. Although the precise method of compromise remains unclear, researchers suspect supply chain attacks or unofficial firmware versions with pre-installed root access.
Google’s Response and Large-Scale Cyber Operations
Google previously clarified that the infected TV models were uncertified, "off-brand" Android devices using open-source Android code instead of Google-certified Play Protect security. The latest iteration of Vo1d indicates an expansion in scale, with evidence suggesting its use in proxy networks, ad fraud, and other illicit activities.
QiAnXin XLab theorizes that Vo1d operates under a "rental-return" model, where cybercriminals lease infected devices for specific time periods to conduct illegal operations before they are reintegrated into the larger botnet.
Technical Breakdown of Vo1d Malware
Analysis of the ELF malware variant (s63) reveals a multi-stage infection process:
- First Stage: The malware downloads, decrypts, and executes a secondary payload, which establishes C2 communications.
- Second Stage: A decrypted package (ts01) contains four key files—install.sh, cv, vo1d, and x.apk.
- The shell script executes the cv component, which subsequently launches vo1d and installs the malicious Android app.
- vo1d Module: Loads a backdoor to communicate with the C2 server and download a native library.
Redirector C2 Implementation: This update improves network communication by introducing a secondary layer, which redirects infected devices to the actual C2 server.
The Android malware disguises itself as "com.google.android.gms.stable", mimicking the legitimate Google Play Services package to evade detection. It achieves persistence by running at system startup and launching additional malicious components.
The Mzmess Modular Malware Suite
The Vo1d botnet also facilitates the deployment of Mzmess, a modular Android malware that operates using four different plugins:
- Popa ("com.app.mz.popan") – Proxy services
- Jaguar ("com.app.mz.jaguarn") – Proxy services
- Lxhwdg ("com.app.mz.lxhwdgn") – Function unknown (C2 server offline)
- Spirit ("com.app.mz.spiritn") – Ad fraud and traffic inflation
Potential for Large-Scale Cyber Threats
While Vo1d is currently used for financial gain, researchers warn that attackers could leverage its full control over infected devices for large-scale cyberattacks, including:
DDoS Attacks – Overwhelming online services with massive traffic
Illegal Content Distribution – Broadcasting unauthorized content through compromised devices
Expansion of Cybercriminal Networks – Selling access to infected devices on the dark web
As the botnet continues to evolve, cybersecurity experts emphasize the need for stronger firmware security, robust threat monitoring, and stricter regulations for uncertified Android devices to mitigate further infections.


